Chinese Spies Exploit Venezuela Crisis to Target US Officials in Phishing Campaign Deploying Backdoor
- Targeted Espionage: A Chinese-linked cyberespionage group executed a highly targeted campaign against U.S. government and policy officials.
- Political Lure: Emails contain Venezuela-themed phishing lures following recent geopolitical developments involving the capture of the country’s leader, Nicolás Maduro.
- Malware Deployment: A malicious ZIP archive deploys LOTUSLITE, a custom C++ backdoor capable of remote tasking and data exfiltration via DLL sideloading.
A sophisticated Chinese cyberespionage campaign recently targeted U.S. government entities by exploiting the geopolitical volatility surrounding Venezuela following U.S. operations related to Venezuelan leadership.
Researchers attribute the activity with moderate confidence to Mustang Panda, a state-sponsored entity known for aligning its cyber operations with current geopolitical events to facilitate intelligence collection, previously linked to a modified variant of the TONESHELL backdoor.
Technical Analysis of LOTUSLITE Backdoor
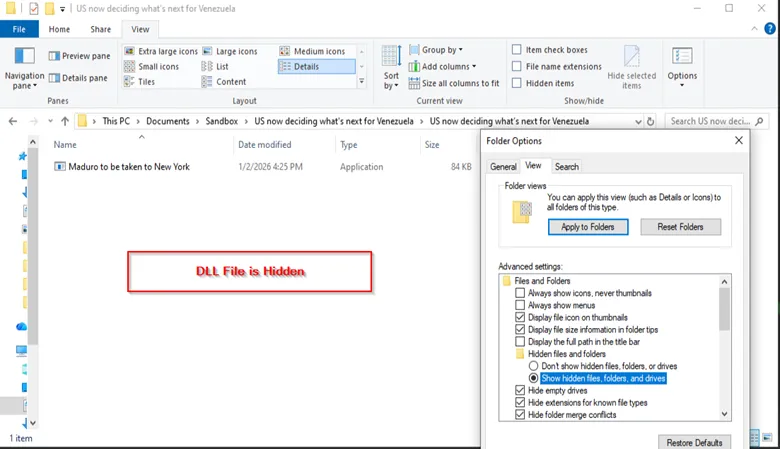
The threat actors distributed phishing emails containing a ZIP archive titled "U.S. now deciding what’s next for Venezuela.zip," Acronis cybersecurity researchers said. The use of such timely and specific lures indicates a deliberate effort to compromise high-value targets within the U.S. policy and government sectors.
The attack chain relied on a distinct execution flow designed to evade detection. The malicious archive contained a legitimate executable and a hidden, nonstandard DLL.
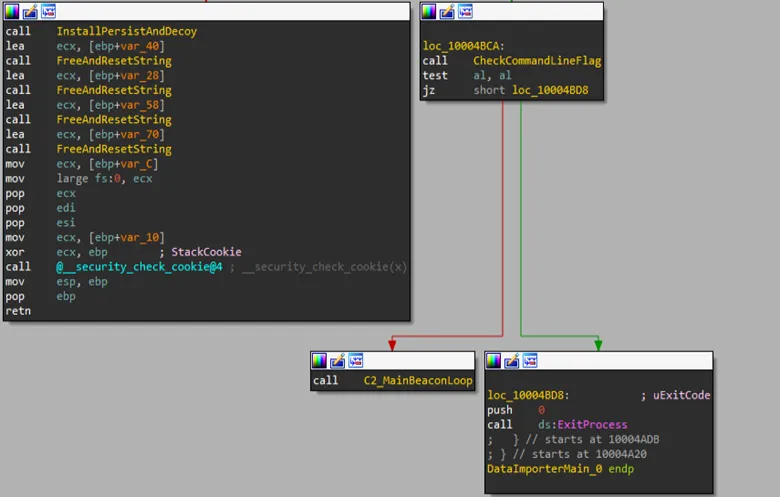
This process deployed the LOTUSLITE backdoor, a custom implant designed for persistent access. The malware establishes persistence via registry modifications and communicates with a hard-coded command-and-control (C2) server to receive instructions.
Its capabilities are strictly espionage-focused, supporting remote command execution and data exfiltration while avoiding the disruptive behaviors typically associated with financially motivated cybercrime.
The author of the report, Subhajeet Singha, told Reuters that the hackers appeared to be in a haste to leverage the rapidly developing geopolitical situation and left behind “artifacts that helped link the malware to prior Mustang Panda operations.”
Implications for U.S. Government Cybersecurity
The deployment of Venezuela-themed phishing emails demonstrates how adversaries rapidly weaponize breaking news to engineer social engineering attacks. The technical tradecraft, specifically the reliance on DLL sideloading and custom loaders, reflects a focus on operational reliability over extreme sophistication.
Security teams defending government networks must remain vigilant against spear-phishing campaigns that mirror real-time political developments, particularly those involving foreign policy interests relevant to Chinese state objectives.
“China firmly opposes the dissemination of false information about so-called 'Chinese cyber threats' for political purposes,” a spokesperson for the Chinese embassy in Washington told Reuters.
The UNC6384 group, a threat actor associated with TEMP.Hex (Mustang Panda), was linked by GTIG in August to a PRC-nexus espionage campaign targeting diplomats across Southeast Asia via web traffic hijacking, and Arctic Wolf linked the group to a cyberespionage campaign targeting European diplomatic entities via spear-phishing.
Reports this month said the Chinese group Salt Typhoon allegedly hacked the U.S. House of Representatives staff email server, previously accused of gathering data on American telecommunications.