Cyber Threats Masquerading as AI Tool Installers Deploy CyberLock, LuckyGh0$t, Numero
- Fake AI tool installers are increasingly seen deploying ransomware like CyberLock and LuckyGh0$t.
- Cybersecurity experts also discovered a new destructive malware named Numero.
- These campaigns rely on sophisticated techniques such as SEO poisoning and social media distribution.
Threat actors are deploying ransomware and destructive malware by disguising malicious payloads as legitimate AI tool installers, leveraging sophisticated techniques such as SEO poisoning and social media distribution.
Cisco Talos researchers have identified a range of malware strains posing as AI software, most notably CyberLock ransomware, LuckyGh0$t ransomware, and a newly discovered destructive malware named Numero.
These are targeting organizations eager to adopt artificial intelligence solutions, and each employs unique strategies to compromise victims.
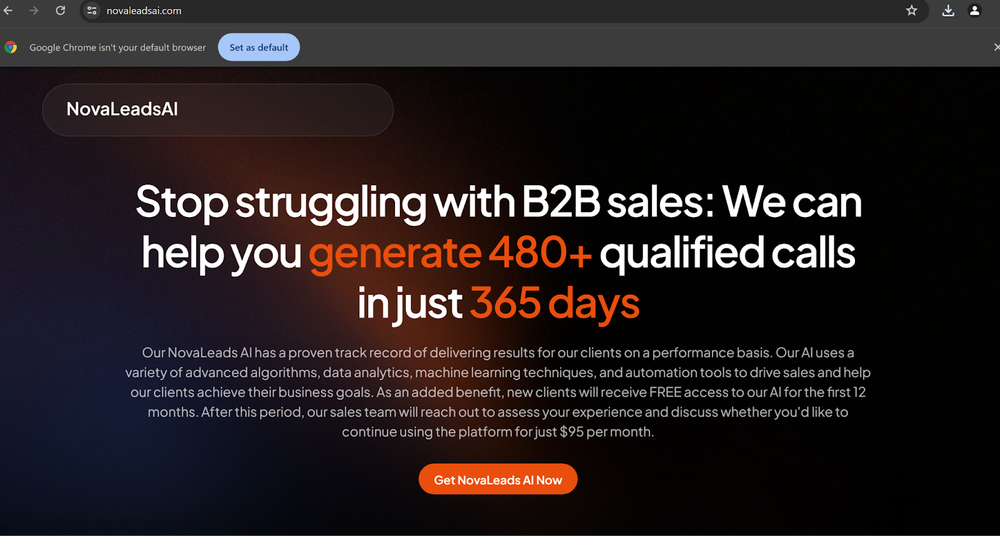
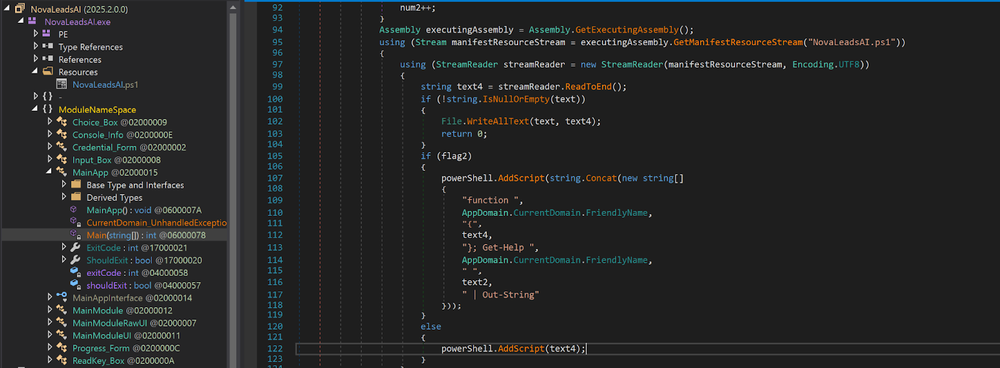
CyberLock Ransomware has been distributed via a fake AI product website imitating the legitimate domain of a popular lead monetization platform. By enticing users with extended free trials, attackers lure businesses into downloading a .NET loader embedded with a PowerShell-based ransomware payload.
Once executed, CyberLock encrypts a comprehensive array of file formats, appends a “.cyberlock” extension, and presents a ransom note demanding $50,000 in Monero cryptocurrency.
Notably, the attackers deploy psychological manipulation by claiming the ransom will fund humanitarian aid, while leveraging techniques such as privilege escalation, desktop wallpaper changes, and erasing free disk space to hinder forensic recovery.
LuckyGh0$t Ransomware is camouflaged as a “ChatGPT 4.0” installer, delivered through a self-extracting ZIP archive. Based on the Yashma ransomware family, LuckyGh0$t encrypts files less than 1.2GB and corrupts larger files by replacing their contents.
It masquerades as a legitimate Microsoft AI tool and uses complex evasion techniques, making detection more challenging for endpoint security tools.
Numero Malware impersonates the AI video creation tool “InVideo AI” and operates by corrupting Windows OS GUI components, rendering systems unusable. Designed to loop persistently and evade analysis, Numero demonstrates a destructive approach, continuously manipulating desktop windows until the device becomes inoperable.
These threats exploit the growing demand for AI tools across B2B sales, marketing, and technology sectors. Adversaries use SEO manipulation and messaging platforms to position malicious installers prominently, increasing the risk for organizations seeking legitimate AI solutions.