“BootHole” Flaw in GRUB2 Introduces Secure Boot Attack Risks
- A flaw in GRUB2 could potentially enable a malicious actor to replace the bootloader and take over the device.
- The flaw may have already been under exploitation in the last couple of months, as there has been a suspicious rise in the circulation of nasty bootloaders.
- To address the risks, update your GRUB2 installation, re-install your Linux distro, and apply all incoming updates as soon as they arrive.
Eclypsium researchers have discovered a critical vulnerability in the GRUB2 bootloader, calling it “BootHole.” The flaw could enable a malicious actor to perform arbitrary code execution during the boot process, even if “Secure Boot” is enabled, potentially installing persistent and stealthy bootkits on the target system.
The worst-case scenario would be a near-total control over the victim’s computer, so fixing the flaw as soon as possible is critical.
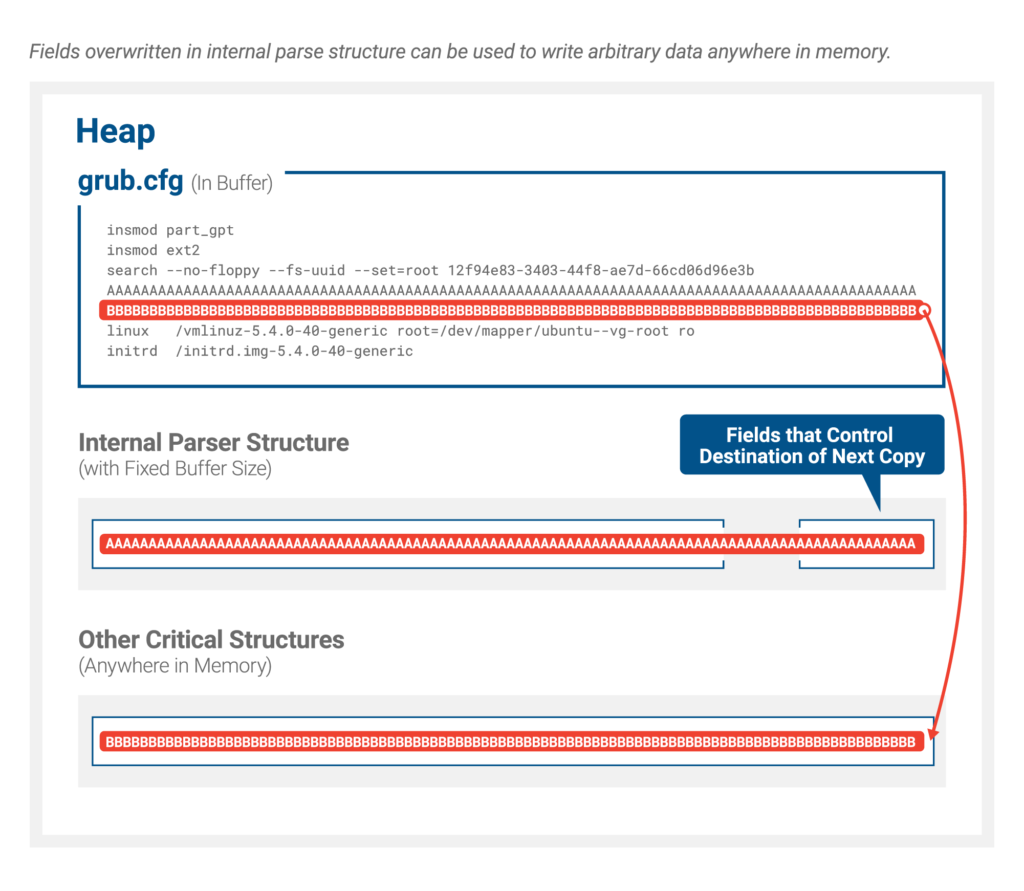
Eclypsium discovered that a vulnerability in the way that GRUB2 parses content from its config file (grub.cfg) could enable someone to replace the bootloader with a malicious version. The altered config file isn’t signed as it should be, and GRUB isn’t even looking for authentication certificates in this case.
This way, the attacker could trigger a buffer overflow vulnerability during the parsing, opening the door to code execution in UEFI. There, they may run malware, alter the boot process, fiddle with the OS kernel, and more. The malicious configuration file has to be planted in the EFI System Partition, so some level of access is required for the attack to work.
Source: Eclypsium
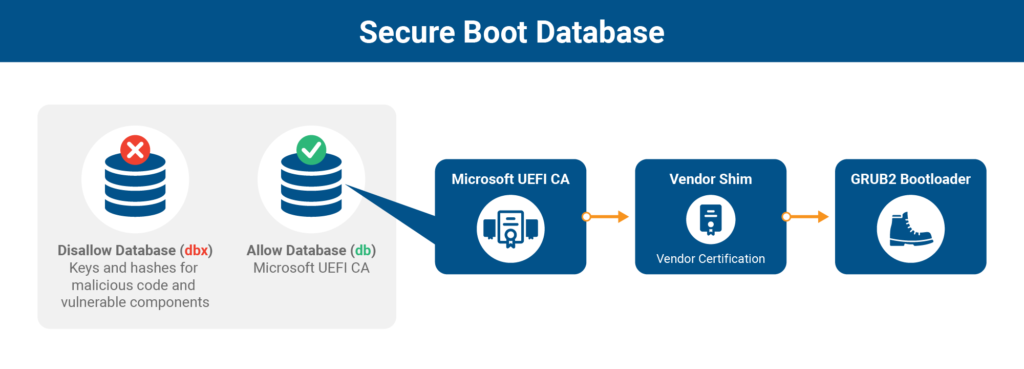
The whole purpose of the existence of UEFI Secure Boot is to protect systems from these types of attacks, but Microsoft’s decision to lock the system with licensing complexities has forced open-source projects to turn to alternative certificate and code verification tools, like shims pointing to Microsoft 3rd Party UEFI CA. With the process getting more complicated as a result, attackers have more chances to find a vulnerability in bootloaders such as GRUB2.
After Eclypsium’s initial finding, Microsoft, Canonical, and Debian researchers have scrutinized GRUB2 security once again and discovered another seven medium-severity flaws, namely CVE-2020-14308, CVE-2020-14309, CVE-2020-14310, CVE-2020-14311, CVE-2020-15706, CVE-2020-15707, and CVE-2020-15705.
Source: Eclypsium
With this information in their hands, the researchers prepared a patched GRUB2 build, which all Linux distributions should receive in the following days, ideally as soon as possible. There has been a rise in the number of malicious bootloaders appearing in the wild lately, so it’s quite likely that threat actors are already exploiting “BootHole.”
Remember, the flaw affects GRUB2, so whether you are using the bootloader to access a Linux system or a Windows partition, it doesn’t make any difference. Both systems are vulnerable.
To address the problem, Linux distributions must update their installers and GRUB2 packages, and new shims will have to be signed by the Microsoft 3rd Party UEFI CA.
For enterprise and server systems, this is going to be a nightmare to handle now, so adding a revocation list with the “reset to default” option for when things go bad would be a good idea.
Read More:
- The Ups and Downs of the Threat Landscape in Q2 2020
- Purism Presents Privacy-Focused “Librem 14” Linux Laptop
- Microsoft Has Finally Brought Its ‘Defender’ Antivirus Solution to Android and Linux