Automotive Data Exposed in Git File Leak at Major Roadside Assistance and Insurance Vendor
- Automotive data leak: An automotive-related vendor’s unsecured Git file exposed over 20GB of data from leading automotive giants.
- Sensitive personal data: One million records exposed PII-related data, including customer names, addresses, phone numbers, and vehicle details.
- Operational documents: Scanned PAN cards, canceled checks, and tax certificates for merchants were also revealed.
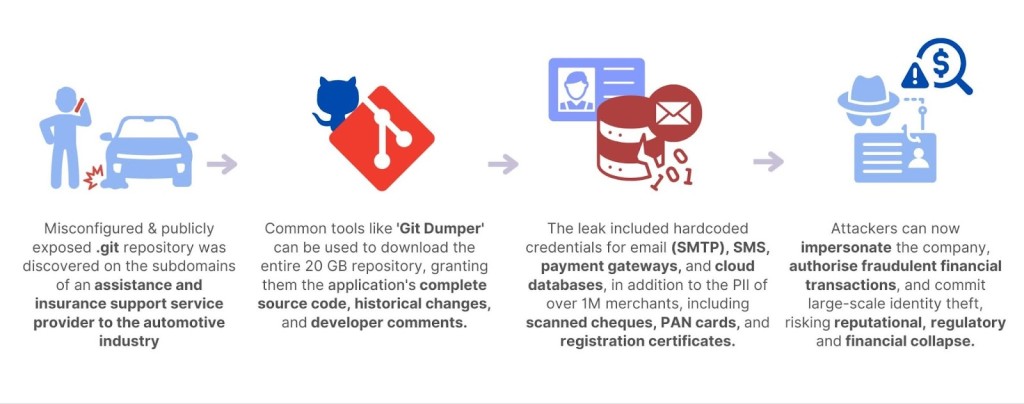
A critical Git file leak at a major roadside assistance and insurance vendor has exposed sensitive data from over 6,700 leading automotive giants due to a misconfigured Git repository, which revealed confidential details of one million records.
Exposed Data
The leak uncovered by CloudSEK’s SVigil platform contained over 20GB of data, including the complete source code of internal e-portals, hardcoded credentials, and more than one million personally identifiable information (PII) records.
The PII and sensitive financial documents belonging to over 6,700 vehicle merchants and their customers included:
- Customer PII: Full Names, Addresses, Mobile Numbers, and Vehicle Details.
- Sensitive Merchant Documents: Over 6,000 scanned cancelled cheques, 6,000 service tax certificates, and 6,000 official registration documents.
- Official ID Documents: Over 2,000 scanned PAN cards (India's equivalent of a Social Security Number) and dealer photographs.
Attackers could gain access to the complete source code of the company's e-portals, as critical credentials were found embedded in the code:
- email (SMTP) credentials
- SMS gateway secrets
- payment gateway tokens
- cloud database keys
This month, TechNadu reported on a flaw in the web portal of a “widely known automaker with several popular sub-brands” that allowed remote car unlocking vulnerability and access to 1,000 dealerships.
Implications
This automotive data breach has vast implications for entities relying on the compromised vendor. These vulnerabilities present attackers with avenues to conduct large-scale phishing campaigns, impersonate the company, trigger unauthorized transactions, and infiltrate cloud databases.
Furthermore, the leaked information lays bare the company’s core development architecture, allowing attackers to engineer future breaches.
Recommended Actions
To address such incidents, organizations must implement secure development practices by ensuring that .git folders remain inaccessible in production environments. Additionally, implementing key rotation policies and monitoring supply chain vulnerabilities can reduce exposure.
Regular audits, up-to-date employee training, and third-party risk assessments are essential components of a robust cybersecurity strategy.