BrowserVenom Malware Targets AI Enthusiasts via DeepSeek Google Ads Malvertising
- A new malicious campaign is distributing malware through a fake DeepSeek-R1 LLM environment installer.
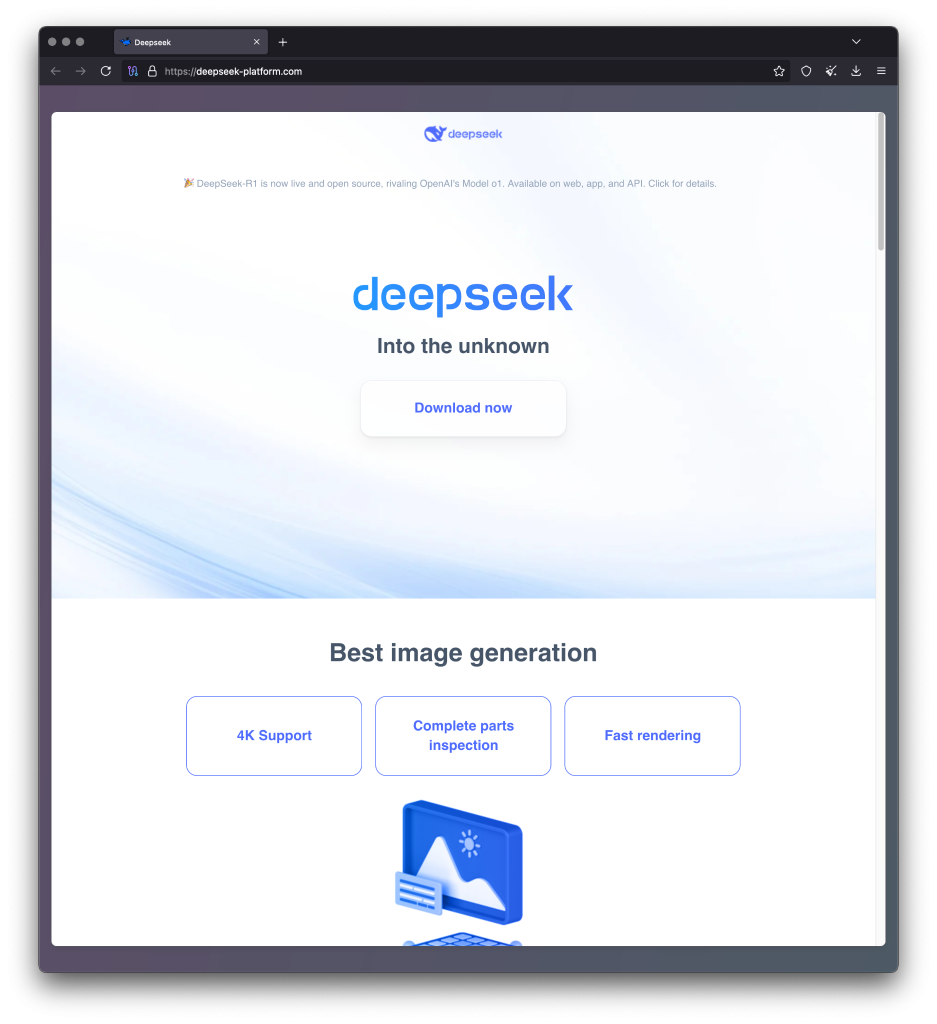
- Attackers use a phishing site promoted in the search results via Google Ads that mimics the official DeepSeek homepage.
- The BrowserVenom implant is ultimately deployed, resulting in the manipulation of the victim’s network traffic and data harvesting.
A new malware campaign leverages the popularity of AI chatbots, specifically targeting DeepSeek-R1 users. This sophisticated attack employs malvertising tactics to distribute the "BrowserVenom" implant through a fake DeepSeek website promoted via Google Ads as the top search result.
The malware functions to manipulate victims' browsing activity by forcing traffic through a proxy controlled by the attackers, Kaspersky researchers have uncovered.
The phishing attack begins when a user searches for DeepSeek-R1 and clicks on the malicious ad, leading them to a fake website (deepseek-platform[.]com) with a CAPTCHA verification.
Victims are lured into downloading what appears to be the DeepSeek installer, only to receive a malicious executable named AI_Launcher_1.21.exe. Executing this binary opens a fake CAPTCHA window that afterwards presents installation buttons for malware-laced LM Studio and Ollama software.
This installer initiates a second-stage implant, BrowserVenom, which then attempts to bypass Windows Defender by excluding certain folders and downloads additional malware from a malicious domain using PowerShell commands.
It also reconfigures web browsers to route traffic through a hardcoded proxy, granting attackers access to encrypted network transmissions.
BrowserVenom poses a significant threat by allowing attackers to intercept sensitive information, monitor browsing activities, and manipulate internet traffic.
This campaign is believed to be orchestrated by Russian-speaking threat actors, evidenced by the coding language used on its phishing and distribution sites.
The campaign has already affected users in Brazil, Cuba, Mexico, India, Nepal, South Africa, and Egypt, making it a global concern. Its use of malvertising through legitimate platforms like Google Ads increases its reach and credibility, risking potential harm to unsuspecting users worldwide.