Critical Remote Code Execution Vulnerability Found in the Anthropic MCP Inspector
- A critical Anthropic MCP Inspector flaw exposes compromised systems to unauthorized command execution.
- The Inspector Client and Proxy MCP Inspector components are at the core of the issue.
- The security flaw affects versions earlier than 0.14.1 and demands urgent attention.
A severe remote code execution (RCE) vulnerability, cataloged as CVE-2025-49596, has been discovered in Anthropic's widely used MCP Inspector tool. This critical flaw places unpatched systems at significant risk of malicious exploitation and demands immediate remediation.
Tenable Research has identified that the vulnerability, which has been given a CVSS score of 9.4, resides in the MCP Inspector, an open-source tool designed to facilitate testing and troubleshooting for Model Context Protocol (MCP) servers.
Specifically, the security flaw affects versions earlier than 0.14.1, leaving compromised systems vulnerable to unauthorized command execution.
The core of the issue lies within two key components of MCP Inspector: MCP Inspector Client, a web-based interface for managing MCP servers, and MCP Proxy, which bridges communication between the client and MCP servers, according to the Tenable report.
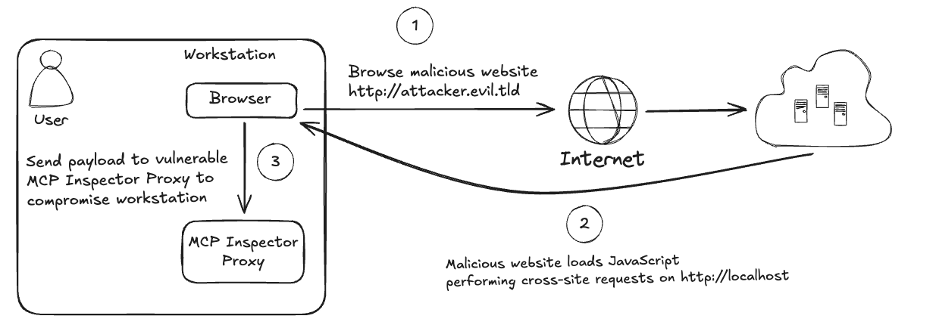
Upon initializing the tool, the MCP Proxy operates without enforcing authentication and binds to all available network interfaces by default. These conditions enable attackers to remotely inject and execute malicious commands, escalating to full system compromise with the privileges of the proxy process.
Exploits can range from direct unauthenticated attacks to cross-origin resource sharing (CORS) manipulation and DNS rebinding. Threat actors could also establish footholds within broader networks, leading to more extensive breaches.
Because MCP Inspector integrates with multiple open-source projects, the risk extends to downstream systems leveraging affected versions.
Additionally, attackers can target victims by luring them to malicious websites that exploit this flaw, allowing remote takeover without user intervention.
Version 0.14.1 or later addresses the vulnerability by enforcing authentication through session tokens, restricting access to localhost-bound network interfaces, and limiting trusted origins to localhost environments.