“Cyrat” Is a New Ransomware Strain Disguised as a DLL Fixer
- "Cyrat" is a new ransomware strain under heavy development going for payments of $500-$1,000.
- The ransomware is using an unsuitable encryption scheme that can't handle larger files properly.
- Although new, the project is very active, so it could bring widespread trouble soon.
A new ransomware strain called "Cyrat" has appeared in the wild, tricking internet users and finding its way into their machines disguised as a DLL fixer. The first signs of Cyrat appeared on August 25, 2020, and one of the early reports analyzing the characteristics of this ransomware comes from malware analyst Karsten Hahn.
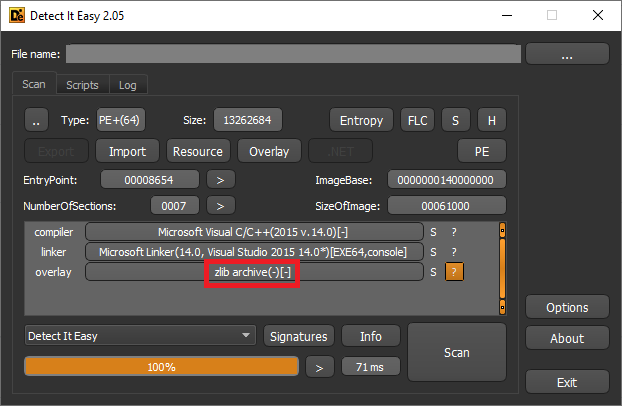
According to the first details that have surfaced, this malware was compiled with Python 3.7 and converted to a Windows PE (pre-installation environment) through PyInstaller. The resulting package is a zlib archive with the filename "PYZ-00."
Source: GData Software
The encryption scheme used in Cyrat is the Fernet symmetric encryption, which is pretty unusual in the field. Most ransomware strains don't use Fernet because it can't handle big-size files very well. On smaller files, it works speedy and effectively as it appends them in RAM, but Cyrat isn't doing size-based discrimination at the time. On the contrary, it scans the user's 'Desktop,' 'Downloads,' 'Pictures,' 'Music,' 'Videos,' and 'Documents' folders, and looks for 188 file extensions to encrypt.
The resulting files have the ".CYRAT" filename extension. The locking process is concluded with the use of a public RSA key, which encrypts the Fernet key.
Source: GData Software
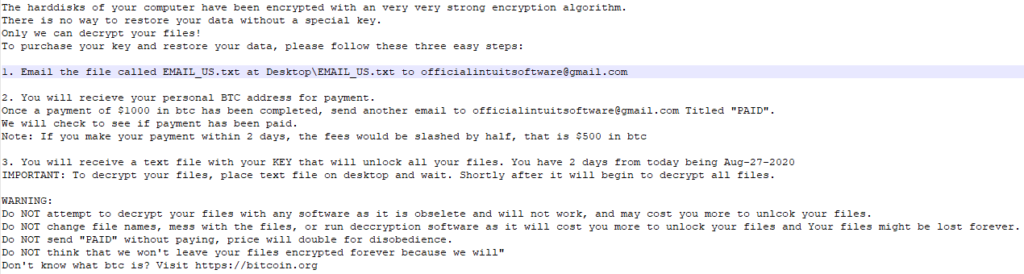
Cyrat sets a wallpaper which depicts a stock ransomware infection photo, while the ransom note demands the payment of $1,000 in BTC, or $500 if completed within 48 hours. To prevent system restoration, Cyrat disables the CMD, the registry tools, the task manager, removes the RUN command from the start menu, and sets "recoveryenabled" to "No."
Additionally, it copies itself to the autostart folder, so in the case that the victim reboots, the ransomware will even encrypt the ransom notes it generated in the previous session.
Source: GData Software
Karsten Hahn says Cyrat crashed when tested, so it's clear that this is still "work in progress." However, the researcher points out that the actors are active and respond to victims' emails, so it's only a matter of time before the infection rates spike. Sure, there are several rough edges to smooth right now, and the choice of Fernet is undoubtedly problematic, but the Cyrat authors are likely already working on these issues.
Hahn discovered another thing during the Cyrat code review: that there are signs showing intention to infect the Linux and Darwin , but these modules aren't complete at the current status. The authors may decide to add this functionality later on or ditch it entirely.
Read More:
- New “SunCrypt” Ransomware Gang Joins the ‘Maze’ Cartel
- A Volkswagen Dealership Has Been Hit by “Conti” Ransomware
- The University of Utah Paid $457,000 to Ransomware Actors