Cisco Routers Under Attack After Proof of Concept Revelation
- Cisco RV320 and RV325 were found to contain two “high” severity vulnerabilities.
- The proof of concept code opened the gates of exploitation, and many haven’t updated their tools.
- Cisco urges their customers to patch the routers immediately, as there’s no other workaround.
Proof of concept code is used to demonstrate how a particular vulnerability can be exploited, adding credibility to a researcher’s report and also helping the developers to plug the issues and fix the vulnerability. However, it is often the case that these demonstrations act as the springboard for malicious parties that use them to target the presented hardware/software and take advantage of those who have not updated soon enough and are still vulnerable. This is precisely what happened with Cisco’s RV320 and RV325, two of the company’s most popular and widely deployed WAN VPN routers.
Last week, security researcher David Davidson published his PoC code for two vulnerabilities that affect the aforementioned routers. The first one, CVE-2019- 1653 allows a remote attacker to acquire sensitive configuration data about the device without having to enter any credentials. The second vulnerability, CVE-2019-1652, goes a step further to allow the remote injection and execution of admin-level commands, again, without having to login as administrator. These problems were reported to Cisco, and the California-based IT and networking company was quick to release the firmware update that fixed the issues on Friday.
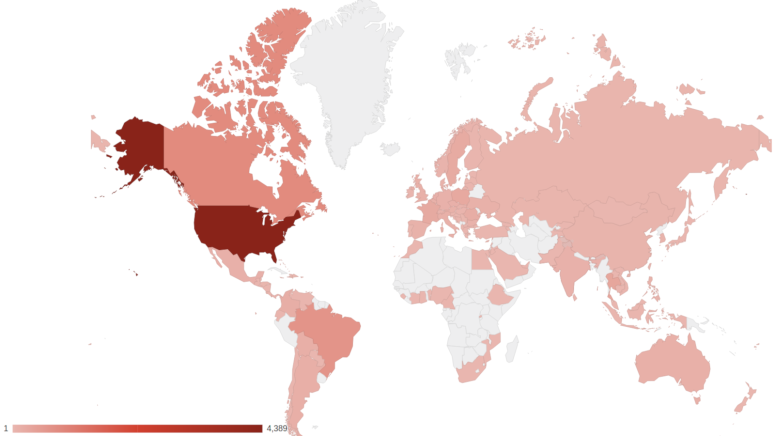
However, and as it often happens in situations like this, not all companies and their IT departments have immediate reflexes, and so a lot of them remained vulnerable since no patching took place. The fact that the weekend intervened wasn’t a helpful occurrence either. According to Bad Packets Report, their honeypots have detected a surge in the scanning activity targeting RV320 and RV325, and thousands of “GET requests” that expose the configuration settings as demonstrated in the PoC. Bad Packets reports that about 63.5% of the routers scanned are vulnerable to CVE-2019-1653, and they have even created an interactive map to showcase where those hosts are to be found.
https://twitter.com/info_dox/status/1089002947076333570
The owners and administrators of these routers are urged to update their firmware to version 1.4.2.20 immediately, as there are no other workarounds to address the vulnerabilities. Moreover, changing the admin and pass, as well as the WiFi credentials is also highly recommended, as attackers may have easily gotten their hands onto them already. Once again, those who update and patch their tools are secure, proving that this is the most dependable way to stay out of trouble.
Do you believe that proof of concept code should be managed differently? Let us know of your opinion in the comments section below, and don’t forget to also check out our socials, on Facebook and Twitter.