Colombian Cybercrime Group Blind Eagle May be Connected to Russian Hosting Service Proton66
- Signs of a connection between Blind Eagle and Russian hosting service Proton66 surfaced via a recent campaign.
- The threat actors used freely available Dynamic DNS services and open-source RATs, including AsyncRAT and Remcos.
- Blind Eagle gains access to victim machines, exfiltrates data, and executes further commands via publicly accessible botnet panels.
A significant connection between the Latin American-focused threat group Blind Eagle (APT-C-36) and the Russian bulletproof hosting provider Proton66 sheds light on a large-scale operation targeting financial institutions across Latin America.
Blind Eagle, known for its focus on Colombian financial institutions, exploits Proton66's infrastructure to execute phishing campaigns and deploy Remote Access Trojans (RATs).
The Trustwave's SpiderLabs team investigation offers a deeper understanding of the infrastructure supporting the group's operations, highlighting their tactics and threat potential.
Trustwave identified these tactics after analyzing infrastructure linked to Proton66 OOO, which hosts clusters of malicious domains exhibiting consistent naming patterns and strong interconnections.
Blind Eagle’s campaigns heavily rely on Visual Basic Scripts (VBS) as the initial malware loader. These scripts download and execute second-stage RATs such as Remcos and AsyncRATs, enabling threat actors to establish command and control (C2) channels with compromised hosts.
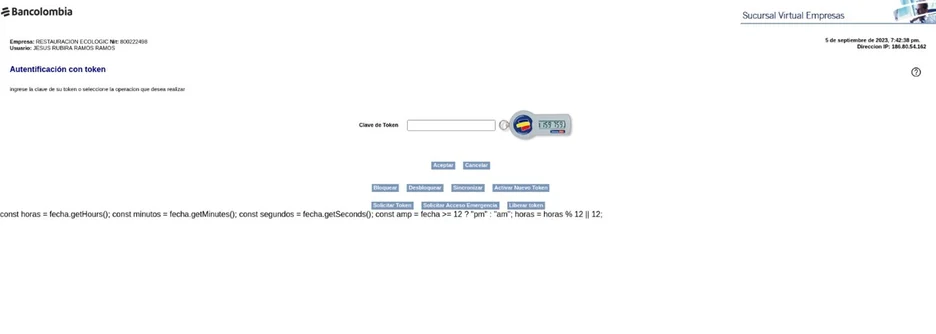
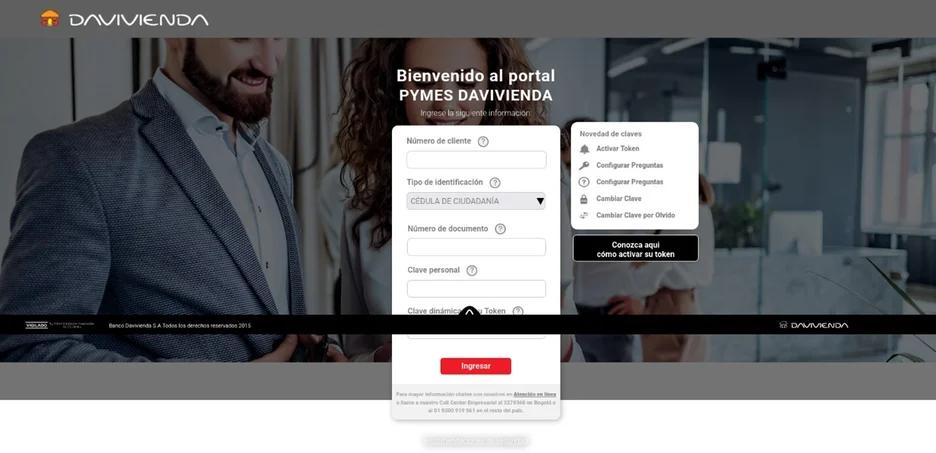
The group set up phishing sites mimicking login pages of well-known Colombian banks like Bancolombia, BBVA, Banco Caja Social, and Davivienda. These pages were designed to steal user credentials and personal information.
These domains, all resolving to the IP address 45.135.232[.]38, were used to execute phishing campaigns and distribute malicious VBS files. The analysis revealed overlaps in VBS code generated using Vbs-Crypter, a subscription-based service enabling payload obfuscation to bypass detection.
Despite employing complex tactics, the group demonstrated minimal effort to hide its infrastructure. Many malicious components, such as phishing pages and botnet panels, were accessible via open directories, with no signs of segmentation or advanced obfuscation.
One notable revelation included a Brazilian Portuguese-language botnet management dashboard, hosted on the identified infrastructure. This panel displayed logs of compromised systems and links to open-source RAT payloads, underscoring the operational scale and accessibility of the campaign.