Chinese Hacking Group ‘TA416’ Return With a Golang PlugX Malware Loader
- Chinese hackers have returned to active phishing operations, targeting African diplomats.
- The state-supported group of “RedDelta” is deploying PlugX malware through Golang loaders.
- The distribution vector remains unknown, but it’s possibly URLs on legitimate cloud services.
“TA416” (aka “RedDelta”), the hacking group that is believed to be supported by the Chinese government, has returned in full operations and uses a refreshed toolset that delivers PlugX malware payloads to the targets. The threat actors are now targeting African organizations that specialize in diplomacy and international relations, so the motive appears to be cyber-espionage and collecting intelligence. The group’s recent activity has been spotted by researchers of ProofPoint, who have prepared a detailed report on it.
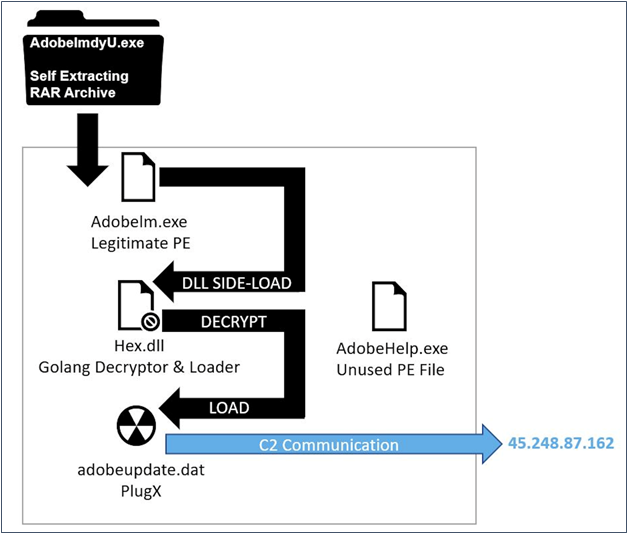
The hackers are using two RAR archives that serve as malware droppers, but the researchers were unable to figure out the delivery vector for these files. Possibly, the actors are abusing Google Drive or Dropbox services again, incorporating URLs that point there inside phishing emails. The archives are self-extracting, and an executable file (Adobelm.exe) contained there is auto-executed.
The executable performs the side-loading of the hex.dll file, which is also contained in the extracted archive, and eventually, a Golang binary is loaded to decrypt and execute the PlugX payload (adobeupdate.dat). The Goland loader sampled by the researchers was created on June 24, 2020, but it got its first deployment in the wild after August 24, 2020.
As for the command and control infrastructure, ProofPoint has identified the following three URLs:
- 45.248.87[.]162
- hxxp://45.248.87[.]162/756d1598
- hxxp://45.248.87[.]162/9f86852b
These are all hosted by Anchnet Asia Limited, a Chinese ISP, while the actors appear to have kept their C2 online until at least September 28, 2020. After that date, ‘TA416’ have gone silent and remained inactive for nearly a full month. The resumption of the phishing activity by the particular hacking group resumed around the end of October, and it’s ongoing.
Actors of this level know how to hide effectively from researchers and security tools, so following their activities closely and reporting on them is key. TA416 continues to target high-profile entities and attempt to compromise their communications with a continually refreshed set of tools.