Bluehost Plagued by Multiple Information Leaks and Account Takeover Vulnerabilities
- Five popular hosting service providers were found to be 'easy to hack' by an independent researcher.
- The vulnerabilities allow account data leaks and in some cases, complete account takeover.
- The hosting companies claim that fixes are underway, with their reputation already having taken a blow.
As revealed by Paulos Yibelo, who worked with the support of Website Planet, five popular website hosting services are plagued by highly severe vulnerabilities that can result in account takeover. The service providers that were analyzed and found to be problematic in multiple levels include Bluehost, Dreamhost, OVH, iPage, and HostGator, all popular and widely used platforms.
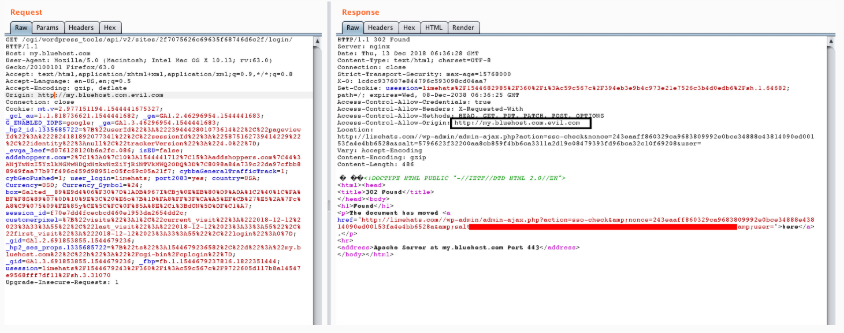
First and foremost, Yibelo tested the CORS policy of Bluehost and found that it accepts vague values while considering only parts of the strings sent. This is an obvious case of 'loose' CORS policy that makes the bypassing of filters by attackers easier, and setting up a malicious subdomain elsewhere that could communicate with the Bluehost-hosted website and retrieve information through CORS requests. The information that can be stolen this way includes emails, first and last names, the location of the registered user, access tokens, and more.
Source: websiteplanet.com
Proceeding further, Yibelo discovered that it is possible to change the email address of the registered user and then reset the password, essentially taking over the account. This is achieved through a vulnerability from Bluehost’s side that allows certain requests to be processed without validation. These requests are sent through JSON, without the attacker using a Flash-powered browser whatsoever. The verification absence is present in the scheme/protocol that allows the reading of traffic through LAN or Wi-Fi as well. This way, an attacker can intercept the traffic data, and even bypass the SSL/HTTPS encryption step, so the resulting text is unencrypted.
Similar findings concern the Dreamhost service that was found to disclose account information via XSS, allowing the changing of the account email and password through a CSRF (cross-site request forgery) attack. The same information leak problems through CORS misconfigurations and API communication was found in HostGator, while OVH seems to also allow attackers to read API contents through a CSRF protection bypassing method based on the use of Flash again.
As the security research reports, all five web hosting services can be easily hacked, a claim that is alarming, to say the least. Dreamhost has responded by thanking the team for sharing the hacking details so they can plug the mentioned vulnerabilities, preventing attackers from leveraging their platforms in the future. HostGator and iPage have also publicly assured people that they are already taking steps to patch the issues and provide safer services to their clients.
Would you trust any of the above services today? Let us know in the comments below, and don’t forget to like and share this story through our socials, on Facebook and Twitter.