Chinese Vendor of OLT Devices Loads them with Firmware Backdoors
- “C-Data” is planting backdoors on its OLT devices, allowing easy remote telnet access.
- Such an attack could potentially have a wide range of exploitation possibilities, including plaintext data exfiltration.
- The vendor hasn’t responded, and you should generally abandon any hope for fixing patches.
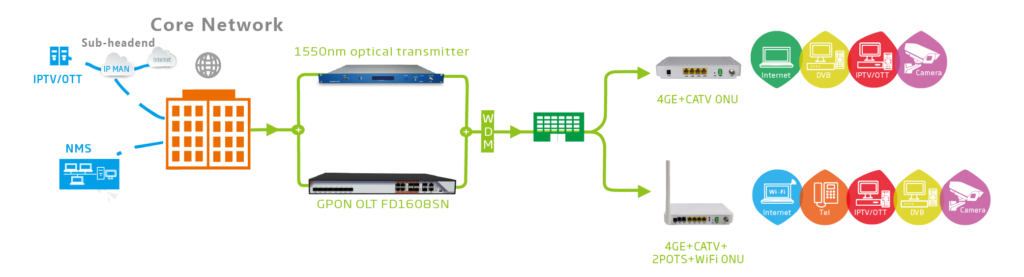
“C-Data”, a Chinese manufacturer of network equipment was “caught” by security researchers Pierre Kim and Alexandre Torres, who found intentionally planted backdoors in OLT (optical line terminal) firmware. These devices are basically used by network engineers to “terminate” the optical line and convert it to an Ethernet connection. This is why these terminals are typically found nearby or inside buildings, offices, homes, and the end-user in general. “C-Data” is selling these OLTs under its brand, or as “OptiLink”, “V-SOL CN”, or “BLIY”.
Source: C-Data
The researchers tested C-Data models “FD1104B” and “FD1108SN” in the lab and figured that firmware versions V1.2.2 and 2.4.05_000, 2.4.04_001 and 2.4.03_000 contain the backdoors. Upon further analysis, the team figured that the following models are affected by this critical security problem:
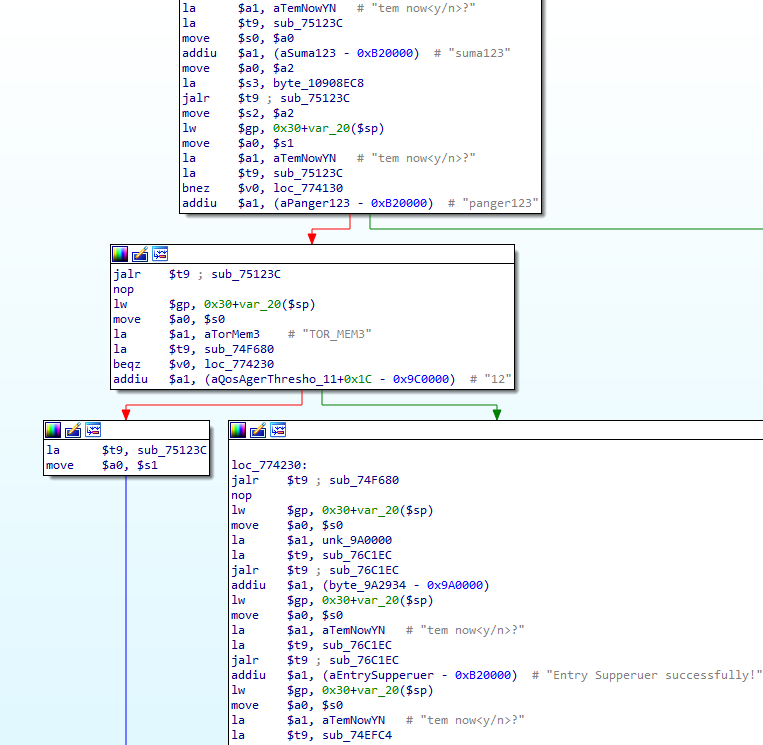
Source: C-DataThe backdoor was planted intentionally without a doubt and allows a remote user to connect to the clients that are linked with the OLT via a telnet server. The firmware contains hardcoded credentials like “debug” + “debug124” or “root” + “root126”, which would be easy to brute-force even from people who don’t work in C-Data.
Source: pierrekim.github.io
Once the attacker has established presence through telnet, there are various things they can do next. One would be to extract the administrator credentials, another would be to escape the shell with root privileges, and other exploitation scenarios could involve the launching of pre-auth remote denial of service attacks. As the researcher explains, all of the above are pretty easy to carry out by running simple commands. MITM and password interception that would exfiltrate data in clear text form would be entirely possible, and a grave scenario for the end-user.
The researchers didn’t bother contacting the vendor of the devices and waiting for a response, a patch, going through retesting rounds, etc., as they believe the vulnerabilities were intentionally planted. Thus, they just published everything for the networking engineers to take note of and do the needful. C-Data hasn’t issued an official response on the above, and it will surely be very hard for their PR to explain all that. As for what the end-user can do, the answer is not much other than informing your ISP and demanding their technicians to double-check what equipment they’re using.
Read More:
- Hackers Have Been Actively Exploiting DrayTek Equipment Zero Days
- Powerline Networking Flaws Highlight a Fundamental Security Problem