Dark Web Actors Are Sharing Link to Unprotected ‘Korn Ferry’ Database
- An American consulting firm has misconfigured their Amazon S3 bucket, and actors have accessed it.
- The data contained in the bucket include both employee and client information, while confidential documents are also present.
- The firm hasn’t responded to the notifications of the breach and hasn’t secured the leaking server yet.
‘Korn Ferry,’ the successful American consulting firm, has left an unprotected Amazon S3 bucket online, which was apparently discovered by malicious individuals. The actors then shared the link on the dark web, and Cyble’s sweepers located it. Upon analyzing the files found in the accessible database, the researchers realized that this was confidential information that was never meant to come to light. Obviously, the files have been accessed by a large number of unauthorized third parties, and the company will now have trouble containing the damage done by this misconfiguration.
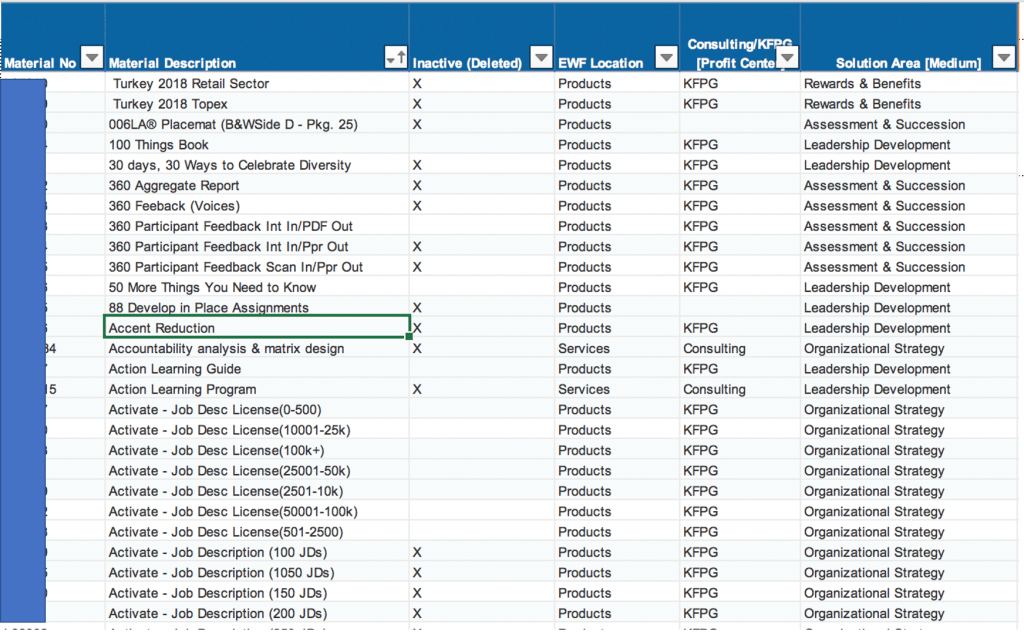
Korn Ferry is a California-based consulting firm that operates 104 offices in 52 countries, employing 8,678 people around the world. The company has revenues counted in the billions and serves clients of the highest prestige and financial magnitude. That said, exposing information belonging to these clients is catastrophic, to say the least. Unfortunately, for Korn Ferry, this seems to be the case with the most recent security incident. More specifically, Cyble has found the following things stored in the unprotected database:
- HR records of employees detailing the employee IDs, their annual base salary along with dollars per hour rate.
- Documents that are confidential to the organization.
- Product hub usernames and default passwords for client users
- Multiple survey templates to gather data such as employee’s availability surveys in different industries
- Detailed records of different types of materials and their pricing.
Source: Cyble blog
As it becomes clear from the above, ‘Korn Ferry’ left a crucial database unprotected online, containing both their internal information and that of their clients. The worst damage was done to the employees who had their sensitive details exposed. These people are now running the risk of getting phished or scammed, and they should receive an identity protection service from their employer soon. The scale of the clients' damage is unknown, as we don't know the content of the exposed documents.
Cyble has reached out to Korn Ferry, but the consulting firm hasn’t responded yet. It means that the unprotected database is still up, and actors are free to access it. This doesn’t look like a database supporting a live system, so even if the actors eventually wipe it, the company may not notice the event immediately. If you work for Korn Ferry or if you are a client, contact the firm immediately and demand action. The exposure of the above data should be considered a fact, and so treating all incoming communications with vigilance is the way to go now.