Dozens of Global Companies in Aviation, Defense, Engineering, and More Breached via Infostealer Credentials
- Attack Vector: Access to 50 companies' cloud storage portals (ShareFile, Nextcloud, OwnCloud) is auctioned using infostealer-harvested credentials.
- Root Cause: The breaches were enabled by a combination of infected employee devices and the lack of multi-factor authentication.
- Affected Sectors: Alleged victims include aviation (Iberia Airlines), defense (Intecro Robotics), engineering (Pickett & Associates), and government infrastructure (CRRC MA).
A threat actor using the aliases "Zestix" and "Sentap" is auctioning access to the corporate cloud file-sharing instances of dozens of global enterprises. The campaign abuses a common cloud security gap, leveraging credentials stolen via infostealers used against portals without MFA.
The actor is not using sophisticated exploits but rather logging in directly with valid usernames and passwords. This infostealer cloud credential breach has exposed terabytes of sensitive data from victims across the aviation, defense, finance, and healthcare sectors, highlighting a pervasive and preventable security failure.
Infostealer Credentials and MFA Lapses
The exfiltrated data includes intellectual property, aircraft maintenance programs, defense project blueprints, patient health information (PHI), and sensitive client litigation strategies, a recent report from Infostealers by Hudson Rock said. The scale of this corporate data compromise is extensive, impacting companies like:
- Iberia Airlines (iberiaexpress.sharefile.com) – Breach point identified via an employee login: technical safety and confidential fleet data.
- CRRC MA (ltk-lametro.sharefile.com) – LA Metro HR4000, security info, blueprint exposure.
- Intecro Robotics, Turkey (fileshare.intecro.com.tr) – Critical military intellectual property: defense projects, ITAR controlled data.
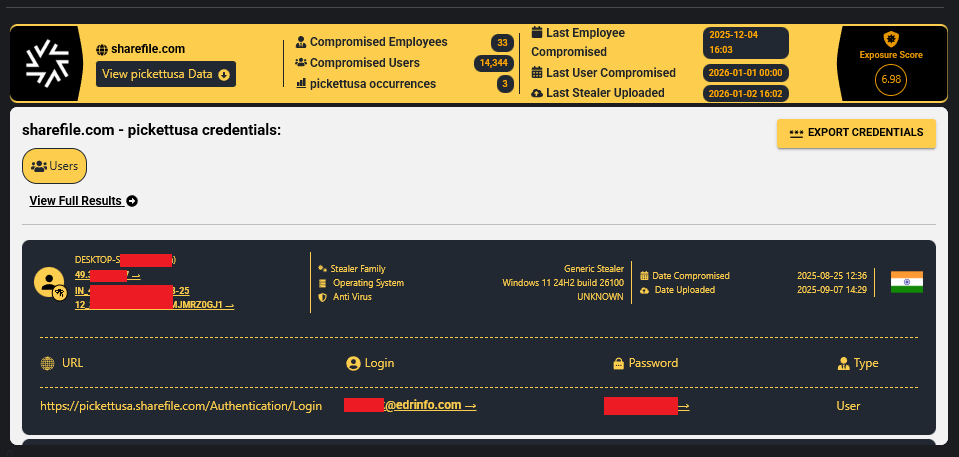
- Pickett & Associates (pickettusa.sharefile.com) – 800+ classified LiDAR files covering transmission line corridors and substations, operational blueprints.
- Burris & Macomber (Mercedes-Benz Counsel) – National Coordinating Counsel for Mercedes-Benz USA: litigation strategy, customer data, corporate secrets.
- Maida Health, Brazil (nextcloud.maida.net) – Health records of the Brazilian Military Police with sensitive PII, medical records.
- K3G Solutions (owncloud.k3gsolutions.com.br) – Over 724,000 files with network configs.
- IFLUSAC, Brazil – 22 GB of engineering and business data.
- GreenBills – Over 111,000 PDF files pertaining to real patients (2020-2023)..
- CiberC – 95,000+ files including monthly project tracking reports for government contracts.
The investigation reveals that these security failures stem from a dual cause:
- Employee devices becoming infected with infostealers (such as RedLine, Lumma Stealer, or Vidar)
- A subsequent failure by the targeted organizations to enforce multi-factor authentication (MFA) on their cloud portals.
The malware harvests credentials saved in browsers, which are then aggregated and sold. In many cases, the stolen credentials had been sitting dormant in malware logs for years, representing a long-standing, unaddressed risk.
This campaign underscores that without MFA, stolen passwords provide a direct and unimpeded path to an organization's most sensitive data repositories.
A Global Cybersecurity Threat
This campaign serves as a stark reminder of the far-reaching impact of Infostealer malware, transforming individual employee infections into major corporate and even national security incidents.
The findings emphasize the urgent need for organizations to mandate MFA and gain visibility into compromised credentials originating from outside the traditional corporate network perimeter.
In November, Stolen Police logins raised security concerns regarding Flock Safety surveillance cameras, as 35 customer passwords leaked.