DanaBot Banking Trojan Resurfaces with Version 669 After Operation Endgame Takedown, Focused on Cryptocurrency Theft
Key Takeaways
- Malware return: The DanaBot banking malware has reemerged with a new variant six months after its takedown in May 2025.
- Infrastructure rebuilt: The malware operators have deployed new C2 servers, using a mix of IP-based and Tor-hidden services to enhance resilience.
- Primary threat: It still focuses on cryptocurrency theft, with configured wallet addresses for Bitcoin, Ethereum, Litecoin, and TRON.
The DanaBot banking trojan has made a significant return to the threat landscape with the appearance of version 669. This resurgence comes nearly six months after the coordinated international law enforcement effort, Operation Endgame, attempted to dismantle its operations in May 2025.
New Command-and-Control Infrastructure
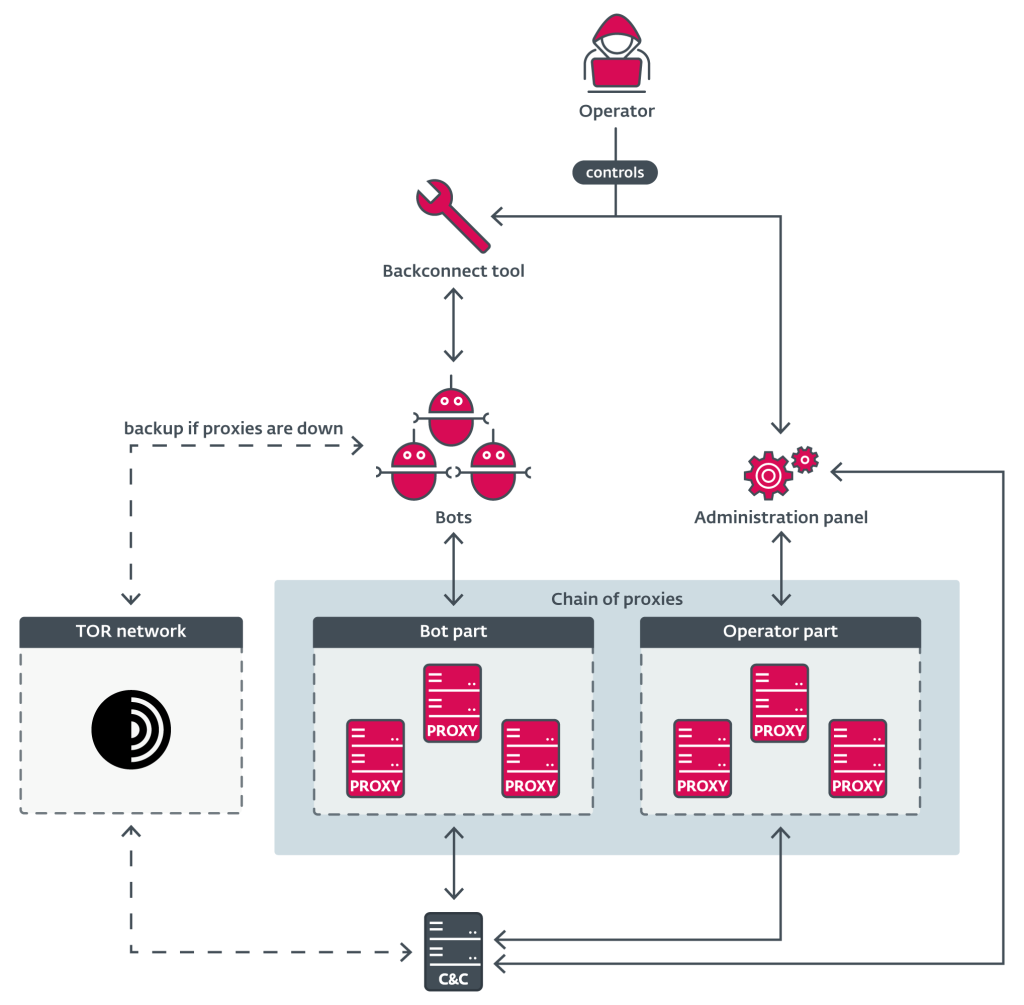
Security researchers at ZScaler have identified a newly established command-and-control (C2) infrastructure supporting DanaBot version 669. The reemergence indicates that the malware's operators have successfully regrouped, rebuilt their infrastructure, and resumed their campaigns.
The operators of DanaBot, a major malware-as-a-service (MaaS) platform active since 2018 that specializes in credential theft and banking fraud, have adopted a hybrid strategy to evade future takedowns, utilizing both traditional IP-based C2 servers and Tor-based hidden services for enhanced anonymity and persistence.
Several C2 endpoints have been identified, alongside backconnect servers designed to facilitate reverse shell connections and access to compromised systems.
The primary objective of the new DanaBot variant remains financial theft, with a strong focus on cryptocurrencies. The malware is configured with dedicated wallet addresses to steal various digital assets, maximizing its monetization potential:
- Bitcoin (BTC)
- Ethereum (ETH)
- Litecoin (LTC)
- TRON (TRX)
Cybersecurity Risks and Implications
The DanaBot malware resurgence poses significant cybersecurity risks for both individuals and financial institutions. Organizations are advised to:
- Enhance endpoint detection and response (EDR) capabilities,
- Monitor network traffic for connections to the newly identified C2 infrastructure,
- Ensure security awareness training addressing the latest phishing and social engineering tactics used to deliver such malware.
In May, the U.S. indicted 16 Russian nationals in the DanaBot case as part of Operation Endgame after several operators unwittingly infected their own machines, exposing their real-world identities through uploaded credentials and internal communications.