Dark Web Sales of Government Email Addresses from the US and More Expose Global Risks
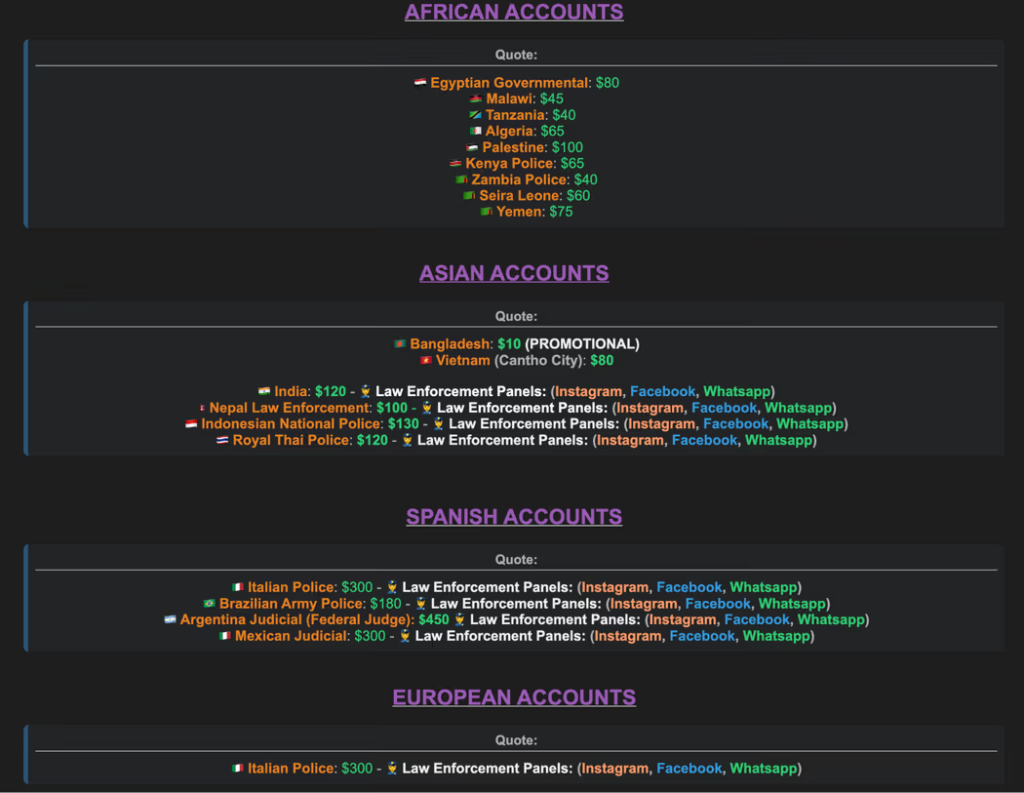
- Underground forum sale: Cybercriminals offer government and police email addresses for as low as $40.
- Why it matters: Buyers can gain access to these official accounts via credential stuffing, infostealers, or targeted phishing.
- Impacted countries: The list reportedly includes the U.S., the U.K., and India, as well as African countries.
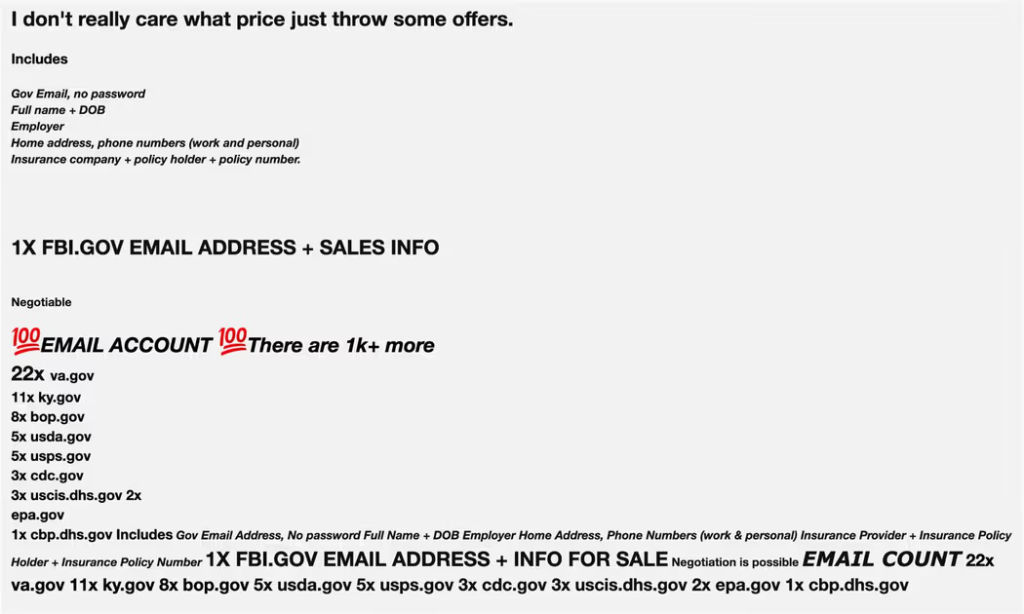
Cybercriminals are selling active law enforcement and government email addresses from the U.S., U.K., India, Brazil, Germany, and more on dark web forums, with prices starting at $40, according to a recent report from Abnormal Security.
These accounts enable attackers to exploit institutional trust, carry out fraudulent activities, and access critical systems, posing severe cybersecurity risks.
Methods of Compromise
The offers advertise the sale of details such as government email addresses, full names, dates of birth, employer, home address, work and personal phone numbers, insurance company, and policy holder and number. However, passwords are not on the list.
According to the research, attackers employ several techniques to acquire these high-value accounts:
- Credential Stuffing – Using breached credentials from past cyber incidents, attackers systematically test for password reuse across government email accounts.
- Infostealer Malware – Malicious software captures login credentials stored in browsers or email clients, later sold in bundles on dark web marketplaces.
- Targeted Phishing – Personalized emails deceive government employees into revealing their login details on fake portals, bypassing security layers if multi-factor authentication (MFA) is absent.
Once compromised, these accounts provide unfettered access to inboxes, systems, and services designed exclusively for law enforcement and government use.
Implications and Risks
Compromised accounts allow attackers to impersonate law enforcement or government officials, increasing the chances of successful phishing campaigns, fraud, and data theft. Fraudulent legal requests using these credentials further enhance their potential for misuse, enabling access to confidential information from telecom providers or social platforms.
More troubling, some accounts are being marketed as "toolkits" for accessing restricted databases and investigative platforms.
Securing Government Email Accounts
Enhanced security measures like mandatory MFA, stricter password policies, and proactive phishing awareness training are essential to counter these threats. Prioritizing email account security in government institutions is crucial to mitigating future incidents and protecting sensitive public data.
Last month, reports highlighted a surge in phishing attacks impersonating financial institutions and payment platforms, and hackers cloned the U.S. Department of Education’s grant site in a credential theft campaign.