Conti Lists the ‘Birmingham Barons’ Baseball Team as a Ransomware Victim
- Conti appears to have hit ‘Birmingham Barons,’ a popular American baseball team based in Alabama.
- The actors haven’t published any data yet, but they could have stolen ticket or apparel order details.
- A relatively large seafood restaurant chain from the U.S. has also been listed in Conti’s extortion portal.
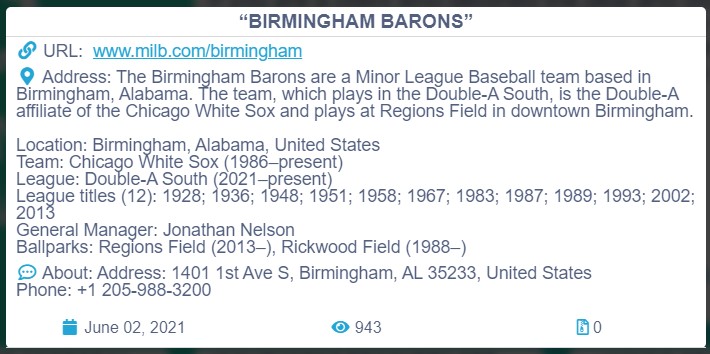
The unstoppable Conti ransomware group has just listed ‘Birmingham Barons’ in its extortion website, meaning that the threat actors have compromised the Alabama-based Minor League Baseball team. There are no leaked files to accompany the announcement, so the ransomware group is looking to negotiate with the team at this point. If that doesn’t yield any results, then we’ll begin to see data published on the extortion portal, as usual.
The website of Birmingham Barons is online, so there are no problems there, and the online shop appears to be working fine. If Conti stole data from the baseball team site, that would mean they’re holding order details, delivery addresses, and possibly even payment details of the fans. Also, the website offers an account creation system to help fans buy game or season tickets, take advantage of promotions, etc., so there is valuable data that could be stored from there as well.
This opens up the potential for widespread exposure, as the Barons are a pretty popular baseball team, an affiliate of the Chicago White Sox, and winner of six Southern League and six Dixie Series championships. All their games are televised and also broadcast on radio, and their official website stands among the top 1,500 most visited in the United States (according to Alexa).
At the same time, Conti has published 5% of the stolen data they exfiltrated from King’s Seafood Company’, an American seafood restaurant chain that operates brands such as Pier Burger, 555 East, King’s Fish House, Meat on Ocean, Water Grill, Fish Camp, and Lou & Mickey's. The published files expose financial documents and employee PII - so for now, if the actors hold any client data, they are holding it back and using it for the extortion process.
Conti’s activity is getting out of proportion, and we are reporting notable victims of the particular ransomware group on a daily basis. Historically, RaaS operations wrap up sometime after a sudden boom in their activities. Still, right now, we don’t know how close Conti’s main operators could be to calling it a day.