Click Studios ‘Passwordstate’ Compromised by Supply Chain Actors
- The password manager ‘Passwordstate’ was laced by supply chain actors on April 20, 2021.
- Customers who applied an update within a period of 28 hours may have had their passwords stolen.
- The firm has released a hotfix, sent out notices of a breach to affected clients, and advises global password resets.
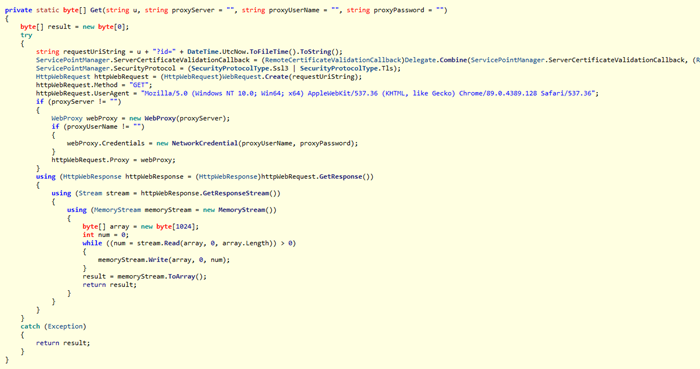
Click Studios, the software development company behind the ‘Passwordstate’ password manager, sent out notices of a breach to its users, informing them of a supply chain compromise that was introduced to the product on April 20, 2021, 8:33 PM UTC. This lasted until April 22, 2021, 0:30 AM UTC, so all clients who have performed an In-Place Upgrade between these 28 hours have potentially downloaded a malicious upgrade ZIP file. Manual upgrades of the Passwordstate product aren’t affected by this, even if carried out during that period.
The malformed version of the product may have resulted in the affected customers having their credentials stolen by the actors. The hackers achieved this by fetching an additional .dll from their own CDN network, which starts a thread in the background. That process is planted on the RAM for detection avoidance and collects the following information for a duration of 24 hours.
- Computer Name
- User Name
- Domain Name
- Current Process Name
- Current Process Id
- All running Processes name and ID
- All running services name
- Display name and status Passwordstate instance’s
- Proxy Server Address
- Username and Password
From Passwordstate’s password table specifically, the following types of data are exfiltrated:
- Title
- UserName
- Description
- GenericField1
- GenericField2
- GenericField3
- Notes
- URL
- Password
The discovery of this rogue dll was the work of the CSIS Security Group, which thankfully happened pretty quickly, essentially minimizing the number of victims. Still, though, it is estimated that a large portion of Click Studios’ 29,000 high-profile customers has been compromised.
The CSIS researchers sampled and analyzed the DLL payload, but the second stage payload was never retrieved due to the C2 (“passwordstate-18ed2.kxcdn[.]com”) being down at the time of the discovery and action.
Compromised entities may have had their VPN, Firewall, Switches, local accounts, and server passwords stolen, so resetting them immediately should be a priority. Moreover, any credentials stored in Passwordstate should be removed as well. The company released a hotfix, the link to which is shared in the security notice circulated. A PowerShell checksum of the hotfix is also advised to avoid another supply chain incident through the hotfix itself.
The firm has promised to provide additional information as soon as possible. Still, for now, the priority is to work closely with all customers, help them identify and fix compromises, as well as provide remedial advice.