Cybercriminals Go After Accountants Through Yandex.Direct Malvertising
- Malvertising campaigners are using Yandex.Direct again, and their toolset is more abundant than ever.
- From known backdoors and macro-documents to ransomware and phishing forms, it’s all there.
- The main target is Russia-based financial institutions and their accountants.
A recent report by ESET researchers shows that cybercrooks are still after Russian accountants who are merely researching the net to find resources relevant to their work. The criminals post malicious ads on Yandex.Direct, which is an auction-based system for ad placement on the popular Yandex research engine, used widely in Russia. Through this method, unsuspecting accountants are led to believe they are following a link to the resource they were looking for, and land on websites that urge them to download malicious documents plagued by nasty macros, straight-out phishing webpages, or ransomware tools disguised as accounting software suites.
image source: welivesecurity.com
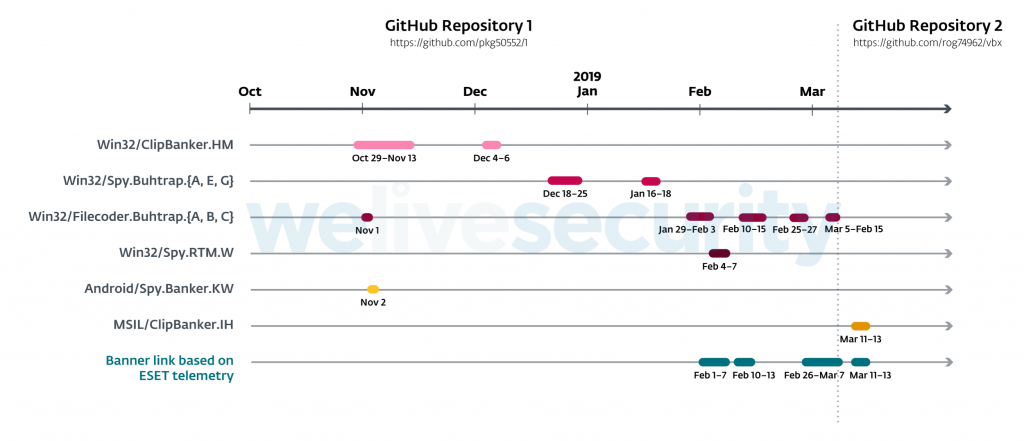
While the ESET team has contacted Yandex and the platform removed the malvertising campaign, for now, the malicious actors are bound to create a new one and keep on doing this indefinitely as long as they are hooking victims on their bait. The researchers have figured out that the malicious files used in the campaign were all hosted on two GitHub repositories, and in all cases, the actors used the known RTM and Buhtrap backdoors, as well as ransomware and crypto-stealing tools. While the source code of Buhtrap is already leaked, the use of the RTM indicates that these actors are the same, or related to previous campaigners who targeted Russian financial institutions from 2016 and onwards.
The actors placed banners to advertise invoice templates, legal contract examples, contract forms, complaint forms, and various other accounting-related stuff. The domains that were used are confirmed to be at least ten different websites, which doesn’t make them malicious or part of the operation of course. The distribution of the macro and phishing documents was intermittent, with GitHub often hosting empty zip files or non-harmful executables, and other times spreading backdoors. By analyzing the malware samples, the researchers also realized that until February 2019, the actors possessed the private key to sign them with legit certificates, although they inexplicably chose not to do this in all occasions.
image source: welivesecurity.com
The operation of the powerful malware tools that were distributed is really extensive, ranging from clipboard monitoring and stealing of credentials, to data exfiltration and local files encryption. The persistence and obfuscation of the tools used in this campaign are also quite notable, as some malware samples were found to be modifying the Windows Registry, sporting anti-tampering mechanisms and trace-wiping capabilities.
The takeout of this story should be that trustworthy ad serving platforms don’t automatically mean that their ad campaigns should be trusted as well. Unfortunately, crooks will use all means they have at their disposal, and utilizing legit ad placement systems is undoubtedly one of the best. Don’t download anything that doesn’t come from a reputable vendor no matter where the banner was placed and how dependable it looks to be.
Have any comments to make on the above? Share your thoughts in the section down below, or on our socials, on Facebook and Twitter.