Suspected Chinese-Sponsored Cyber Espionage Actor Intensifies Taiwanese Operations
- Suspected Chinese state-sponsored threat actor RedJuliett increased its cyber espionage activities targeting Taiwan.
- These operations use network perimeter exploitation to target various official organizations.
- The hacker group was also seen targeting other states, including South Korea and the United States.
RedJuliett, a likely Chinese state-sponsored group focusing on government, academic, technology, and diplomatic organizations in Taiwan, was seen intensifying its cyber espionage activities by Insikt Group’s security researchers. The report says RedJuliett activities were observed from November 2023 to April 2024.
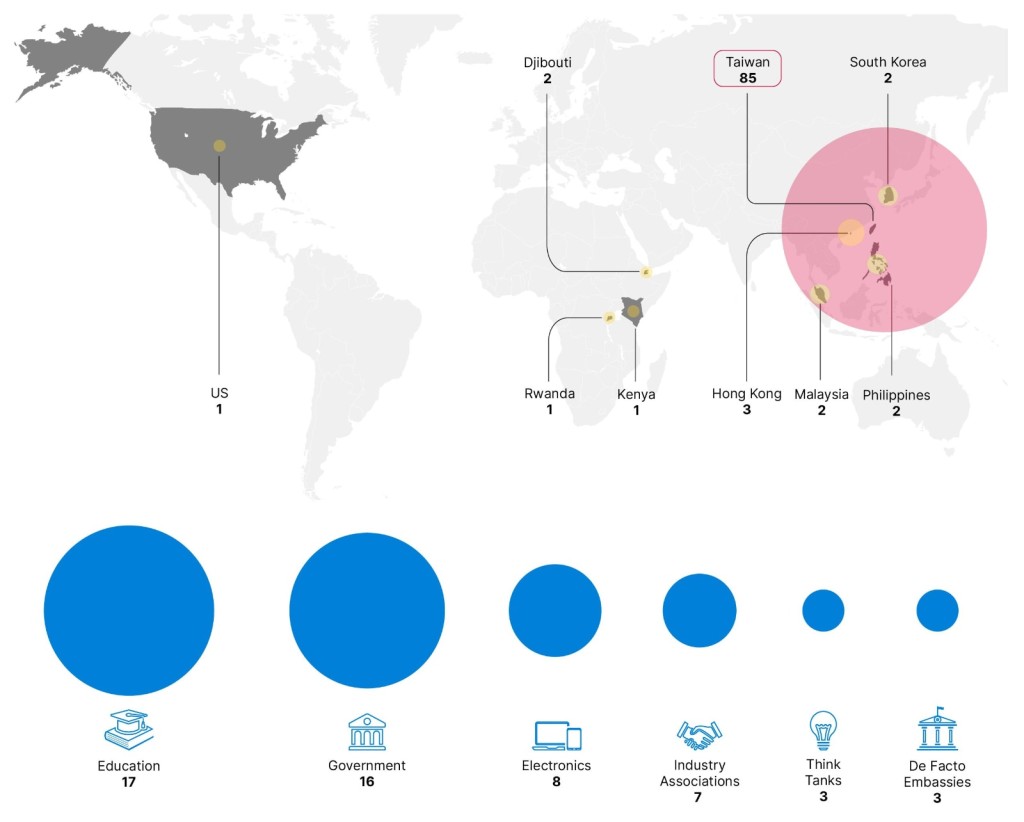
The threat actor compromised 24 organizations, including government organizations in Taiwan, Laos, Kenya, and Rwanda, and conducted network reconnaissance or attempted exploitation against over 70 academic, government, think-tank, and technology organizations and multiple de facto embassies in Taiwan.
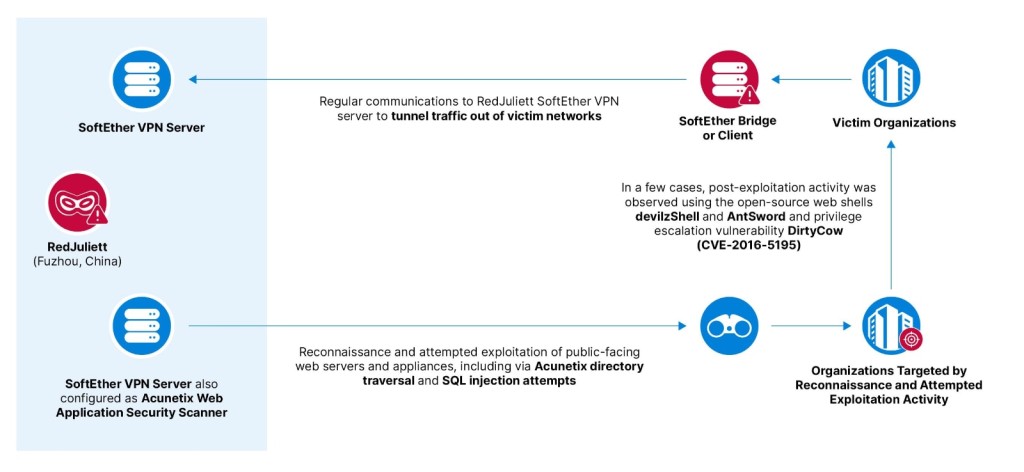
The cybercriminal operational infrastructure is administered using the open-source SoftEther VPN and uses leased servers under the threat actor’s control and Taiwanese universities’ compromised infrastructure.
RedJuliett exploited known vulnerabilities in Internet-facing network edge devices such as firewalls, enterprise virtual private networks (VPNs), and load balancers for initial access.
Their exploitation techniques include creating a VPN bridge or client-in-victim networks and using Acunetix Web Application Security Scanners for reconnaissance and attempted exploitation. They also attempted structured query language (SQL) injection and directory traversal against Web and SQL applications.
Once inside the breached systems, the hackers used open-source Web shells and exploited an elevation of privilege flaw in the Linux operating system.
RedJuliett was also seen expanding its operations to compromise organizations in Hong Kong, Malaysia, Laos, the Philippines, South Korea, Kenya, Rwanda, Djibouti, and the U.S. The group likely operates from Fuzhou, China.
Insikt Group says the cyber-espionage group's targeting of multiple critical technology companies underlines the strategic importance of this sector for Chinese state-sponsored threat actors. Their activities align with Beijing's objectives to gather intelligence on Taiwan’s economic policy, trade, and diplomatic relations.
RedJuliett closely coincides with public reporting of Flax Typhoon and Ethereal Panda. First reported by Microsoft in August 2023, Flax Typhoon targeted Taiwanese government agencies, education, critical manufacturing, and IT organizations via living-off-the-land (LotL) techniques and SoftEther. The group abused vulnerabilities in public-facing services and used the China Chopper web shell for persistence and remote code execution.
CrowdStrike's reports on Ethereal Panda present very similar tactics, techniques, and procedures (TTPs) and the group’s use of the open-source Web shell Godzilla.