The “Black Rose Lucy” Ransomware Is Back Now and Targets Mobile Platforms
- CheckPoint has discovered an Android version of the “Black Rose Lucy” ransomware.
- The malicious actors are pretending to be the FBI, threatening the victim with legal prosecution.
- The ransomware isn’t particularly advanced, but it comes with more than enough functions to do much damage.
A new version of the “Black Rose Lucy” ransomware has been spotted on the wild, and it seems to be targeting Android devices now. This is a malware family that first came to light in September 2018, when Check Point discovered it. However, it never managed to become very popular in the scene. Now, the same team of researchers is reporting that Lucy has returned and has a bag of tricks to fool its victims.
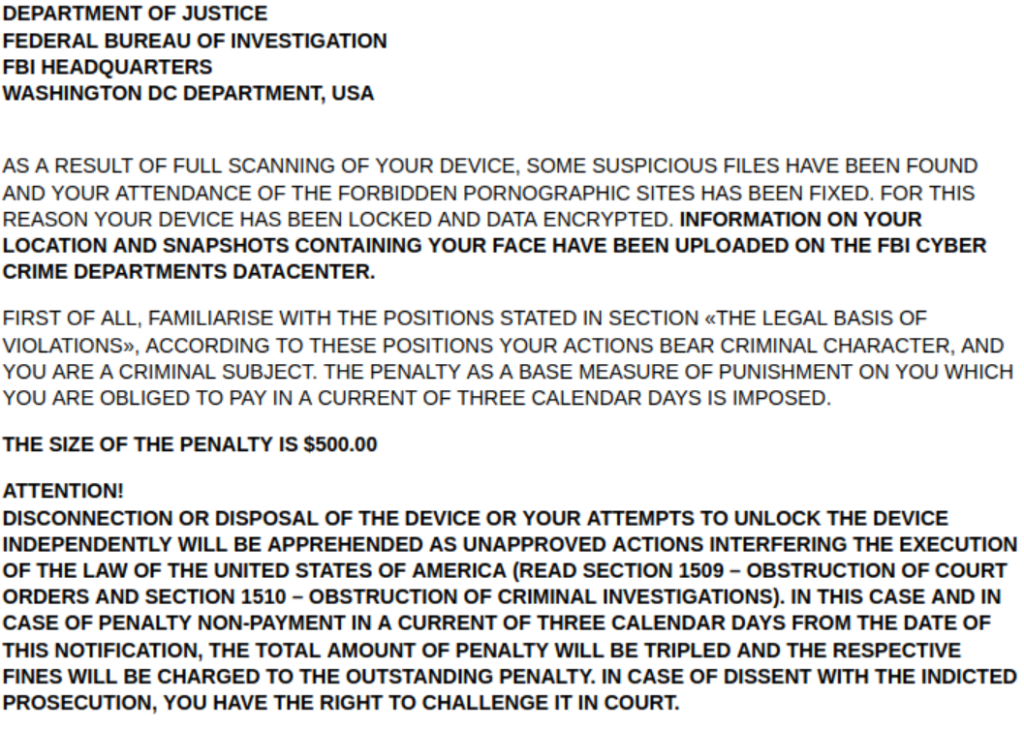
First of all, Lucy is to be found in unofficial APK sources, so its channels of distribution don’t include Google Play. The researchers located more than 80 samples of the new ransomware on social media platforms, where actors are sharing links, as well as in IM app groups. When victims download the ransomware, they get a message that supposedly comes from the FBI, warning them about the discovery of pornographic content on their device. The ransomware then locks the files by encrypting them using the AES algorithm and presents this as part of the FBI action.
Source: CheckPoint Research
Supposedly, the victims had received a $500 penalty due to the possession of the inappropriate material, so they are requested to make the payment within three calendar days. The message warns victims that trying to unlock the device themselves or not paying would constitute a further breaking of the law, resulting in the tripling of the fines.
The victim ends up with files carrying the “.Lucy” extension, while from a technical perspective, the ransomware is similar to what it used to be when it was discovered. All device directories, the ‘/storage,’ and even the ‘/sdcard’ are scanned and encrypted, so nothing is left out. The researchers have noticed that Lucy begins the encryption process with a false key, which could be an attempt to mislead malware analysts.
Source: CheckPoint Research
As for the C2 infrastructure, four servers are hardcoded in Lucy’s code, namely apsoinasj[.]in, 9120qwpsa[.]in, a0h12p14k[.]in, and qeoq0r1hgf03ds[.]in. The malware rotates among them, and there’s a unique API for calling each of them. As for the commands sent from the C&C server to Lucy, these include the calling of a phone number, the fetching of the scanned directories, initiation of encryption, decryption, decline payment, fetch installed apps list, open a remote shell, delete encryption keys, and even to delete Lucy itself.
As always, we recommend paying attention to where you download your mobile apps from, as most malware comes from unofficial app stores. Besides, a security solution means an extra layer of protection.