Chinese APT “NAIKON” Is Using a Backup Backdoor Called “Nebulae”
- One of NAIKON’s secondary “backup” backdoors has been discovered, and it’s a nasty piece of software.
- The Chinese actors have deployed the backdoor called “Nebulae” for almost two full years.
- When it comes to APTs, persistence is seldom reliant on a single malware.
Researchers at Bitdefender have discovered a novel backdoor called “Nebulae,” which appears to be linked with the Chinese APT group known as “NAIKON.” The particular hackers have been active for at least a decade now, focusing their efforts on cyber-espionage against government agencies and military organizations in the South Asian region. The Nebulae appears to be a backup backdoor used for persistence in the case that the primary backdoor is found and uprooted by the defenders.
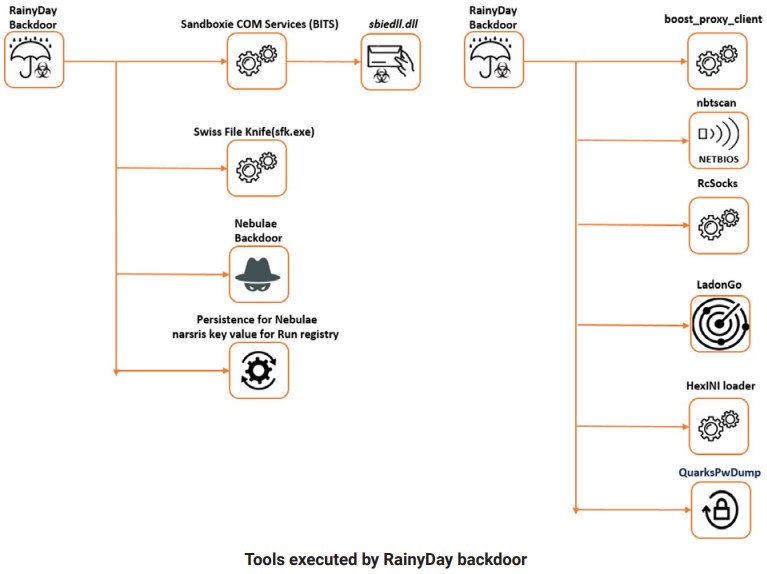
Nebulae has been used by NAIKON since June 2019, landing on the compromised systems at the first stage of the attack together with the “Aria-Body” loader. According to Bitdefender’s observations, NAIKON started using the “RainyDay” backdoor from September 2020 and onward. However, not every tool in the APT’s arsenal was intrinsically malicious.
The researchers report the following legit tools as being abused by NAIKON:
- ARO 2012 Tutorial 8.0.12.0
- VirusScan On-Demand Scan Task Properties (McAfee, Inc.)
- Sandboxie COM Services (BITS) 3.55.06 (SANDBOXIE L.T.D)
- Outlook Item Finder 11.0.5510 (Microsoft Corporation)
- Mobile Popup Application 16.00 (Quick Heal Technologies (P) Ltd.)
Both backdoors are using the DLL side-loading technique to gain the local privileges they need for malicious operations. Nebulae’s capabilities include the following:
- Getting LogicalDrive information (Drive type, FreeSpace, VolumeInformation)
- Listing, moving, and deleting files and directories
- Executing a process using CreateProcess or through a CMD shell
- Listing and terminating processes
- Downloading and uploading files from and to C&C
The above is quite impressive for a secondary backdoor, offering NAIKON full power over the compromised machine even if or when things don’t go as planned. Also, Nebulae is perfectly adequate for the job of reintroducing additional payloads onto the compromised system.
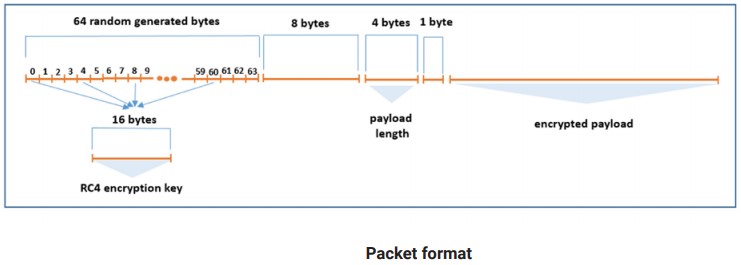
The key remains to keep the backdoor hidden, as Nebulae needs to be very stealthy. Its communication with the C2 is optimized for stealthiness, taking place through a TCP connection and featuring RC4 encryption.
Bitdefender’s report goes on to analyze NAIKON’s entire toolset, with credential harvesters, exfiltration tools, network tools, etc., so it is worth a read. For us, the takeaway is that when sophisticated threat actors find their way into a system or network, the persistence they establish is very rarely relying on a single backdoor.
We saw something similar in the SolarWinds attacks, where the “SUNBURST” backdoor was eventually determined to be only one of the multiple backdoors used by the infiltrators.