The Dharma Ransomware Abuses ESET to Go Undetected
- The Dharma ransomware tries to divert the victim’s attention by using an old ESET tool.
- While the user is dealing with the installation of the ESET Remover, Dharma runs in the background.
- There’s nothing that can be done about this by ESET, and users just have to be careful with what they download.
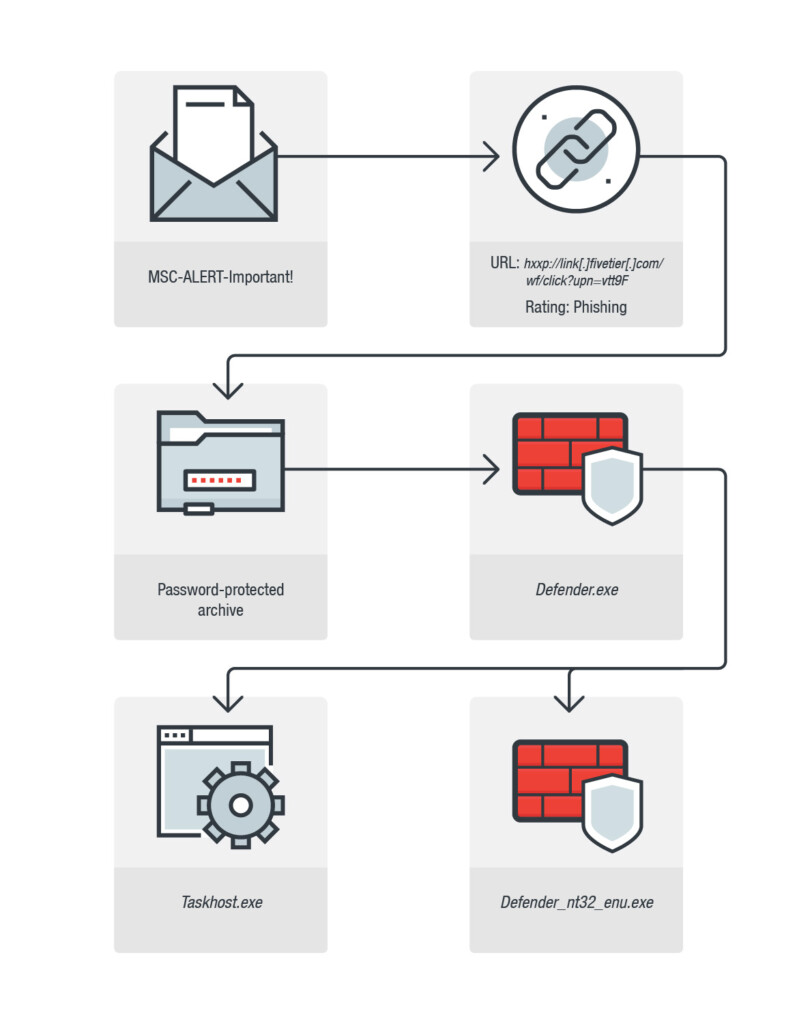
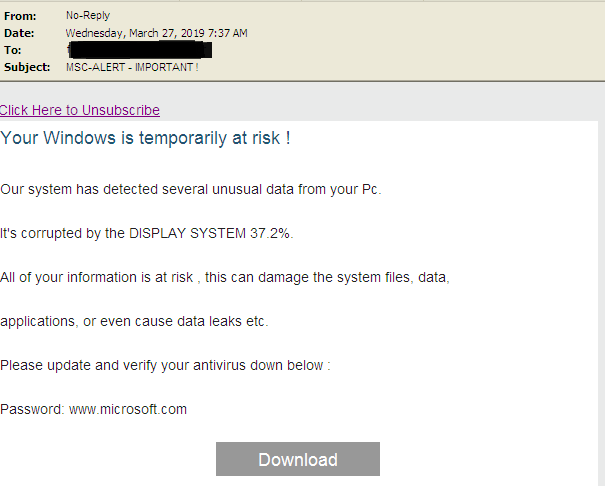
Dharma ransomware keeps going for the third year, and as expected, it is continuously updated and enriched with more tricks up its sleeve. According to a report by Trend Micro researchers, the newest samples of the Dharma ransomware is still passed around via spam email, but they are now urging the recipient to download a seeming innocuousness file named “Defender.exe”. The particular file is actually an archive, so when the victim executes it, it extracts and drops a malicious file named “taskhost.exe” and an old application remover of the ESET antivirus. To make things a little more believable, the archive is password protected, and the password is “www.microsoft.com”.
image source: blog.trendmicro.com
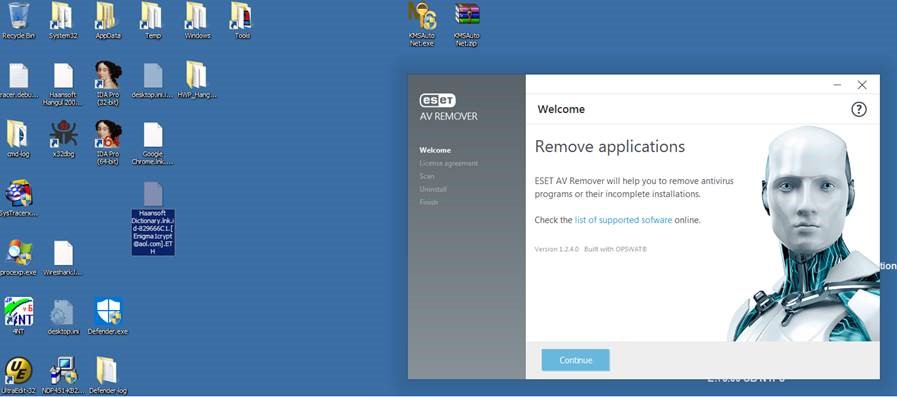
The main idea for the malicious actors is to draw the victim’s attention to the supposed removal of the applications that allegedly cause the “display system corruption”, and since people see a familiar ESET branding and GUI, they are less likely to suspect that something shady is going on in their system. Unfortunately, there is, as while the ESET Remover is installed in the system, the Dharma tool is encrypting the victim’s files in the background. No matter whether people will actually install the ESET tool or not, the Dharma will start its encrypting activities upon the extraction of the Defender archive.
image source: blog.trendmicro.com
The whole point of doing all this bundling of the malware in the ESET tool is to make the capturing of system processing resources seem legit. If the victim proceeds to install the ESET Remover and then try to figure out what they are supposed to do with it, they will waste precious time, allowing the encrypter to do its thing for at least a couple of minutes. There’s no way for ESET to do something about this, although they are aware that their tool is being used for malicious purposes. As always, it all boils down to the user.
image source: blog.trendmicro.com
Don’t download and execute files that accompany unsolicited email messages, back up your valuable files frequently, and keep your AV tools up to date. Even if the attached files are named “defender” or “protector”, or “malware-remover”, it most certainly isn’t. If you are not sure about the claims, pay attention to the content of the message. In this case, the spam claims a “corruption by the DISPLAY SYSTEM 37.2%”. This alone should be enough to convince you that the message is directed to people who don’t understand anything about how computers work. If you are one of those people, consider all claims false by default, and just get on with your day.
Would you fall for this? Let us know what you think in the comments down below, and help us spread the word of caution by sharing this post through our socials, on Facebook and Twitter.