CISA Warns About the Perils of SFA as Brute-Force Attacks Reach New Levels
- CISA adds single-factor authentication to its list of bad cybersecurity practices.
- Passwords are just too easy to obtain even if they’re unique and strong, so they aren’t secure on their own.
- Applying multi-factor authentication helps tackle brute force attacks that are currently on the rise.
There are just too many accounts lying behind a single layer of authentication as it seems, and CISA is warning about the risk of the practice and why it should be considered a very inadequate and partial cybersecurity practice. The American agency has added single-factor authentication for remote or administrative access to systems supporting NCF (National Critical Functions) in its “list of bad practices,” but it really applies to everything online. No account should rely solely upon a password, as passwords can be stolen, leaked, deduced, guessed, exposed, keylogged, and brute-forced.
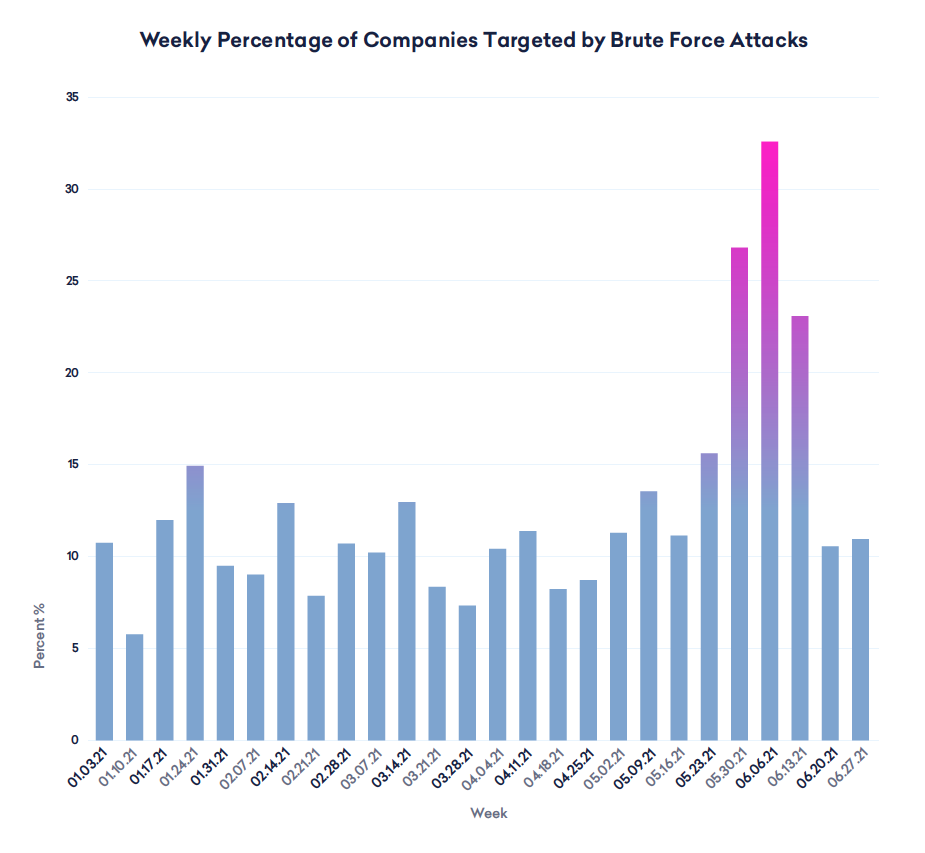
According to a report by Abnormal Security, brute-forcing attacks have risen by 671% (week by week) in the first week of June 2021, and recording a monthly rise of 160% in June compared to May. Over the court of Q2 2021, credential phishing rose by 73% compared to Q4 2020. All metrics show that actors are focusing a lot on brute-forcing - and this indicates that they’re getting to access valuable accounts only by guessing the password, as brute-forcing cannot do much against multi-factor authentication steps.
The stats in the Abnormal Security report show that BEC (business email compromise) is still the main channel of trickery, with the actors impersonating a high-ranking executive, vendors, or colleagues to convince the recipient. Many times, the email arrives from that person’s real address, as the actors have managed to brute force their password and take over their accounts. This is further reflected in the fact that random impersonation has dropped from 45% to 34% in the first half of 2021.
Brute force attacks, though, aren’t always focusing on steering business payments on actor-controlled accounts. CISA’s warning points to the possibility of allowing hackers to infiltrate sensitive networks, perform lateral movement, reconnaissance, privilege escalation, and eventually data exfiltration.
In summary, using multi-factor authentication is key in rendering these attacks useless, and so it should be considered imperative. Apart from that, password length and complexity should be increased, login attempts should be limited, and even Captcha steps could be implemented to verify that automated attacks won’t work.