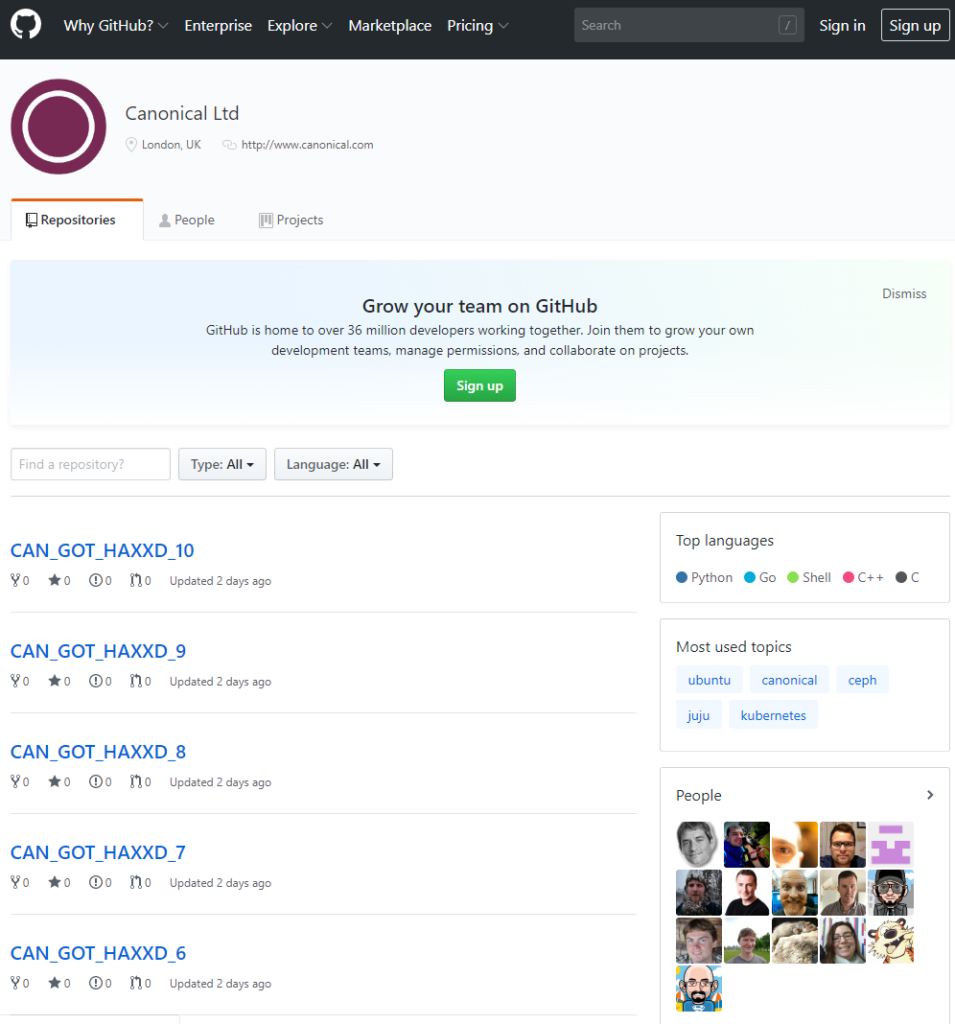
Canonical’s GitHub Account Gets Hacked, and Its Page Gets Defaced
- Canonical losses GitHub account to hackers, and they deface it with empty repositories.
- The company has deleted the repos and is currently conducting an investigation on the matter.
- There seems to be no real damage or malware infection, as hackers likely only wanted to make a statement.
An unknown hacker or group of hackers managed to take over the GitHub account of Canonical, creating 11 empty repositories titled “CAN_GOT_HAXXD”. Canonical is the company behind the most popular Linux distribution out there, Ubuntu. Besides Ubuntu though, Canonical also offers centralized system management solutions, cloud services, and several products for the enterprise market. That said, the GitHub interruption has not affected only home users, but a wide range of customers of the Isle of Man company. Canonical has confirmed the breach with the following statement:
“We can confirm that on 2019-07-06 there was a Canonical owned account on GitHub whose credentials were compromised and used to create repositories and issues among other activities. Canonical has removed the compromised account from the Canonical organization in GitHub and is still investigating the extent of the breach, but there is no indication at this point that any source code or PII was affected.”
image source: web.archive.org
While the company reassures that no real damage was done, hackers accessing their official GitHub could open up the way to infecting the repositories with malware. In the past, we have seen hackers replace the contained files with malicious ones named exactly the same, so no one would realize the hack before the infections took place. This time however, and since the hackers decided to deface the page, it looks like they cared more about making a statement, and less about doing real damage to Canonical and its clients.
Still, the Ubuntu security team is currently carrying out an in-depth investigation to figure out not only the extent of the breach, but also how the hackers managed to get their hands to their GitHub account in the first place. This is not the first time that Ubuntu sustains a breach and defacing, as similar events took place in the distribution’s forums in 2013, twice in 2016, and one more time in 2018. The worst-case scenario for Ubuntu would be a breach that would result in the planting of a backdoor, and while other distros like Linux Mint have suffered this fate, Ubuntu has not confirmed something like that yet.
Finally, Bad Packets security firm has recently warned about a massive scanning operation for exposed git config files, so this latest breach incident could be related. However, this has not been confirmed by Canonical yet, and we’ll probably have to wait for a while to get to know more details about what exactly happened, and how.
Are you using Ubuntu? Do you trust Canonical? Let us know in the comments down below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.