Chinese Hackers Caught Using UN Website to Target Uyghur Muslims
- Chinese hackers are targeting high-profile Uyghur Muslims in China, Pakistan, Turkey, and Malaysia.
- The actors were caught using UN websites and logos to impersonate its human rights department.
- The malware used in this campaign is more of a silent profiler than a damaging tool.
The ethnic group of Uyghur Muslims isn’t having an easy time in China, and that has been established on multiple occasions in the recent past. Chinese state-sponsored hackers target them through ‘watering hole’ websites, malware, social media platforms, and iOS zero-days. They are often combining these to launch powerful privacy-striping attacks. The latest reports from Check Point Research and Kaspersky talk about a novel approach, using a fake UN website to lure people from the Uyghur community and identify them.
The researchers claim to have been following the actors closely for over a year now, and they have collected several pieces of evidence like the malicious documents that the Chinese hackers use. In these files, we can see the UNHRC logos and content that appear to have been copy-pasted. The main topics revolve around human rights violations, attempting to convince the recipients that the sender is on their side, offering help and support.
The documents carry malicious macros that require “Enable Editing,” If the victim approves that request, the VBA macro code is allowed to run and decode a 32-bit or 64-bit payload. These payloads are shellcode loaders that initiate some basic evasion and anti-debugging routines. Having “prepared the ground,” the shellcode then attempts to fetch the main payload, which the researchers could never retrieve and analyze.
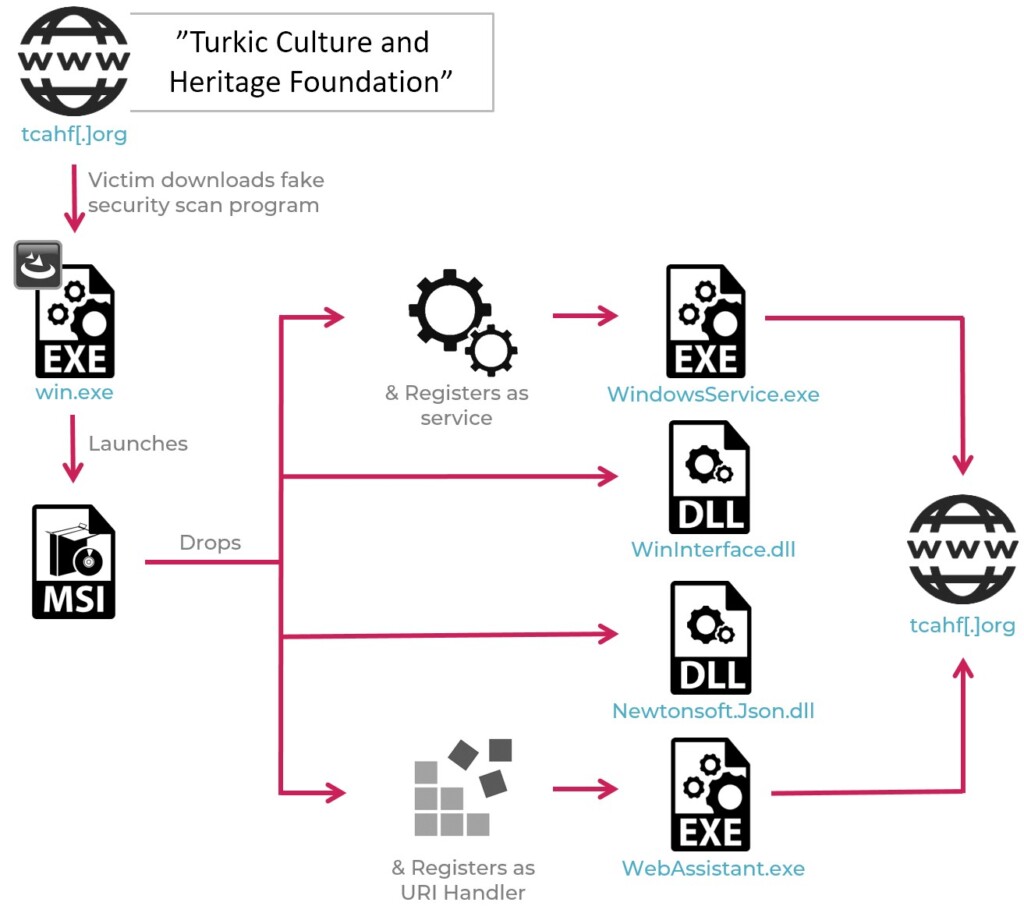
The domains that deliver the documents are impersonating the Office of the United Nations High Commissioner for Human Rights (OHCHR). In another case, the researchers noticed an IP address resolving to tchf[.]org, impersonating the “Turkic Culture and Heritage Foundation.” This website is made up as the actual organization doesn’t have one, yet the actors present it with “who we are” details and everything else that is to be expected from a legit entity of this kind.
What this tells us is that the hackers are targeting high-profile and high-standing Uyghur members who are interested in reading UN documents and staying up to date with the developments. This assumption is also backed by the fact that the malware that is used is geared towards profiling the victim rather than doing any actual damage. Maybe this is why the main payload was never delivered to the targets anyway.
If you are a member of a suppressed minority, you should avoid enabling macros on your Office suite in general. Whenever you are requested to activate them, it is almost certainly to do you harm. In addition to running trustworthy internet security and an AV solution, you should also use a VPN tool at all times and a private email service that supports encryption.