BBC Reporter Contacted by Medusa Ransomware for Insider Access in Cybercriminal Recruitment Attempt
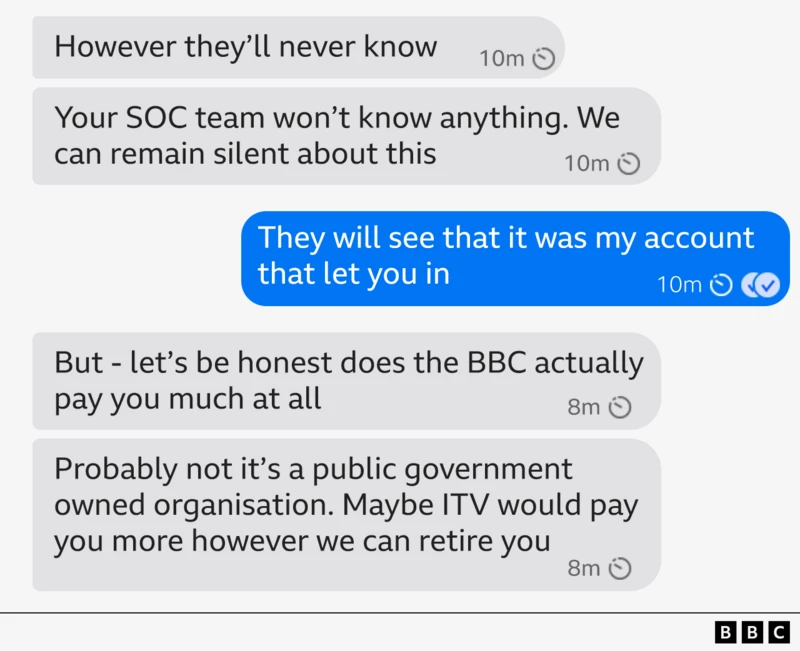
- Insider recruitment: A BBC cyber correspondent was offered a percentage of a future BBC ransom payment in exchange for internal network access.
- Medusa intentions: The individual estimated making millions by hacking the BBC via the obtained corporate login credentials.
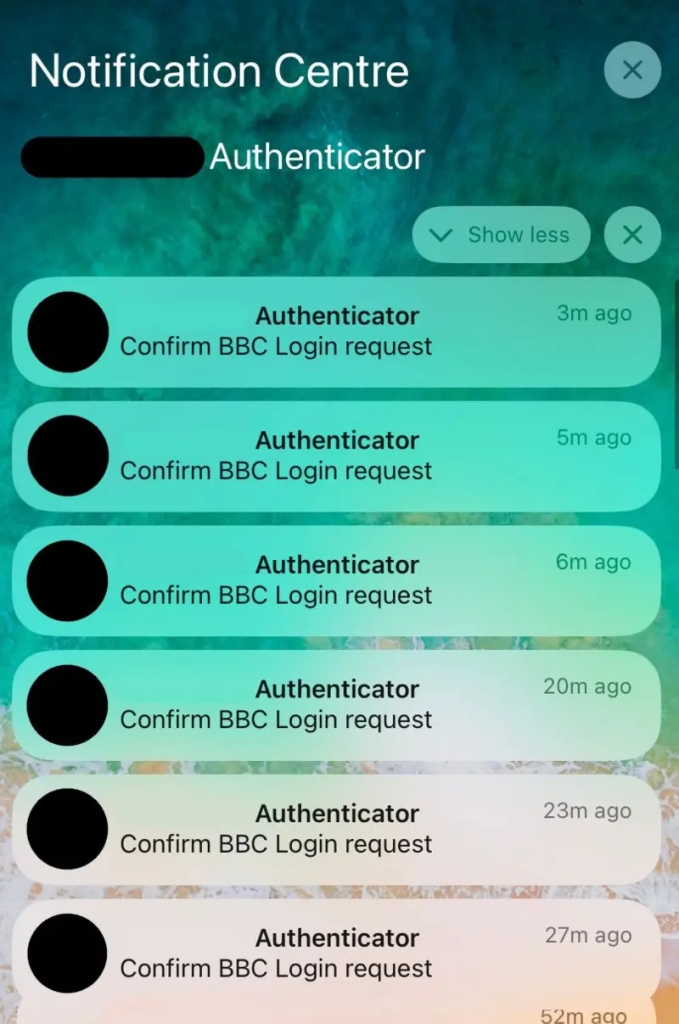
- Hacker tactics: The Medusa members used pressure tactics and MFA bombing to gain access after their initial offer was stalled.
Cyber correspondent Joe Tidy was the target of a brazen BBC cyberattack attempt, in which an individual claiming to be from the notorious Medusa ransomware group tried to recruit him via the encrypted app Signal as a malicious insider.
Escalation and Aggressive Tactics
BBC employee Joe Tidy was pinged on Signal in July by someone claiming to be a "reach out manager" for the notorious Medusa gang, western, and the only English speaker in the team. "If you are interested, we can offer you 15% of any ransom payment if you give us access to your PC," the BBC reports, citing a message from someone calling themselves Syndicate.
After the reporter engaged with the operative under the guidance of BBC editors, the criminals detailed their plan to hack the BBC via the employee’s login details and security code, deploy ransomware, and request a Bitcoin ransom. To prove their identity, they provided a link to Medusa's darknet site.
Later on, Syndicate estimated the team could demand tens of millions in ransom and upped their offer. "We aren't sure how much the BBC pays you, but what if you took 25% of the final negotiation as we extract 1% of the BBC's total revenue? You wouldn't need to work ever again."
The criminals claimed to have successfully used insiders in previous attacks against a U.K. healthcare company and a U.S. emergency services provider. "You'd be surprised at the number of employees who would provide us access," Syndicate said.
When the reporter stalled, the criminals escalated their tactics. They initiated an "MFA bombing" attack, flooding the reporter's phone with login verification requests in an attempt to coerce him into granting access accidentally.
However, they followed with an apology. "The team apologises. We were testing your BBC login page and are extremely sorry if this caused you any issues."
This aggressive move demonstrates the operational methods hackers use when initial social engineering attempts fail, presenting a significant challenge to insider threat cybersecurity protocols.
Highlighting a Pervasive Threat
The direct approach to a journalist, whom they mistakenly believed had high-level IT access, underscores the lengths to which these groups will go to establish a foothold within a target organization.
This event serves as a critical case study on the evolving nature of cyber threats, where external attackers actively seek to cultivate internal accomplices, moving beyond purely technical exploits.
In March, RansomHub was linked to Medusa, Play, and BianLian Ransomware groups via shared EDRKillShifter use.