BlueNoroff APT Campaigns GhostCall and GhostHire Target Web3, Venture Capital Sectors via Advanced Social Engineering
- Dual campaigns: The financially motivated BlueNoroff APT group is running two sophisticated campaigns targeting the Web3 and venture capital sectors.
- Social engineering: GhostCall uses fake video calls to lure executives, while GhostHire targets developers with malicious skill assessments delivered via Telegram and GitHub.
- Complex malware ecosystem: The campaigns deploy multiple, multi-stage macOS and Windows malware chains, including extensive infostealing suites and backdoors.
The BlueNoroff APT group, a threat actor known for its financially motivated cyber operations, has launched two new highly sophisticated campaigns named GhostCall and GhostHire. These operations specifically target executives and developers within the Web3, blockchain, and venture capital industries.
GhostCall and GhostHire Attack Vectors
The BlueNoroff APT campaigns leverage advanced social engineering and a complex ecosystem of malware to achieve their objectives. The campaigns demonstrate the actor's increasing proficiency in multi-platform attacks, with a significant focus on compromising macOS systems.
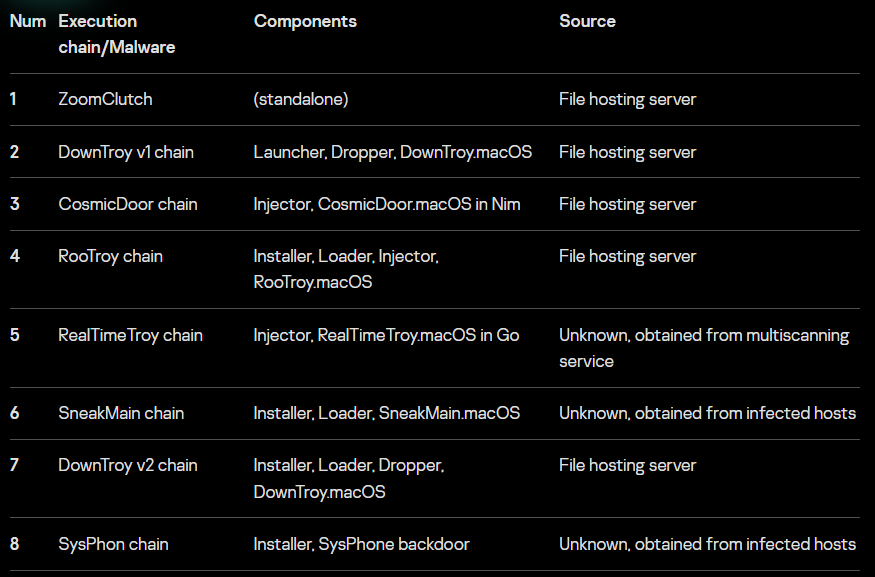
Security researchers at SecureList by Kaspersky discovered seven multi-component infection chains, a keylogger, and a stealer suite that exfiltrates cryptocurrency wallets, Keychain data, package managers, infrastructure setups, as well as cloud platforms and DevOps details, along with notes, API keys for OpenAI, collaboration application data, and browsers, messengers, and Telegram credentials.
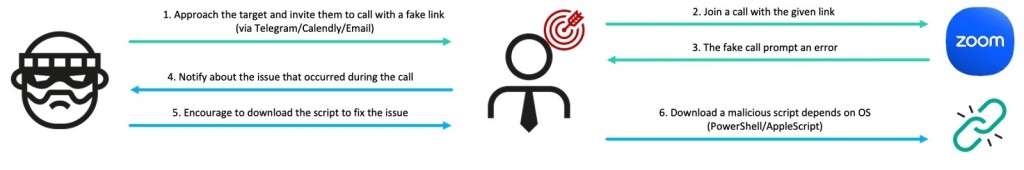
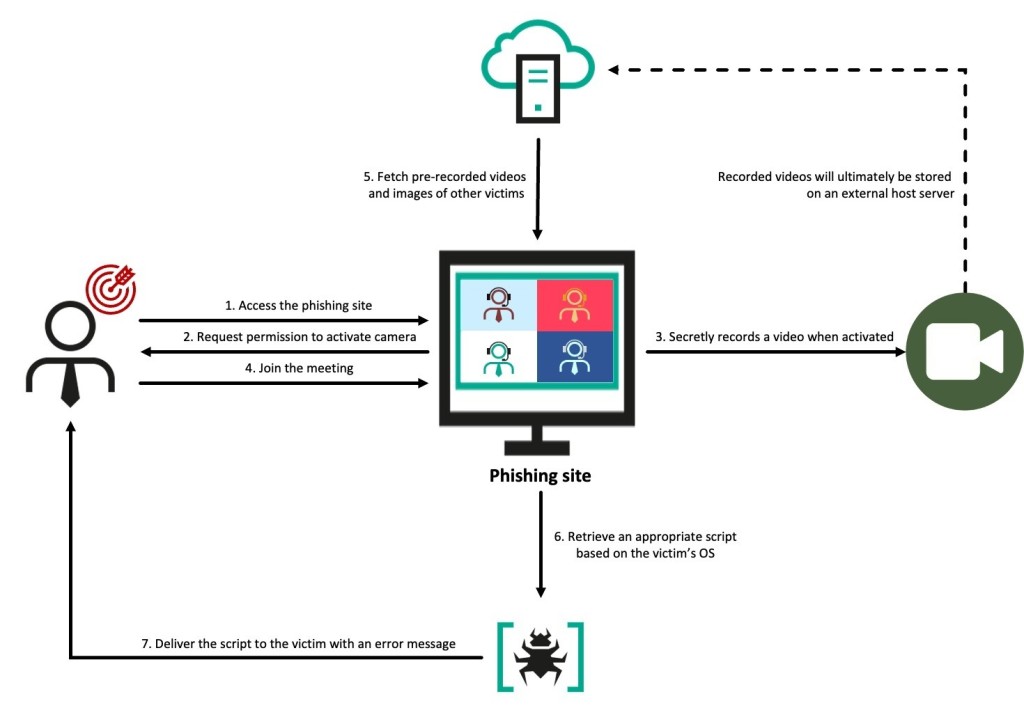
The GhostCall and GhostHire attacks utilize distinct but equally deceptive initial access methods. In the GhostCall campaign, attackers impersonate venture capitalists and engage targets in fake Zoom or Microsoft Teams meetings.
During these calls, which use pre-recorded videos of other victims, the target is tricked into downloading a malicious script disguised as an urgent software update. Microsoft, Huntability, Huntress, Field Effect, and SentinelOne have already tackled GhostCall, and SecureList covers newly discovered malware chains and provides deeper insights.
On Windows, the attack uses the ClickFix technique, where a seemingly harmless code snippet from a legitimate domain delivers the malware.
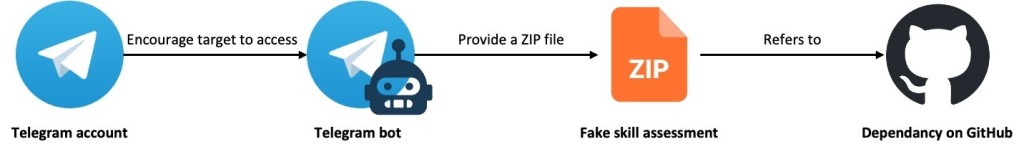
The GhostHire campaign targets developers with fake job opportunities, pressuring them to complete a timed "skill assessment" by downloading and running a malicious project from a GitHub repository. Both methods lead to the deployment of multi-stage APT malware chains.
Evolving Malware and Implications for Cyber Espionage
These campaigns feature an extensive and evolving arsenal of malware. Researchers have identified at least seven distinct infection chains, including backdoors such as RooTroy and CosmicDoor, and an extensive infostealing suite called SilentSiphon.
This suite is designed to harvest a wide array of sensitive data, from browser credentials and crypto wallets to cloud service configurations and even OpenAI API keys. The use of generative AI to enhance social engineering lures and potentially assist in script creation indicates a significant advancement in the group's operational efficiency.
This evolution in cyberespionage tactics poses a severe threat to organizations and individuals in the high-value financial technology sector.
In July, Cofense reported a fake Zoom call phishing campaign that used interactive meeting participants to steal user credentials.
Earlier this year, the Lazarus Group, also known as APT38, scammed Web3 developers via fake LinkedIn jobs, redirecting users to malware websites. In May, reports said LinkedIn crypto job seekers could be members of North Korean cybercriminal groups.