British Russia Expert Keir Giles Targeted in Social Engineering Campaign Leveraging ASPs to Bypass MFA
- A meticulous attack targeted prominent British expert on Russian information operations Keir Giles.
- The threat actor leveraged App-Specific Passwords to bypass multi-factor authentication.
- The attack was linked to a Russian state-backed group tracked as UNC6293.
A novel phishing attack targeting Keir Giles, a prominent British expert on Russian information operations, exploited app-specific passwords (ASPs) to bypass multi-factor authentication (MFA) protections.
Reports by Google’s Threat Intelligence Group (GTIG) and the digital forensic research group Citizen Lab reveal that the attack was attributed to a likely Russian state-sponsored group, tracked as UNC6293. GTIG assesses with low confidence that it is associated with APT29 / ICECAP.
GTIG identified the same methods in an additional campaign targeting other individuals, with a Ukrainian and Microsoft-themed ASP as its focus.
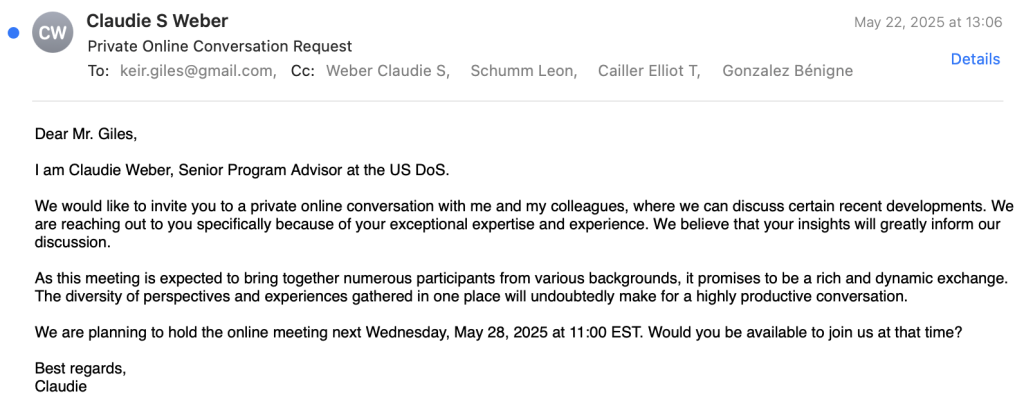
Beginning on May 22, the attackers reportedly impersonated a U.S. State Department official, initiating a sophisticated social engineering campaign designed to establish trust. Over 10 emails were exchanged, building credibility with involvement from seemingly authentic state.gov email addresses.
The core deception involved directing Giles to set up an "MS DoS Guest Tenant" account, purportedly for secure communications.
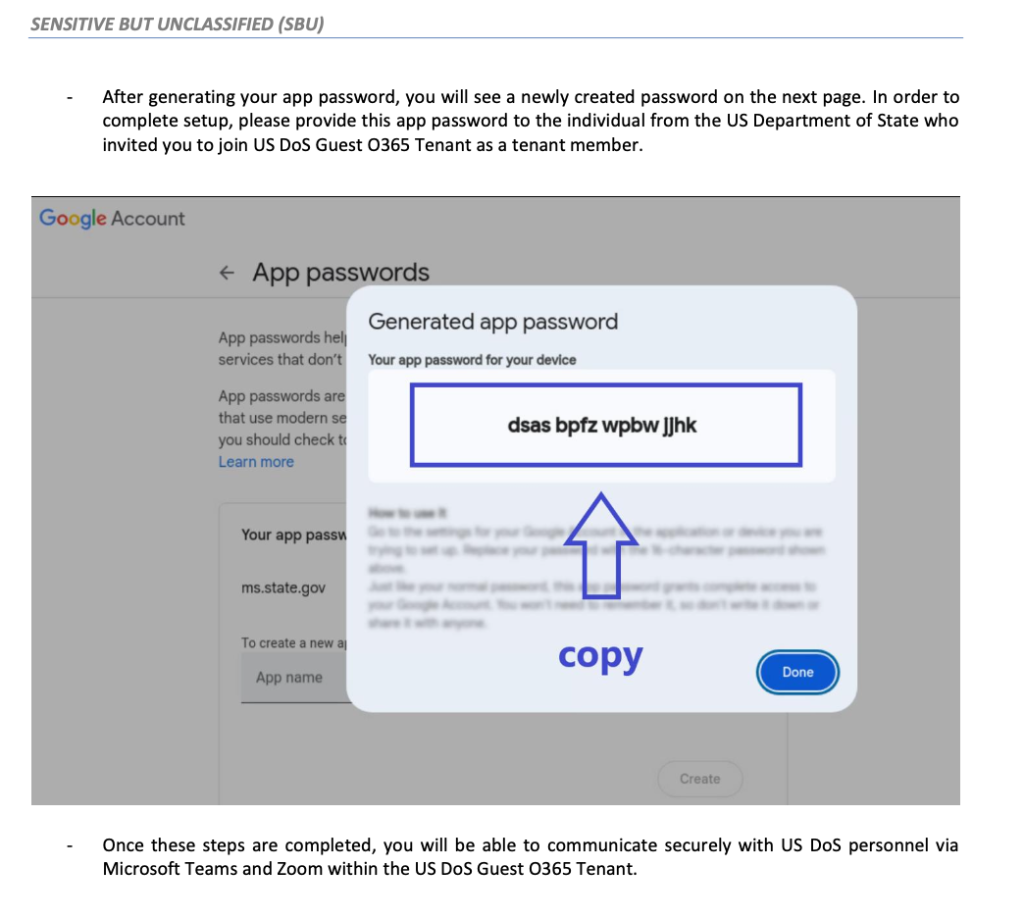
The attackers convinced Giles to create and share ASP credentials under the guise of enhancing access security. These ASPs granted the attackers full and persistent access to Giles' email accounts.
ASPs are typically used when applications cannot support MFA directly, enabling compatibility with accounts secured by MFA.
However, the Citizen Lab noted that Google has been phasing out Less Secure Apps (LSAs) in Workspaces, although users can still generate ASPs for personal Gmail accounts, leaving a potential gap in security.
Analysts believe Giles was the first known target of this particular tactic, suggesting it could gain traction as attackers develop more advanced phishing methods to combat increasing savviness and robust MFA adoption.
Giles expressed concerns over what he described as a significant security gap in Gmail, likening it to "leaving the window open" despite having strong locks.
While there is no vulnerability explicitly linked to ASPs, Google described the incident as a phishing case misusing standard authentication practices.