CFOs in the Crosshairs as Sophisticated NetBird Spear-Phishing Campaign Unfolds
- An unnamed threat actor targets CFOs and finance executives in a new spear-phishing campaign.
- Fake emails are sent to representatives in banking, energy, insurance, and investment sectors.
- Hackers leverage the legitimate WireGuard-based remote-access tool NetBird to gain remote access.
A multi-stage operation attempts to deploy NetBird onto compromised endpoints to establish persistent, encrypted backdoor access, targeting Chief Financial Officers and other finance executives across banking, energy, insurance, and investment sectors worldwide.
Detailed by Trellix Advanced Research Center, this newly uncovered spear-phishing campaign leverages a legitimate WireGuard-based remote-access tool via fake emails.
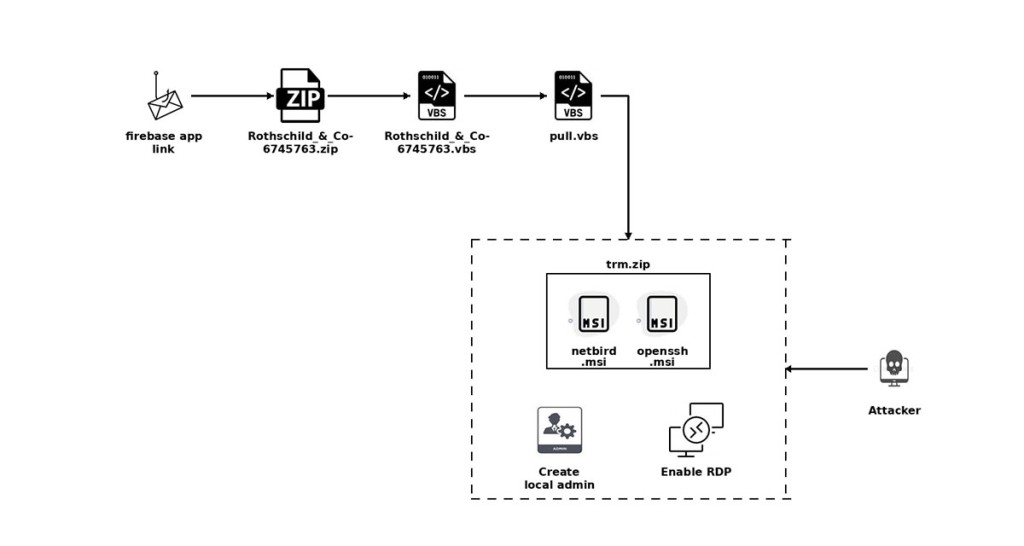
The campaign begins with a highly targeted email masquerading as a recruitment opportunity from Rothschild & Co, enticing recipients with a supposed leadership position.
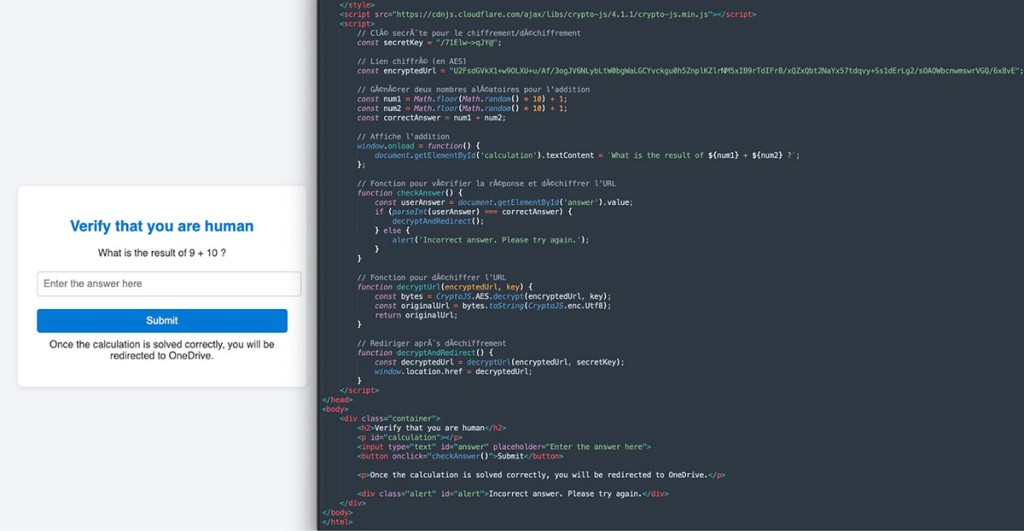
Instead of delivering a PDF as promised, the message links to a Firebase-hosted phishing site hidden behind a custom math CAPTCHA, designed to evade detection by standard security tools.
Upon solving the CAPTCHA, the victim receives a ZIP archive containing a VBS script. Execution of this script triggers a waterfall sequence that downloads additional payloads, ultimately installing both NetBird and OpenSSH silently.
The malware establishes a concealed local administrator account, enables Remote Desktop Protocol (RDP), modifies firewall settings, and ensures persistence by auto-starting NetBird on boot. Attackers gain encrypted remote access channels while maintaining a low profile to avoid detection.
This campaign demonstrates an escalation in attacker sophistication. By leveraging trusted remote access tools, custom CAPTCHA gates, and staged scripting, adversaries are subverting traditional phishing defenses and endpoint protection strategies.
Trellix notes overlaps in infrastructure with known nation-state actors, but to date, it has not attributed the activity to any specific threat group.
The geographic reach is significant, spanning financial organizations in Europe, Africa, Canada, the Middle East, and South Asia. Notably, France’s securities commission (AMF) has issued a parallel warning about similar lures.