Brazilian Electric Power Company Extorted by REvil Ransomware Actors
- “Light S.A.,” a Brazilian energy producer and distributor, has fallen victim to a REvil ransomware attack.
- The actors are demanding the payment of $6.95 million in XMR, which will keep the shroud of their anonymity intact.
- “Light S.A.” hasn’t told the public anything about their intentions, and the first signs point to an ongoing negotiation.
The REvil ransomware gang (Sodinokibi) has returned to claim yet another victim, and this time it is “Light SA.” The private Brazilian electrical energy firm has been operating in the country since 1905, covering large areas with vital energy distribution services. Today, it employs 3,732 people and has a revenue of $3.2 billion. According to local media reports, the firm has been struggling with a ransomware infection since last month but tried to keep everything confidential. Due to service disruptions and technical difficulties in the customer services, they were soon forced to admit that something had happened on June 16, 2020.
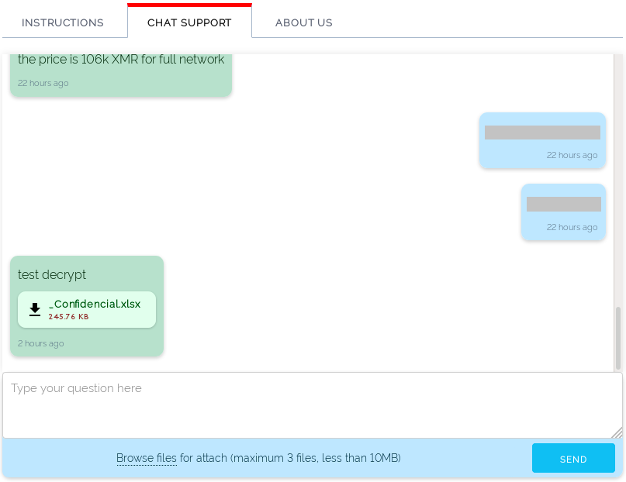
The REvil actors haven’t created a name for themselves by demanding ransoms that are easily covered, and the “Light S.A.” hack is no exception to that. The actors demanded a payment of 107,213.96 Monero (XMR), which is about $6.95 million. As we have analyzed before, the reason why malicious actors are opting for Monero payments is that it is particularly hard to trace or connect with any identity since it uses an obfuscated public ledger that scrambles transaction broadcasts and masks the sources of the requests.
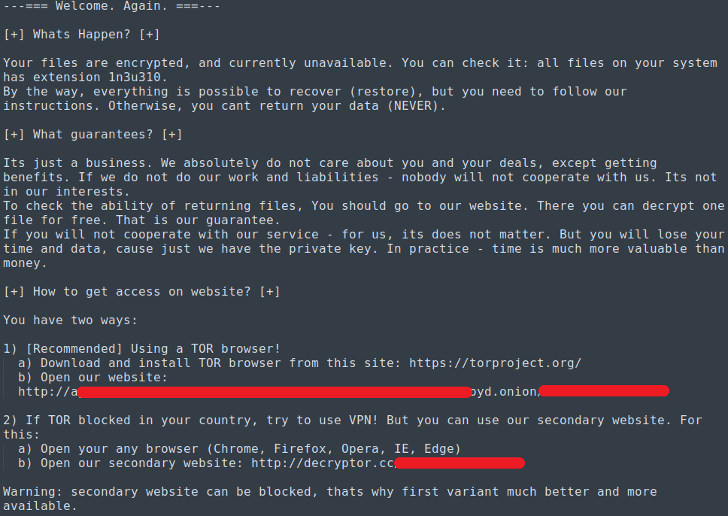
Source: AppGate blog
The firm never mentioned who the actor was, but a recent report by AppGate has connected an associated Sodinokibi sample with that specific attack against Light S.A. The ransom note tries to guarantee that if the ransom is paid, everything will return to normal. Moreover, the actors are offering a live chat communication channel to support the victim and guide them through the payment process. This is clearly an operation set up by professionals, pointing to a RaaS service. AppGate also mentions that the sample they captured was made to exploit the popular Windows flaw “CVE-2018-8453.”
Source: AppGate blog
There’s no word yet about what “Light S.A.” is planning to do, while these developments typically take place behind closed doors and the details surface at a later date, if ever. REvil belongs to a group of actors that exfiltrate data and then gradually leak samples online to raise the level of pressure towards the victim. So far, though, we haven’t seen anything appearing on the dark web yet, so the two parties may be well into the negotiation process.
The most recent REvil attack we covered was that against the Australian beer brewery “Lion,” who was extorted for $800,000. We don’t know if Lion paid or not, but the drink maker has gradually returned to normal production while officially stating that they’re not planning to pay anything to the REvil group. As they declared:
“We do still expect to see some further disruptions as we continue to restore systems. We will continue to work with our team of experts to complete this work as quickly as possible, minimizing any further disruptions, including supply. It remains a real possibility that data held on our systems may be disclosed in the future.”