Beware of Fake Disney+ Activation Pages Leading to Pornographic Scams
- Fake activation pages for popular streaming services like Disney+ redirected to malicious content, urging victims to call the scammers.
- These pages were properly indexed on Google via complex SEO techniques, adding legitimacy to the scam.
- The cybercriminals’ end goal was to steal bank account funds or extort the victims.
Cybercriminals have created fraudulent Disney+ activation pages that redirect unsuspecting users to a pornographic scam. Unlike previous scams relying on paid ads, this scheme uses Search Engine Optimization (SEO) exploitation to place bogus sites within organic search results, a new report from Malwarebytes said.
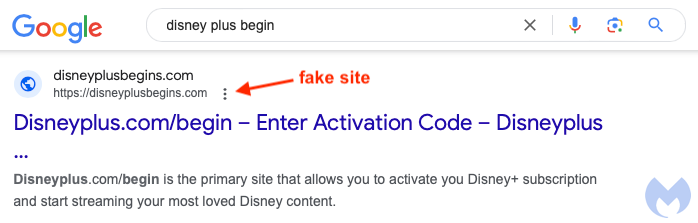
These fake pages are being improperly indexed on Google due to sophisticated SEO techniques, appearing in search results when users seek to activate subscriptions on streaming services, particularly when attempting to authenticate new TV devices.
These fraudulent sites mimic legitimate activation processes by prompting users to enter the code displayed on their screens when activating services like Disney+, Netflix, or Prime Video.
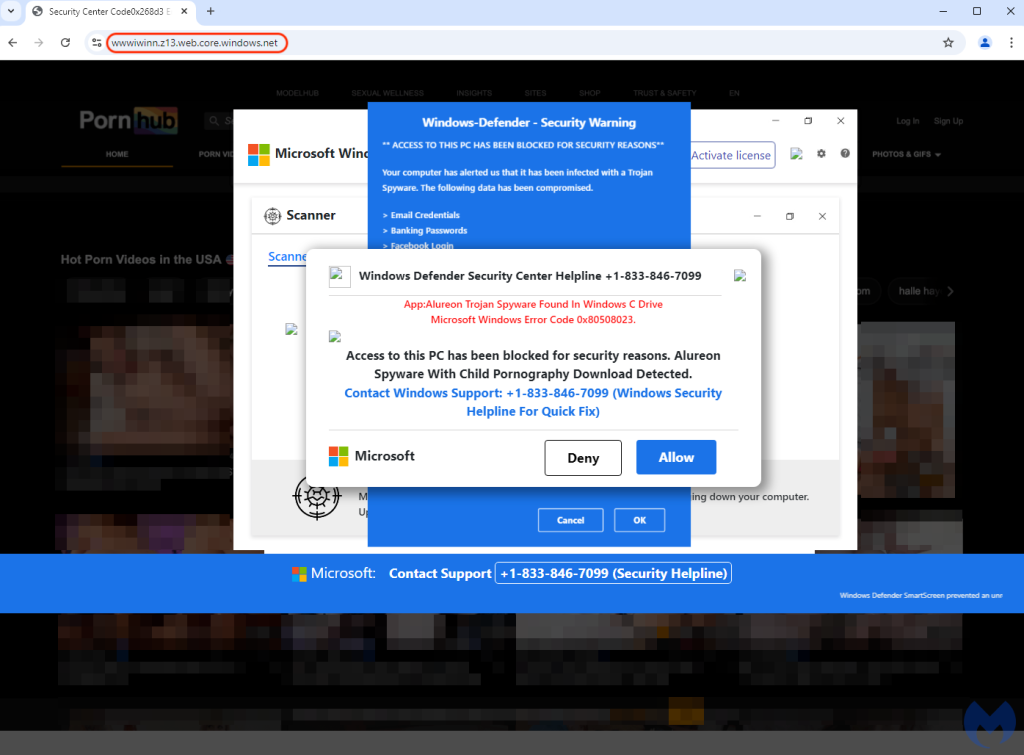
The fake websites mimic genuine activation pages designed to look similar to the official ones. For example, disneyplusbegins[.]com accurately copies the Disney+ activation page but redirects users to a malicious Microsoft Azure-hosted site.
The page contains a background image with pornographic material, as if it were from sites victims may have visited. A counterfeit Windows Defender alert claims that child pornography has been downloaded, prompting users to call a provided number.
This scare tactic is intended to induce panic and prompt users to contact scammers, who then impersonate Microsoft support.
Upon calling, scammers masquerading as Microsoft representatives sought to remotely access the victim's computer. Their ultimate goal is either to steal funds directly from bank accounts or extort money through fraudulent means.
The main recommendation in this case is always to verify the URL to ensure it matches the official website's domain.
In the past months, fake Slack advertisements deploying malware were introduced gradually via Google Ads to avoid detection.
Also, prominent textbook publishers filed a lawsuit in a federal court accusing Google of promoting pirate sites that sell infringing copies of their textbooks, claiming Google did not do enough to prevent ads for infringing works from appearing in Google’s search results.
What’s more, two phishing sites masquerading as official ‘Google Safety Centre’ pages that deployed malware instead of offering Authenticator were indexed in Google Ads as genuine websites.