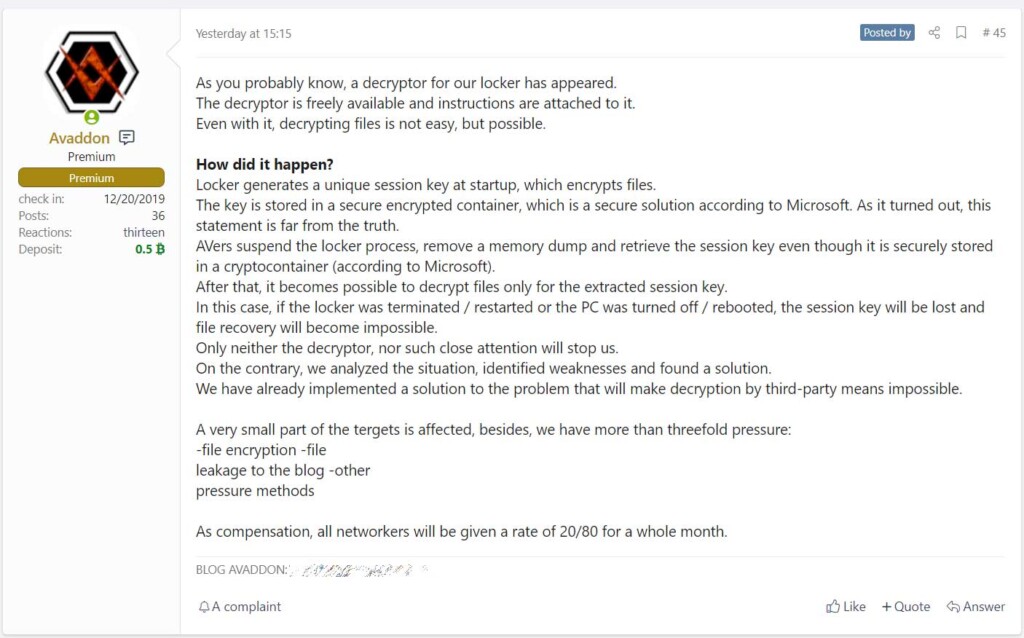
Avaddon Had a Flaw That Allowed Free Decryption but It’s Been Fixed Now
- Avaddon has fixed a flaw that allowed victims to retrieve the encryption/decryption key.
- The researchers who discovered the flaw and released a decryptor shared all technical details publicly.
- The ransomware gang says this is a minor problem for them either way, as data exfiltration remains the main trouble for victims.
The Avaddon ransomware group has fixed a bug on their malware that could have allowed a victim to recover their files for free. The discovery of the flaw came from two University researchers in Madrid, who released a detailed report on it and developed a working decryptor for the latest versions of the strain.
According to the researchers, the flaw lies in how the ransomware clears the AES256 encryption key that is used for the encryption of the victim’s files. The clearing is not complete, and as such, one can retrieve the key from memory as long as the system hasn’t rebooted.
Avaddon was quick to fix that so the “free decryption” won’t apply to new infections. As the group stated, they previously relied on Microsoft’s promise about the security of the encrypted container in Windows, which was proven to be false.
The solution to the problem has already been implemented. To address the Avaddon operators who have had their attacks rendered worthless due to this discovery, the RaaS will now receive a compensating cut of 20/80 (from the normal 30/70) for the whole month.
As the post mentions, decrypting the locked files for free deals with only a small part of the victims' problem, as this is just another alternative for restoring from backups. In practice, the issue of leaking stolen data onto the Avaddon dark web portal (and from there, everywhere) is obviously a lot bigger. This statement is indicative of the fact that the ransomware itself has taken the back seat, and these groups are now relying a lot more on the data breach aspect of their operations.
We really can't help but point out the mistake made by the Spanish researchers, as publishing the details of the flaw basically enabled the authors of the malware to fix it almost immediately. In our private discussions with ransomware analysts and decrypter developers, we often receive kind refusals to share the specifics of a flaw for this very reason, even if we promise not to leak that info. It’s the standard practice followed by the specific research community, and deviating from it has the negative results seen in this case.