Cisco Issues Patch for Critical Unified CM and SME Vulnerability (CVE-2025-20309)
- Cisco has disclosed a critical Unified CM and SME security flaw tracked as CVE-2025-20309.
- An unauthenticated, remote attacker could log in to an affected device and execute arbitrary commands using the root account.
- These admin accounts have static credentials that cannot be changed or deleted, so no workarounds are available.
A critical security flaw in Cisco Unified Communications Manager (Unified CM) and Session Management Edition (SME) releases allows remote attackers to exploit static SSH (Secure Shell) credentials for the root account, granting them full administrative privileges.
The vulnerability, tracked as CVE-2025-20309, stems from hardcoded credentials intended for development and poses significant risks by enabling unauthorized access and command execution as a root user.
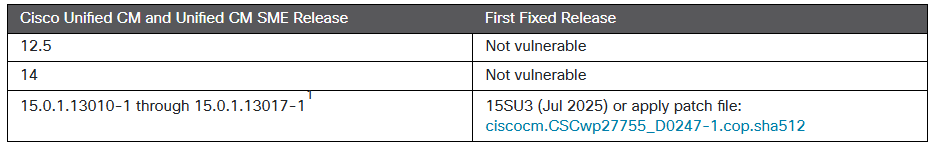
According to Cisco's advisory, the vulnerability affects Engineering Special (ES) releases 15.0.1.13010-1 through 15.0.1.13017-1 – limited fix releases that are distributed only by the Cisco Technical Assistance Center (TAC).
The company warns that there are no available workarounds for this flaw, underscoring the urgency of rolling out the provided software updates to affected systems.
Fixed releases, including 15SU3, have been made available to resolve the issue. Cisco recommends that customers promptly upgrade their software to mitigate the risks associated with potential exploitation.
Cisco reports that successful exploitation would allow attackers to log into affected systems and execute arbitrary commands, which could severely compromise enterprise communications infrastructures.
Yet, the vulnerability was identified through internal security assessments, with no evidence of it being exploited in the wild at this stage.
Ben Ronallo, Principal Cyber Security Engineer at application security solutions provider Black Duck, believes that exposing admin credentials significantly increases the potential for malicious activity. “One plausible effect of this could be that an attacker is able to modify network routing for social engineering or data exfiltration purposes,” Ronallo said.
However, “mature organizations do not typically install ES releases as part of standard practice,” Mayuresh Dani, Security Research Manager at Qualys Threat Research Unit said, adding that ES TAC releases address “specific customer issues or urgent bugs that are not yet resolved in the standard Service Update (SU) or General Availability (GA) releases.”
An attacker could leverage affected Unified CM instances to run commands, plant backdoors, exfiltrate call audio, collect credentials, and tamper with authentication services, so “phone, video and emergency lines could be silently rerouted or knocked offline,” Jason Soroko, Senior Fellow at CLM firm Sectigo, added regarding the risks of this flaw.
Hardcoded credentials, often deemed a relic of legacy development practices, continue to pose serious risks.