Critical TP-Link Zero-Day Vulnerability Exposes Millions of Routers to Full System Takeover
- New zero day: A TP-Link zero-day flaw enables payload delivery and full system compromise with root privileges.
- Stack overflow: A function processes user-controlled data through CWMP SOAP messages without proper bounds checking.
- RCE flaw: After a few easily achievable prerequisites are met, the systems are vulnerable to remote code execution.
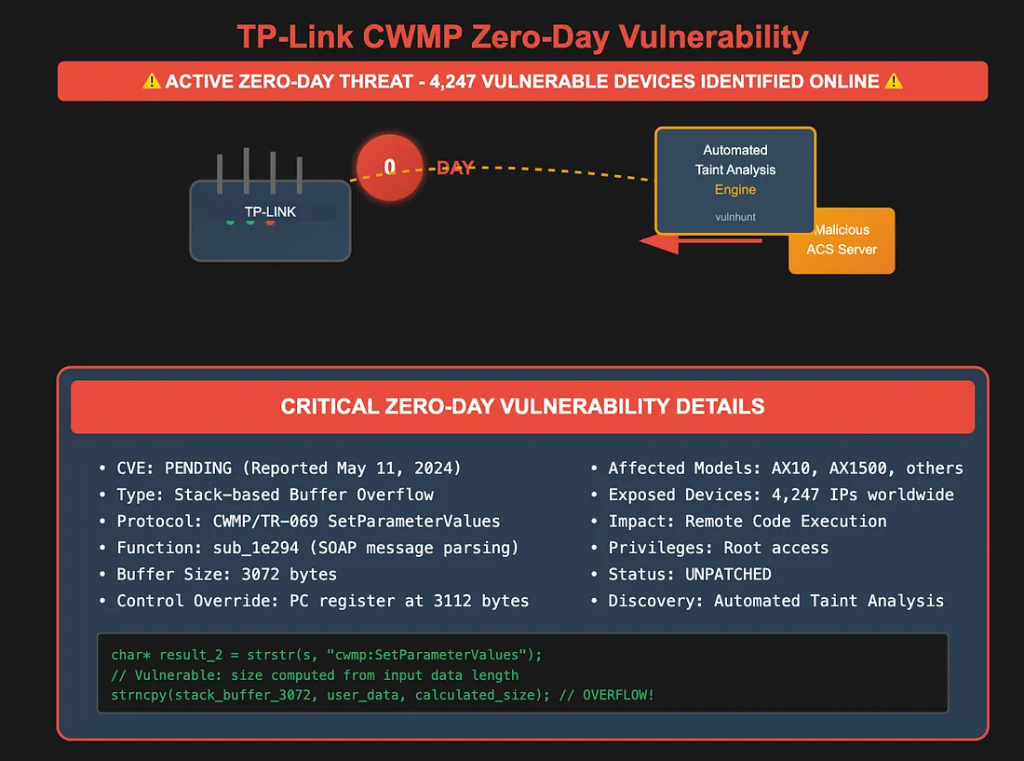
A previously unknown TP-Link zero-day vulnerability has been discovered in the Customer Premises Equipment WAN Management Protocol (CWMP) implementation, affecting multiple router models and exposing users to remote code execution (RCE) attacks. The vulnerability remains unpatched despite being reported to TP-Link in May 2024.
Stack Overflow Vulnerability Details
The CWMP stack overflow vulnerability, identified through automated taint analysis in January 2025, exists in function sub_1e294, which processes SOAP SetParameterValues messages without proper bounds checking.
Security researchers discovered that the vulnerable function calculates buffer sizes based on input data length, creating a dangerous condition where user-controlled data can exceed the allocated 3072-byte stack buffer.
The flaw enables attackers to trigger buffer overflows by sending malicious SOAP messages containing oversized parameter values.
Proof-of-concept testing demonstrated that exactly 3112 bytes are required to overwrite the program counter register, confirming the vulnerability's exploitability for remote code execution with root privileges.
Affected Device Models and Firmware
The TP-Link Archer AX10 vulnerability affects multiple hardware and firmware combinations. Hardware versions V1, V1.2, V2, and V2.6 running firmware versions 1.3.2, 1.3.8, 1.3.9, and 1.3.10 are confirmed vulnerable in all combinations. The TP-Link Archer AX1500 shares identical CWMP binary code, making it equally susceptible to exploitation.
Additional potentially affected models include:
- EX141,
- Archer VR400
- TD-W9970
Internet-wide scanning identified 4,247 unique IP addresses hosting vulnerable TP-Link Archer AX10 and AX1500 devices exposed to public networks, representing significant real-world exposure to RCE via this zero-day.
Router Security Risks and Attack Prerequisites
The router security risks associated with this vulnerability are substantial, though exploitation requires attackers to modify CWMP server configurations. However, security researchers note that gaining access to router configuration is frequently achievable through default credentials, weak passwords, social engineering, or additional flaws.
Once configuration access is obtained, attackers can deploy rogue CWMP servers and trigger the stack overflow vulnerability when devices attempt to connect.
The widespread nature of affected devices and the persistence of default security configurations in many deployments amplify the potential impact of this zero-day vulnerability across residential and small business networks globally.
In June, 12 discovered and patched TP-Link Omada system flaws exposed devices to remote code execution (RCE), denial of service (DoS), arbitrary command injection, and more, and four zero-click DoS flaws in Windows RPC and LDAP were abused to launch large-scale DDoS attacks last month.