Vulnerabilities in Broadcom WiFi Drivers Open the Door to Remote Code Execution
- Two Broadcom WiFi chipset drivers are vulnerable to validation bypassing and heap buffer overflow.
- There’s an extensive list of 166 vendors who are possibly affected, extending to thousands of devices and millions of users.
- As always, the best way to mitigate the risk of falling victim of exploitation is by updating your software.
Broadcom WiFi chipsets operating on the “w1” and the open-source "brcmfmac” drivers were found to be vulnerable to frame validation bypass and heap buffer overflow. If an attacker creates special WiFi packets and sends them over the chipset, they may be able to execute code on the targeted system without the need of getting authenticated. In the most typical scenario, the flaws would lead to a DoS (Denial of Service) situation. The discovery and disclosure of the vulnerabilities is the work of Hugues Anguelkov, intern of Quarkslab, who spent months in reverse engineering and fuzzing the firmware of Broadcom wireless chipsets.
The vulnerabilities found by the researcher are the following:
CVE-2019-9500: Concerns the “brcmfmac” driver in combination with the “Wake-up on Wireless LAN" functionality. If enabled, a malicious event frame can be constructed to trigger a heap buffer overflow in the “brcmf_wowl_nd_results” function, essentially leading to a remote compromising of the host.
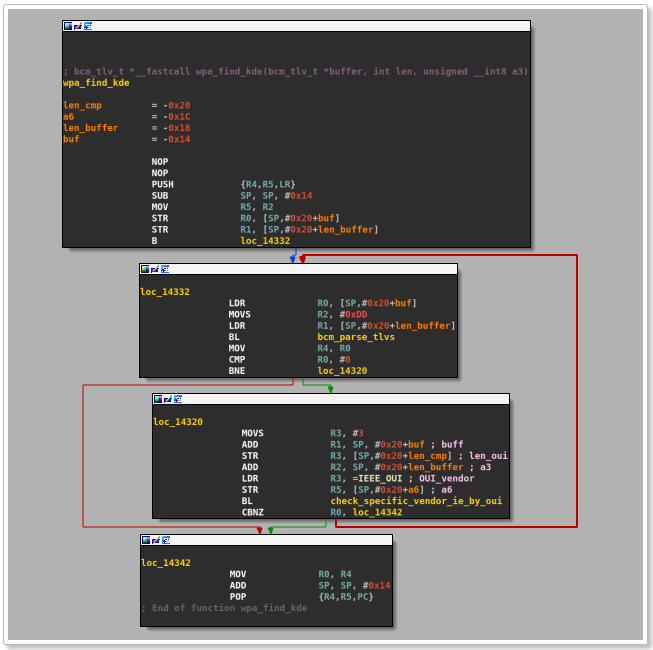
CVE-2019-9501: Concerns the “w1” driver, and allows the triggering of a heap buffer overflow in “wlc_wpa_sup_eapol” by supplying a vendor information element with a data length that is larger than 32 bytes. SoftMAC triggers the flaw in the host’s kernel, while FullMAC points it to the chipset firmware.
CVE-2019-9502: Concerns the “w1” driver and allows yet another heap buffer overflow triggering but this time in “wlc_wpa_plumb_gtk”. The vendor information element data length has to be larger than 164 bytes for this to work. SoftMAC triggers the flaw in the host’s kernel, while FullMAC points it to the chipset firmware.
CVE-2019-9503: Concerns the “brcmfmac” driver and the capacity to receive and process a firmware event frame from a remote attacker without validating it, bypassing the security layer when using a USB WiFi dongle.
image source: blog.quarkslab.com
With Broadcom WiFi chipsets being so common, the above vulnerabilities affect millions of devices and users. Quarkslab has reached out Broadcom and several of the affected vendors since last September to warn them about the flaws, so patching has already taken place in the meantime. That said, the best way to protect yourself from the discovered vulnerabilities is to ensure that your software is up to date. Apple is one of the few to have plugged the weaknesses with the macOS Sierra, High Sierra, and Mojave updates that were rolled out on 15 April, while devices of the Extreme Networks vendor were also confirmed not to be affected.
Have any comments to make on the above? Feel free to leave them in the comments section below, and don’t forget to spread the word about the Broadcom vulnerabilities by sharing this post through our socials, on Facebook and Twitter.