‘Automatic Call Recorder’ App Exposed Thousands of Conversation Clips
- Users of the "Automatic Call Recorder" app have had their private calls exposed via an unprotected AWS bucket.
- The exposure time was at least 10 days, so it is unlikely that hackers haven’t scrapped the 300 GB of accessible data.
- The database has been secured, and the flaw has been patched via an update from the app’s developer.
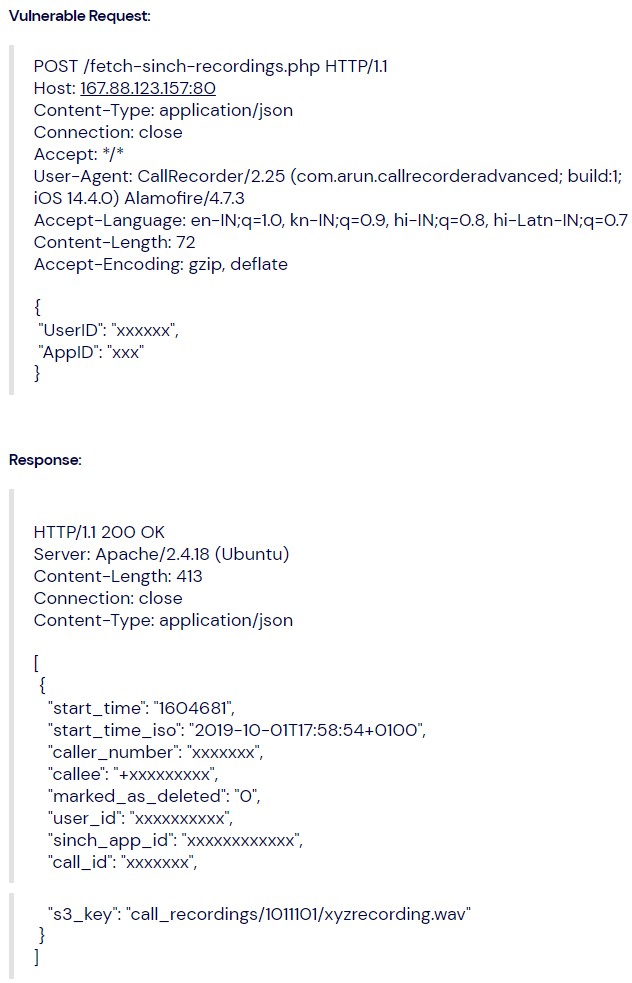
The popular iOS app "Automatic Call Recorder" was plagued by an undiscovered bug that has resulted in the exposure of several thousands of user phone call conversations. The flaw was discovered by Indian security researcher Anand Prakash while he was casually performing a decompilation of the software package. There, he found that the S3 buckets, hostnames, and other sensitive details that should be at least obfuscated/encrypted could be seen by anyone who intercepts the app’s traffic.
This could open the way to send POST API requests to the right webpage and access any user’s recordings. For targeted access, one could use the UserID, or more comfortably, the victim’s phone number.
Using a proxy tool, an attacker could modify the network traffic that travels from and to the app, replacing their number with another person’s and accessing their recordings on their device. The proof of concept and the way to reproduce this is given below, although it won’t work anymore because the bug has been fixed.
The researcher reported his finding to TechCrunch’s Zack Whittaker, who helped reach out to the app’s developers and informed them about the leaking AWS bucket. While the issue has been fixed, there’s a good chance that malicious individuals discovered this before Prakash and that users have had their private conversations exposed.
The discovery happened on February 27, 2021, and the securing action took place on March 6, 2021. The total period of the exposure remains unknown right now, so it could be anything.
According to the researcher, just before it was eventually secured, the storage bucket held 300 GB, corresponding to about 130,000 audio recordings. The App Store doesn’t publish download data, but the developer claims that Automatic Call Recorder has over a million users.
There are 2,200 user reviews on the App Store, giving it an average rating of 4.4 out of 5. For a subscription-based model, this is a good score - and simultaneously, for a project that asks people to pay money for its services, the security lapse is even more demeaning.
If you are among the users of the particular app, we would advise you to treat your communications as compromised and be prepared to receive truthful and convincing phishing SMS.