Auto-Color RAT Exploits SAP NetWeaver Vulnerability in Stealthy Attacks
- First time: This is the first known use of Auto-Color via the SAP NetWeaver flaw, employing a new suppression technique.
- Targeting U.S. chemicals: A chemical company in the U.S. was targeted in a multi-stage attack involving this malware.
- Alarming evolution: Auto-Color, previously seen targeting universities and government entities, has hit critical infrastructure via a U.S. chemical company.
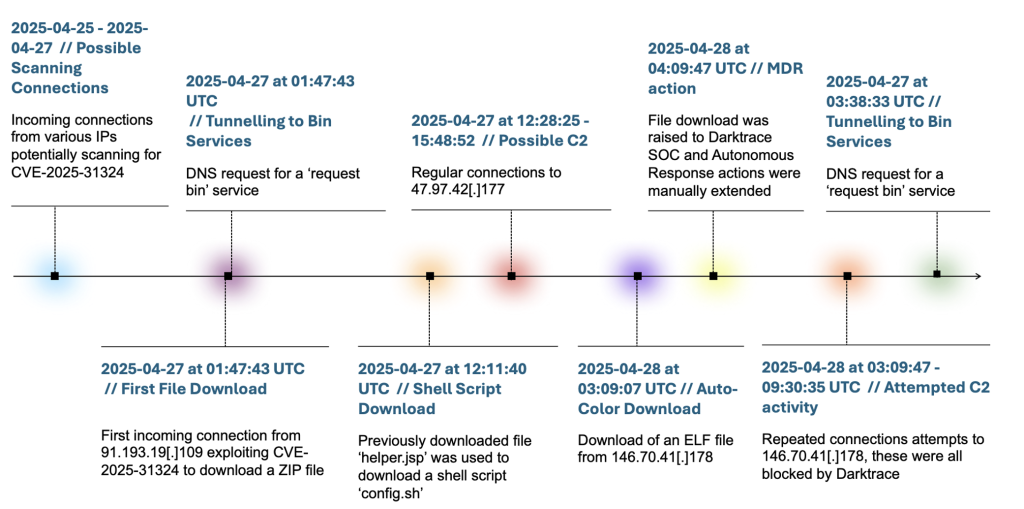
Threat actors are leveraging the critical CVE-2025-31324 vulnerability in SAP NetWeaver systems to deploy a stealthy Linux backdoor malware named Auto-Color. When unable to communicate with the attacker infrastructure, the RAT can appear dormant, making it harder to detect.
Exploiting CVE-2025-31324
Disclosed in April 2025, CVE-2025-31324 is a vulnerability within SAP NetWeaver that allows unauthenticated attackers to upload files, enabling remote code execution. Exploitation provides adversaries full system control, making it an appealing target for persistent network infiltration.
Darktrace reports that the vulnerability is being actively exploited in the wild despite available patches.
Tactics of Auto-Color Malware
A new Darktrace analysis reveals that Auto-Color, a Linux-based Remote Access Trojan (RAT), demonstrates advanced evasion techniques. Upon execution, it renames itself to "auto-color" and uses ld.so.preload for stealth and persistence, ensuring its malicious library loads before legitimate ones.
It enhances its evasiveness by incorporating a 'sleep/delay' mechanism when unable to connect to its command-and-control (C2) server, which makes it appear dormant. This suppression enables it to bypass analysis environments, such as sandboxes.
Additionally, proprietary, custom encryption algorithms secure its C2 communications, and IP addresses are often dynamically generated and stored in temporary files.
In April, Auto-Color was observed for the first time targeting critical infrastructure in an attack on a U.S.-based chemicals company.
Implications and Mitigation
The 2025 cybersecurity threat highlights the persistent risks of unpatched critical systems. Organizations must prioritize robust patch management, implement advanced detection systems, and enforce network segmentation to mitigate risks posed by Linux backdoor malware like Auto-Color.
Jason Soroko, Senior Fellow at Sectigo, said, “Security teams should confirm every SAP NetWeaver instance is fully patched or that the Metadata Uploader is disabled and shielded behind strong access controls. Restrict inbound traffic to the application only from trusted networks and apply egress filtering that blocks unknown TLS destinations so Auto Color cannot reach its operators.”
He further advised, “Proactively hunt for evidence of exploitation such as requests to /developmentserver/metadatauploader the presence of helper.jsp or config.sh unexpected ZIP uploads modifications to /etc/ld.so.preload creation of libcext.so.2 or any file under /var/log/cross named auto color and outbound traffic to suspicious IPs over ports 443 or 3232."
Soroko also recommended the containment steps, stating, "Prepare containment playbooks that include host isolation credential rotation and rapid rebuild of affected systems and add network detection rules for these indicators so the organization can prove it has closed exposure.”
Organizations must implement SELinux policies to prevent unauthorized modifications, as advised by Mayuresh Dani, Security Research Manager at Qualys.
“Eliminate privilege escalation vectors by enforcing least privilege access methods and kernel hardening settings,” Dani said, further recommending to “deploy AppArmor or SELinux mandatory access controls to restrict process capabilities and prevent unauthorized system modifications.”
Darktrace suggested the use of AI-powered autonomous response and AI-powered or behavioral anomaly detection tools that can identify subtle deviations from normal network activity, regardless of known signatures.