Critical ViewState Deserialization Vulnerability Allows RCE on Sitecore Deployments
- Flaw exploited: Attackers are abusing a critical ViewState deserialization vulnerability that impacts several Sitecore deployments.
- How it works: Successful exploitation might lead to remote code execution and unauthorized access to information.
- Why they are vulnerable: The affected Sitecore product deployments are not updated and rely on compromised sample machine keys.
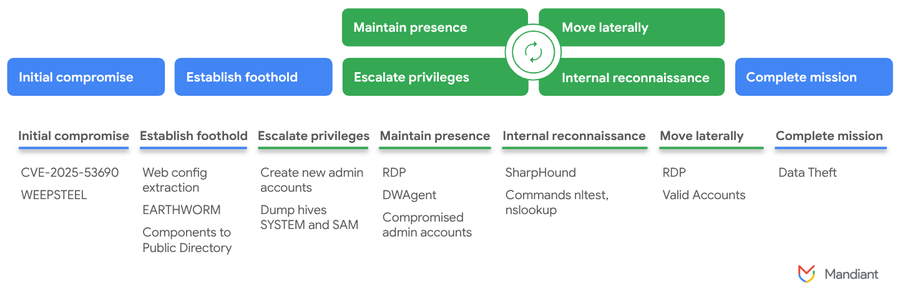
A sophisticated attack campaign exploiting a ViewState deserialization vulnerability, designated CVE-2025-53690, affects multiple Sitecore product deployments utilizing compromised sample machine keys from historical deployment documentation. It allows remote code execution (RCE) on internet-facing Sitecore instances through malicious ViewState payload injection.
Technical Vulnerability Analysis
The CVE-2025-53690 vulnerability stems from the exposure of ASP.NET machine keys in Sitecore deployment guides published in 2017 and earlier versions, according to Mandiant threat research.
These machine keys, designed to protect ViewState integrity and confidentiality, were inadvertently published as sample configurations, compromising the application's ability to differentiate between legitimate and malicious ViewState payloads sent to the server.
Threat intelligence analysis reveals that attackers leveraged exposed machine keys to craft malicious ViewState requests targeting the /sitecore/blocked.aspx endpoint. This legitimate Sitecore component, accessible without authentication, utilizes hidden ViewState forms that become vulnerable when machine key validation mechanisms are compromised.
The attack methodology demonstrates a sophisticated understanding of ASP.NET architecture, with threat actors utilizing tools like the public ysoserial.net project to generate weaponized ViewState payloads.
These payloads contained an embedded .NET assembly that Mandiant tracks as the WEEPSTEEL reconnaissance malware, which shares similarities with the GhostContainer backdoor and an infosealer payload previously observed in the wild.
Sitecore Security Flaw Impact and Exploitation
The vulnerability affects customers deploying Sitecore XP 9.0 and Active Directory 1.4 and earlier versions using the exposed sample machine keys. Successful exploitation grants attackers NETWORK SERVICE privileges, enabling comprehensive system reconnaissance and privilege escalation activities.
Following the initial compromise, the hackers elevated their access privileges to the SYSTEM or ADMINISTRATOR level.
Attack progression includes deployment of open source tooling such as EARTHWORM tunneling software, DWAGENT remote access tool, and SHARPHOUND Active Directory reconnaissance tool.
Mitigation and Recommendations
Sitecore has confirmed that updated deployments automatically generate unique machine keys and has notified affected customers.
Mandiant recommends implementing automated machine key rotation, enabling ViewState Message Authentication Code (MAC) validation, and encrypting plaintext secrets within web.config files to prevent similar vulnerabilities.