Digital Transformation Risks: Critical Governance Gaps in Cloud Migration Impact 40% of Organizations in 2025
Key Takeaways
- Automation lag: Over 70% of organizations lack automation for critical access governance processes like risk analysis and user provisioning.
- Insider threat reality: Nearly 40% of reported incidents were confirmed or suspected to stem from governance gaps created during transformation.
- Delayed revocation: More than half of organizations take longer than 24 hours to de-provision terminated users.
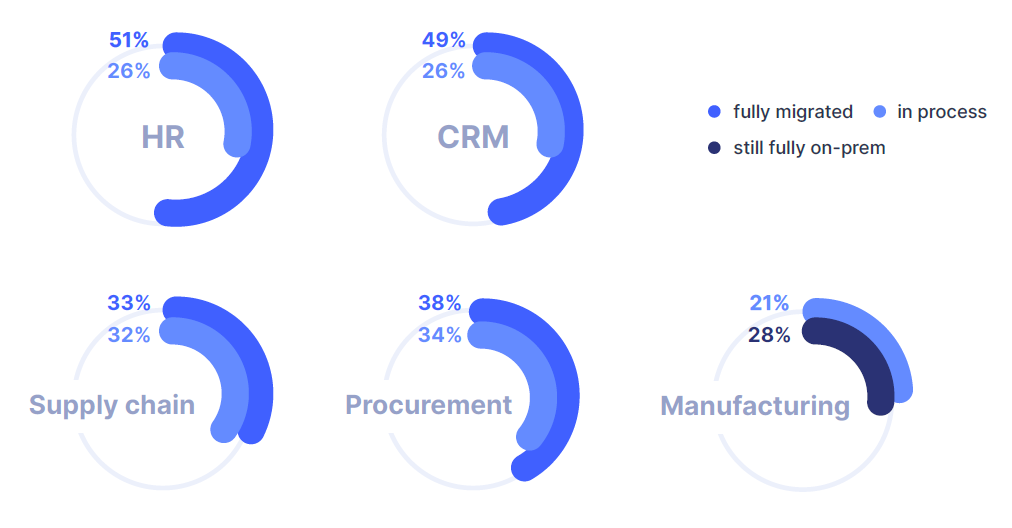
A significant disconnect was observed between the pace of cloud adoption and the implementation of necessary security controls. As organizations migrate core business functions to the cloud, such as Finance, HR, and Supply Chain, governance processes are failing to keep up.
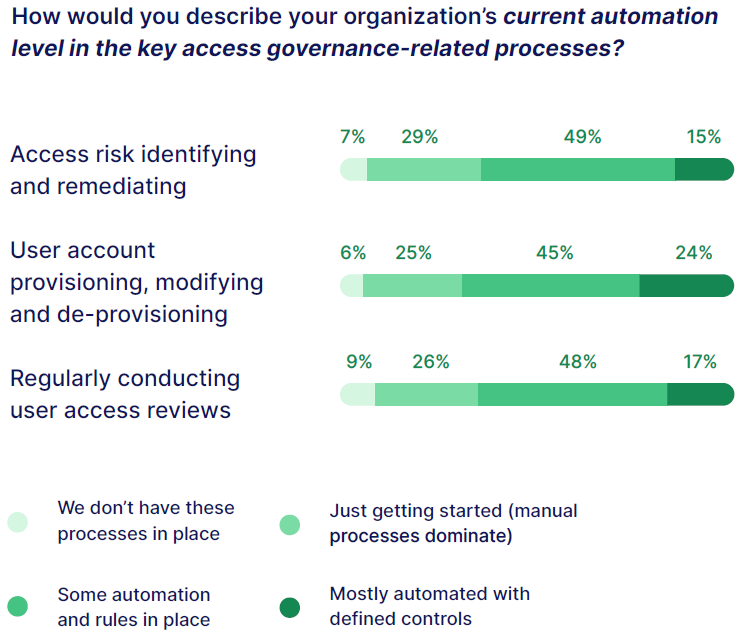
Over 70% of respondents reported a lack of automation in access risk analysis and user access reviews (UARs), creating blind spots that can be exploited.
Governance Gaps and Insider Threat Risks
The 2025 Digital Transformation report released by Pathlock, which surveyed 620 decision-makers globally, found that while cloud adoption for critical functions like SAP S/4HANA is outpacing ECC, access governance risks remain dangerously high due to a reliance on manual processes.
A major finding of the report concerns the misalignment of Governance, Risk, and Compliance (GRC) strategies during migration. Alarmingly, 52% of organizations do not plan GRC controls (e.g., SoD rules, access policies, certifications) early in their migration projects, often addressing them reactively after go-live.
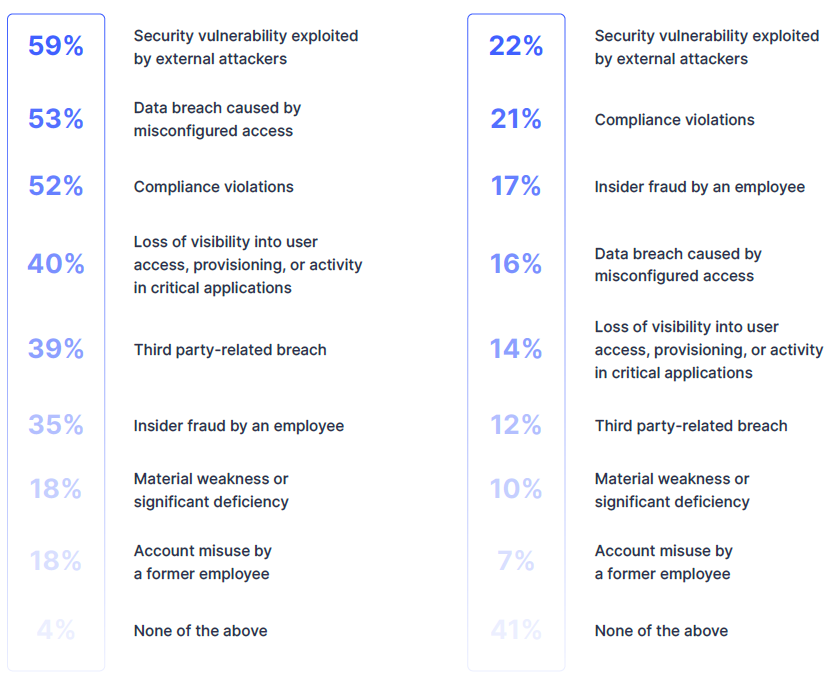
This oversight contributes directly to cloud migration challenges, particularly regarding insider threats. While external vulnerabilities are often the primary fear, the data reveals that nearly one in four organizations experienced an incident involving an insider during or shortly after a migration project.
These insider threat risks are exacerbated by poor role design, with 42% of organizations admitting to taking shortcuts like reusing legacy roles without proper Segregation of Duties (SoD) simulations.
Access De-provisioning Latency
The report also sheds light on critical operational failures in identity lifecycle management. Despite the industry benchmark of revoking access within 24 hours of termination, 51% of organizations take longer than this standard timeframe to de-provision users.
This latency leaves a window of opportunity for unauthorized access to sensitive systems. Furthermore, 60% of organizations lack automated management for elevated access, with every fifth organization granting privileged access without monitoring usage.
The report concludes that without embedding automated GRC controls from day one, digital transformation initiatives risk becoming sources of material business liability rather than drivers of growth.
Teresa Rothaar, Governance, Risk and Compliance Analyst at Keeper Security, and Tim Zimmerman, Manager, Information Security at Cowbell, back the idea that shifting to the cloud without strong governance creates visibility and control gaps.
“Building it into every stage of digital transformation helps teams avoid costly incidents, maintain accountability, and stay resilient as their environments evolve,” Rothaar stated.
Sectigo’s Jason Soroko recommends:
- Making offboarding a hard service goal with a 1-day window
- Issuing privileged access only when needed and for a limited time, with logging and automatic removal.
- Simulating segregation conflicts before roles hit production and block promotion if conflicts remain.
- Replacing periodic mass attestations with change-driven checks tied to job moves, project end dates, and vendor exits.
- Tracking leading indicators like mean time to revoke, orphaned accounts, and the sharing of elevated sessions that are monitored.
An October report also underlined that cloud adoption outpaces security readiness. Crystal Morin, Senior Cybersecurity Strategist at Sysdig, explained in an interview with TechNadu how defenders can secure cloud-native environments.