ClickFix Fake CAPTCHA Campaigns Show Enhanced Cross-Platform Tactics Targeting macOS and Linux
- ClickFix enhancements: The ClickFix malware campaign employed more sophisticated social engineering tactics and eliminated the need for file downloads.
- New approach: Attackers also adopted dynamic script loading and command obfuscation.
- Cross-platform capabilities: Fake CAPTCHA campaigns have been expanded to include cross-platform payloads targeting macOS and Linux.
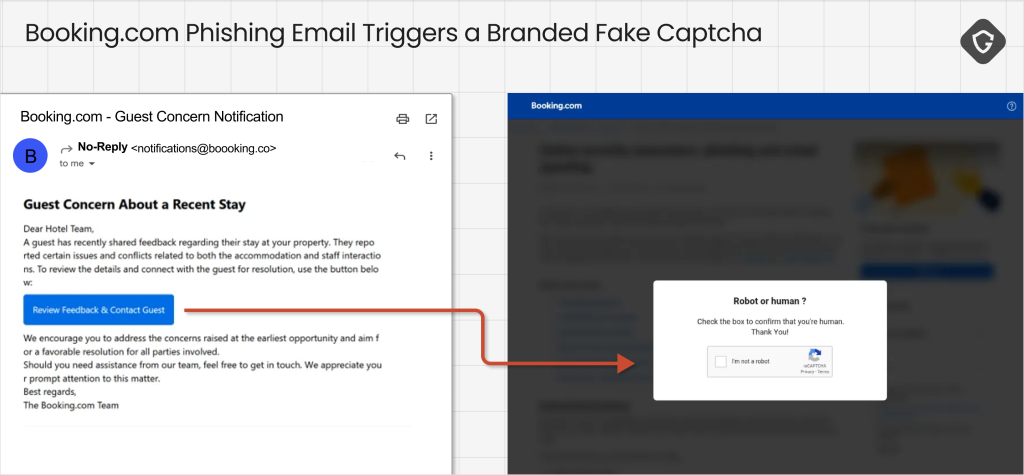
The ClickFix malware campaign, which targets users across multiple platforms via CAPTCHA exploits, spreads via trusted infrastructure, utilizing smarter social engineering tactics and eliminating file downloads. The most recent case is a Booking impersonation via email.
Malware Tactics and Spread
According to a new report from Guardio, this novel approach lures victims into bypassing CAPTCHA challenges, enabling the delivery of malicious payloads on both Windows and macOS systems.
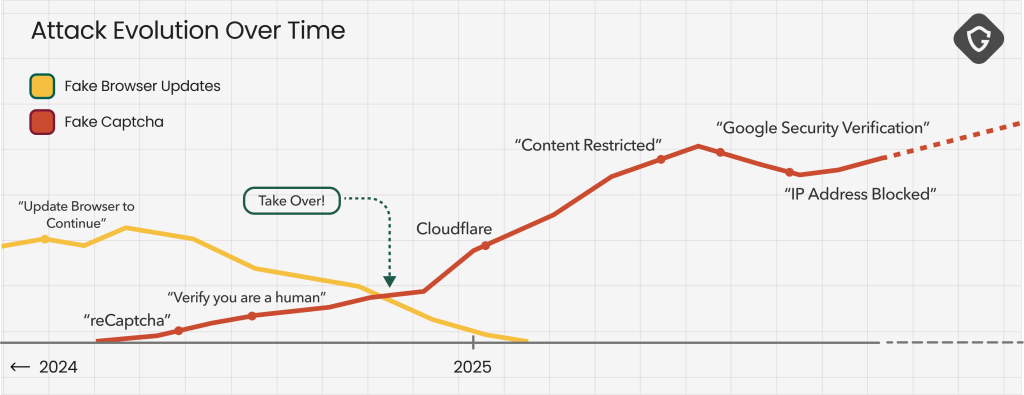
The report highlights an evolution from the ClearFake (fake Browser update) campaigns that disseminated the Lumma stealer malware to the notorious ClickFix approach, which added fake CAPTCHA pages that installed infostealers to exfiltrate accounts, data, and credentials.
Using malvertising campaigns on streaming, pirate content, and free software download pages, they pushed aggressive redirects to fake CAPTCHA pages. Yet, they later moved to abusing compromised legitimate sites and posing as real users on forums, Reddit threads, comment sections, and Git repositories.
Ultimately, attackers resorted to SEO-driven bait websites with legitimate scraped content or misleading or blurred-out text that required “verification.”
Threat actors have advanced their evasion techniques by obfuscating commands, adopting dynamic script loading, and embedding malicious payloads in trusted libraries to bypass detection.
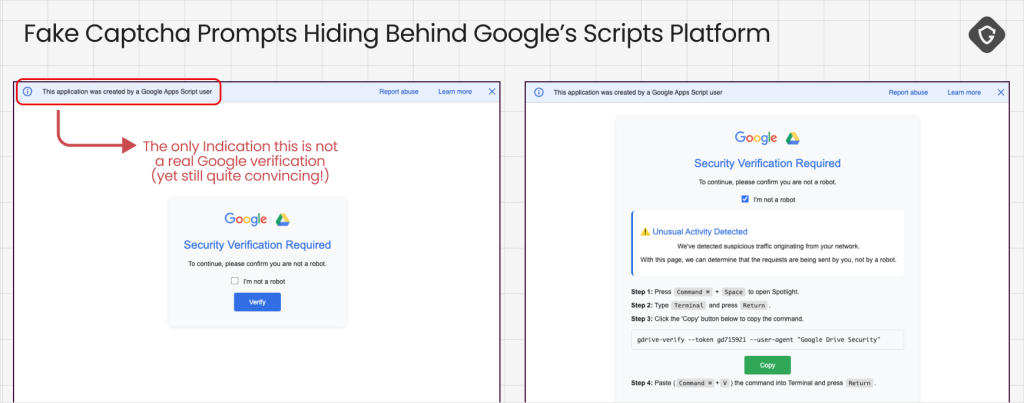
They exploit platforms like Google Scripts to host fake CAPTCHA flows, leveraging trusted domains to evade filters. By mid-2025, attackers expanded to cross-platform payloads targeting macOS and Linux, significantly broadening their victim pool.
Upon successful infiltration, the malware showcases its cross-platform capabilities, adapting its behavior based on the operating system. Windows infections have been observed leveraging PowerShell scripts, while macOS systems experience payload delivery through crafted AppleScripts.
The latest campaign observed by Guardio impersonated the Booking travel website via phishing emails that redirect to a fake Booking login page with a malicious CAPTCHA verification that installs data-stealing malware.
Cross-Platform Impact
This cross-platform malware is particularly concerning due to its capability to target users across diverse environments. Leveraging scripting tools native to targeted platforms, ClickFix can bypass security protocols, gain persistence, and execute lateral movements within compromised networks.
The strategy demonstrates significant technical expertise, advancing beyond traditional, platform-specific attack methods.
Cybersecurity Recommendations
To counteract the ClickFix malware campaign, cybersecurity experts recommend heightened vigilance and robust defenses.
TechNadu reported in May on a new ClickFix campaign distributing LOSTKEYS malware to Western Entities and NGOs. In July, a novel Interlock RAT variant uncovered in the KongTuke FileFix campaign relied on fake CAPTCHAs.