Chinese Hackers Stealing Data From Global Telecommunications Providers
- A group of hackers who are probably sponsored by the Chinese state have been stealing call records from many telecommunication providers.
- The hackers infiltrated the networks with ease and downloaded many gigabytes of raw data logs.
- The operation went on from 2017 until today and targeted at least 20 high-interest individuals.
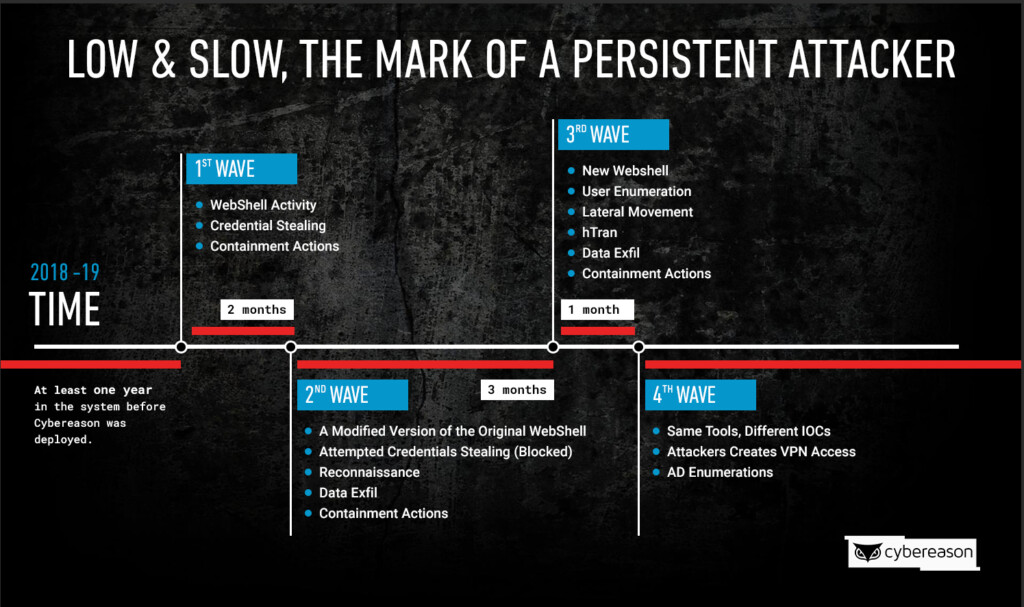
As unveiled by the Cybereason Nocturnus security team, the Chinese hacker group known as “APT10” were involved in a long-term, persistent, and advanced series of attacks against numerous global telecommunications providers. The goal of the actors was to steal data relating to at least 20 high-interest customers of these service providers, purloining key information about their communication and activities. The actors achieved this by compromising the network of the telcos and stealing targeted call detail records from their systems. Cybereason gives the operation the name “Operation Soft Cell”, and has deduced that it has been going one since at least 2017, possibly even earlier.
image source: cybereason.com
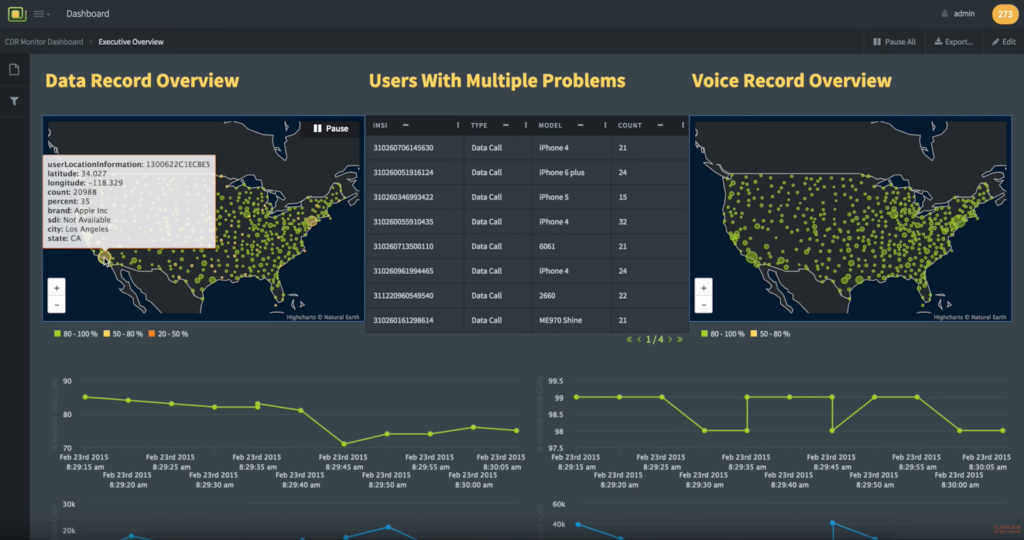
According to the details of the report, the hackers were able to steal personally identifiable information (PII), call detail records, user credentials, geolocation information about their targets, billing data, email server information, and the usernames and passwords of the users who administered the critical systems of the telecom providers. While the actual calls or messages aren’t included in these call records, the detailed metadata logs are usually more than enough in the context of espionage operations. Moreover, without hacking the phone of the target directly, you run no risk of the target ever suspecting anything shady going on.
image source: cybereason.com
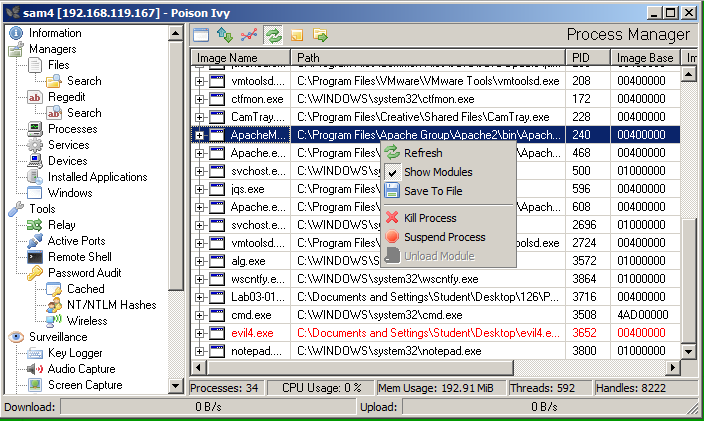
As one of the researchers detailed, the hackers even created a virtual private network connection on one of the telecom's compromised servers, so as they could re-access it again without having to go through the process of dumping credentials and making their way deeper into the network step by step. As for the tools used, we see the trend of "living off the land" again with modified versions of open source and freely available legitimate tools such as NBTSCAN, Mimikatz, WinRAR, WMI, and PsExec. However, there are also the tools that gave away the group, like the PoisonIvy Remote Access Tool that is associated with APT10.
image source: cybereason.com
Cybereason believes that Operation Soft Cell is state-sponsored, but they cannot prove this with absolute certainty. The main sign of this is that the hackers were not after financial information but intellectual property and other types of sensitive data associated with their targets. This means that they are after spying, not making money. Moreover, the level of sophistication and infiltration achievement indicates a very advanced group of hackers and not just haphazard. The actors managed to take full control of the telecommunication providers’ infrastructure, being able to inflict considerable damage to it, but decided not to because their goal was a very different one.
Do you have something to comment on the above? Share your thought with us in the comments section beneath, or join the discussion on our socials media platforms, on Facebook and Twitter.