You Hear That? It’s Cloudflare’s DDoS Protection Working as Expected Against an Acoustics Inspired Attack
- Someone has targeted a Cloudflare client using an acoustics-inspired DDoS attack pattern.
- The attack lasted for 19 hours but failed to overcome the internet firm’s protection systems.
- This attempt was an example of how hackers think out of the box to break sophisticated security measures.
Cloudflare is the leading expert in DDoS (distributed denial of service) mitigation, a type of attack plaguing the net for over two decades now - and which continues to be a threat that can only be managed, not eliminated. The company blocks an average of 72 billion threats per day, many of which are quite voluminous DDoS attempts against its clients.
One recent attempt of this kind was interesting enough to book its own space on Cloudflare’s blog, as someone tried to overcome the company’s protection systems by using acoustics-inspired patterns.
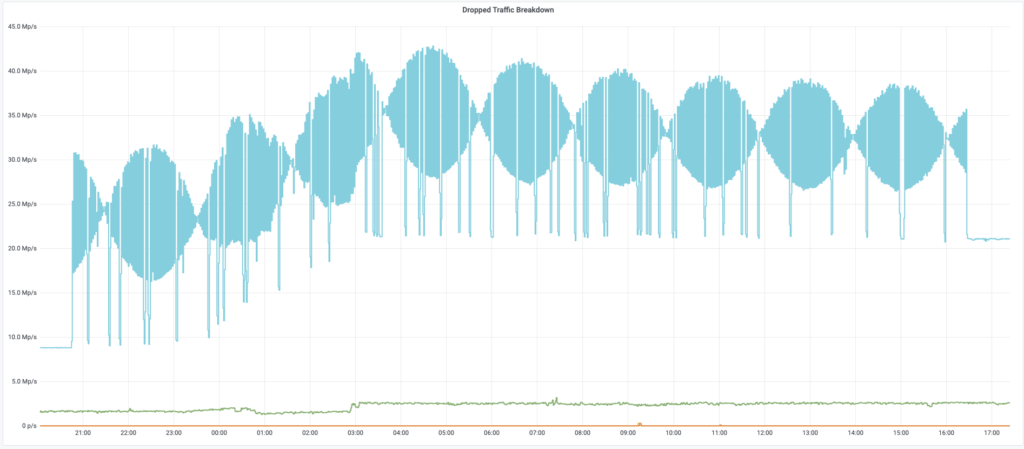
More specifically, the attacker set up a packet rate that followed a wave-shaped pattern that resembled that of a “beat.” In acoustics, the beat is the interference pattern between two sound waves resulting in a periodic variation in volume.
The effect of the two sine waves’ unison is the generation of a beating, hence the name. In the case of the particular DDoS attack, the waves were nearly 180 degrees out of phase, merging to amplify periodically for a time period of 19 hours.
The packet rate used in the attack ranged from 18 Mpps to 42 Mpps, setting the amplitude to 7 Mpps and the wavelength to about 4 hours. The attack traffic accumulated at almost 500 TB and was just a part of the total of 3.6 petabytes that hit the particular customer in November. The beating attack didn’t work, and Cloudflare’s DDoS protection systems worked as expected.
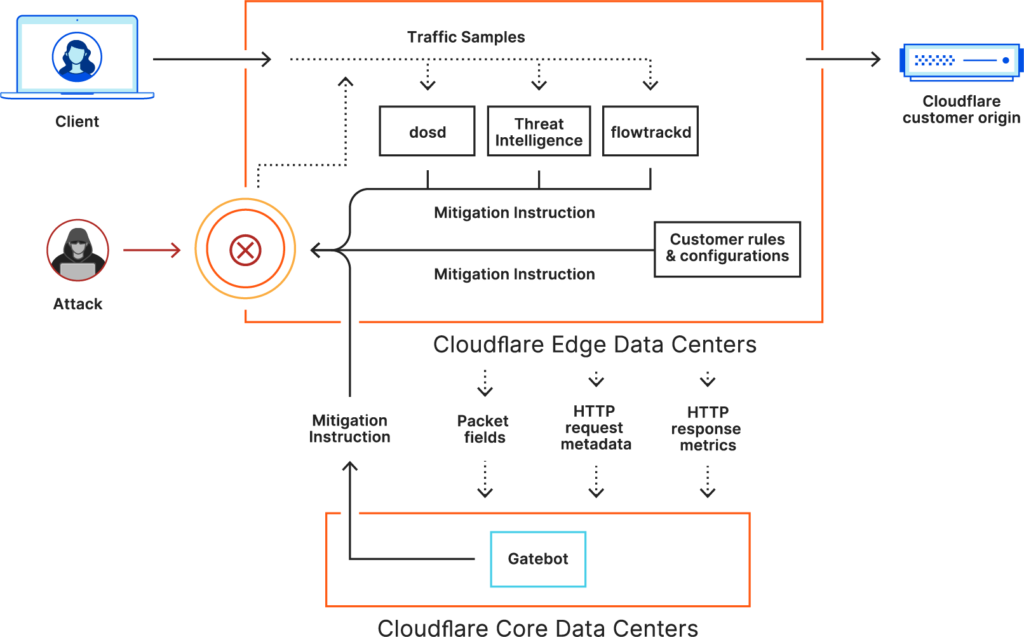
As the blog piece explains, the TCP state tracking machine detected the acoustic-wave-inspired DDoS attack as an ACK packet flood, so it was handled accordingly. Cloudflare’s flowtrackd works in harmony with “dosd” and “Gatebot,” so anything that doesn’t belong to an existing TCP connection is dropped at the internet firm’s edge.
That is regardless of the type, sophistication, size, or other characteristics. The “beat” has failed to overcome Cloudflare’s superior DDoS protection systems, but the actors are bound to try again, and who knows what they’ll think of next time.