Decade-Old Pixie Dust Exploit Risk Persists in Modern Wireless Firmware, Report Says
- Old flaw exploit: The decade-old Pixie Dust exploit still impacts current wireless network devices with vulnerable firmware as of 2025.
- Exploit analysis: The new report focuses on operational and strategic risks this exploit presents to device manufacturers, supply chain partners, and end users.
- Vulnerable devices: It tackles devices across routers, range extenders, access points, and hybrid Wi-Fi/powerline products that remain vulnerable.
A decade-old vulnerability known as the Pixie Dust exploit continues to affect modern wireless networking equipment, with vulnerable firmware released as recently as July 2025. A new report reveals that this critical flaw, which targets Wi-Fi Protected Setup (WPS), remains a significant threat, exposing consumer and small-business networks to rapid credential compromise.
Analysis of Wireless Firmware Vulnerabilities
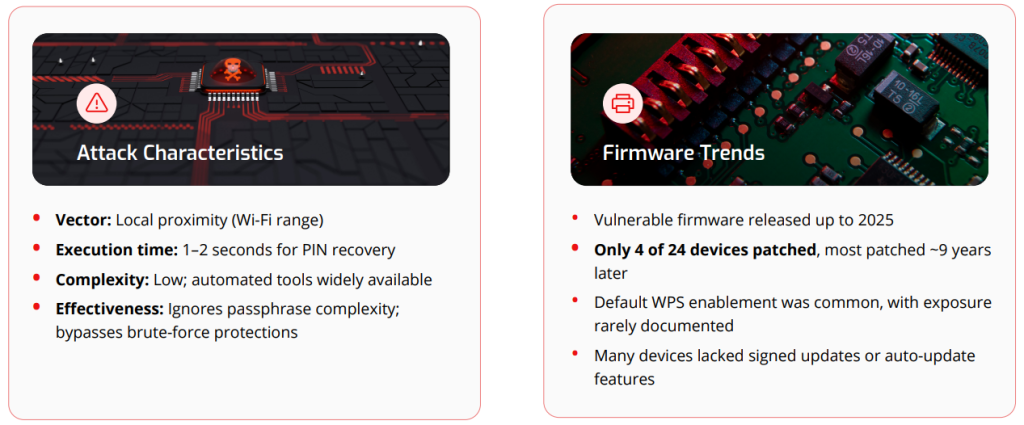
The Pixie Dust exploit leverages poor entropy in the key generation process of the WPS protocol, allowing an attacker within Wi-Fi range to recover the WPS PIN in seconds through an offline brute-force attack, a NetRise analysis says.
The report identified 24 vulnerable devices, including routers, access points, and range extenders, from six vendors.
Despite the exploit being publicly disclosed in 2014, these devices shipped with firmware that remained susceptible.
Of the 24 devices analyzed, only four ever received a patch. These fixes were severely delayed, arriving on average over nine years after the initial disclosure. As of the report's publication, 13 devices are still actively supported but unpatched, while another seven reached their end-of-life (EOL) without ever being fixed.
“Pixie Dust is more than a vulnerability. It’s a case study in how insecure defaults and weak patching processes persist in firmware,” said Thomas Pace, co-founder and CEO of NetRise. “Relying on vendor self-attestation isn’t good enough for enterprises that deploy devices such as these. Creating a comprehensive and accurate SBOM by analyzing the compiled code that’s on the device is the only way to uncover and manage risk.”
This highlights systemic issues in firmware supply chains and vendor patch management, contributing to significant WPS security risks.
Implications for IoT Cybersecurity
The persistence of the Pixie Dust exploit highlights a broader issue in IoT cybersecurity: the silent propagation of legacy vulnerabilities, which expose enterprise and home networks to low-complexity attacks that can bypass robust password policies entirely. Recommendations include:
- Disable WPS entirely on all devices unless explicitly required
- Implement firmware inventories, ensuring that vulnerable modules can be detected even when source code or vendor disclosures are unavailable
- Audit default wireless configurations across product portfolios
- Provide transparent customer advisories on unsupported legacy devices and security posture
- Adopt secure-by-default development practices with cryptographic review for inherited components
The findings serve as a critical reminder for organizations to implement comprehensive firmware analysis and inventory management to detect and mitigate such long-tail risks, as vendor transparency and timely remediation cannot be assumed.
In other news, a critical TP-Link Zero-Day flaw exposed millions of routers to full system takeover.