DarkSide Added ‘Toshiba France’ to Its Victim List but It Could Be the Last One
- Toshiba France has fallen victim to the DarkSide ransomware gang, but this could be their last victim.
- The servers of the RaaS operations have been seized, right after the crooks received almost $10 million.
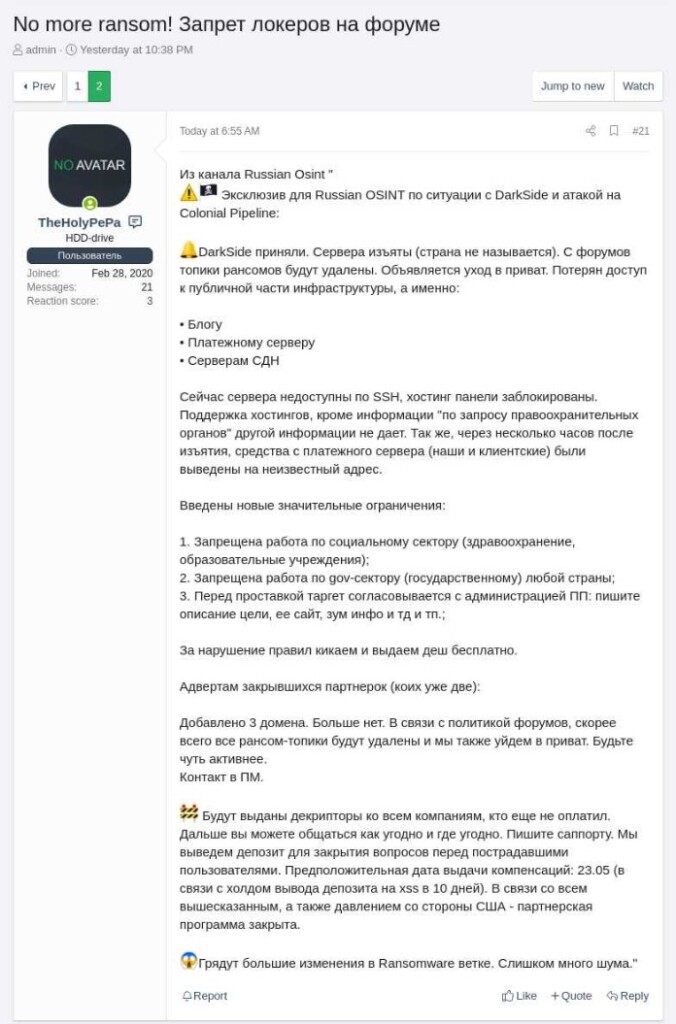
- Discussions on the dark web claim that the affiliate program is closed, and every victim will get a decrypter.
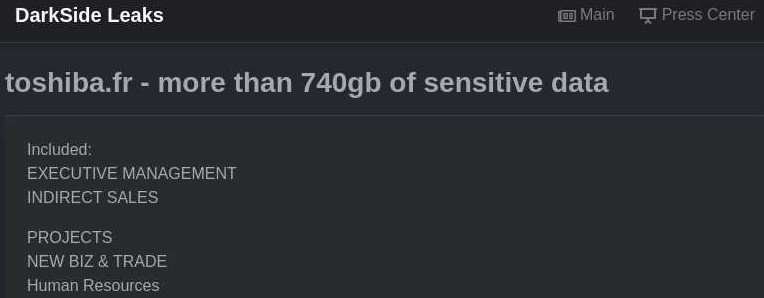
The ‘DarkSide’ ransomware gang has just added ‘Toshiba France’ to its list of victims, claiming to have stolen 740 GB of sensitive data, including executive management details, indirect sales documents, and information relevant to human resources and trade business. The leak site was showing (now offline) scans of employee VISAs and national ID cards, as well as documents relevant to projects.
Toshiba France is a central European hub of innovation, production, and provision of digital solutions services, industrial infrastructure, railway systems, heating, air conditioning, semiconductors, data storage, and a wide range of energy solutions. As a corporate entity, Toshiba is based in Tokyo, Japan, employs over 140 thousand experts, and has an annual net income of $9.235 trillion. These impressive figures are what made them a target for DarkSide, the hottest and most dangerous ransomware group right now.
Soon after that announcement, the infrastructure of DarkSide went bust, and its servers were seized. However, the negotiation site is still up, so the extortion and payment procedures should continue unabated. It is unknown if the group will experience a serious or lengthy disruption from this, but it definitely shows that when the FBI is determined to get you, they’ll get you.
In the meantime, the actors have made the astronomical amount of almost $10 million in just a couple of hours. First, Colonial Pipeline paid a ransom of $5 million to the hackers, even if they had to restore most of their systems from backups. Then, the German chemicals giant Brenntag paid another $4.4 million to DarkSide, getting the decryption key and hoping that the actors won’t leak the stolen files after all.
In the case of Toshiba, the negotiations will take the amount to a comparable level, but we don’t know what the French are planning to do. For now, the company remains silent and hasn’t decided on how to communicate the incident to the public. Maybe this is a good time for Toshiba as DarkSide is under great heat from the law enforcement authorities following the Colonial hack.
Toshiba shared a comment with Valéry Marchive of LeMagIT, saying the following:
Irina Nesterovsky, Chief Research Officer at KELA tells us:
We have searched the dark web with the help of KELA’s powerful tools, and we have found claims about the payment server being beyond access, the hosting panels being blocked, and all funds of the RaaS operators and the DarkSide members have been withdrawn to an unknown address.
This surely sounds like the authorities have taken serious action against the group, but nothing is certain yet. Also, there’s another message claiming that due to the pressure from the United States, the affiliate program is closed, and decrypters will be issued to all companies that have not paid yet. Maybe the operators are going for an exit scam, or maybe they are honest. Whatever really happened, we will get to know for sure soon.