New Astaroth Trojan Can Bypass Antivirus Software Services
- A new variant of the Astaroth trojan has been spotted in the wild in Europe and Brazil.
- The trojan is distributed through phishing campaigns and hides in image and extension-less files.
- Astaroth is also capable of tricking antivirus programs into ignoring any malicious activity.
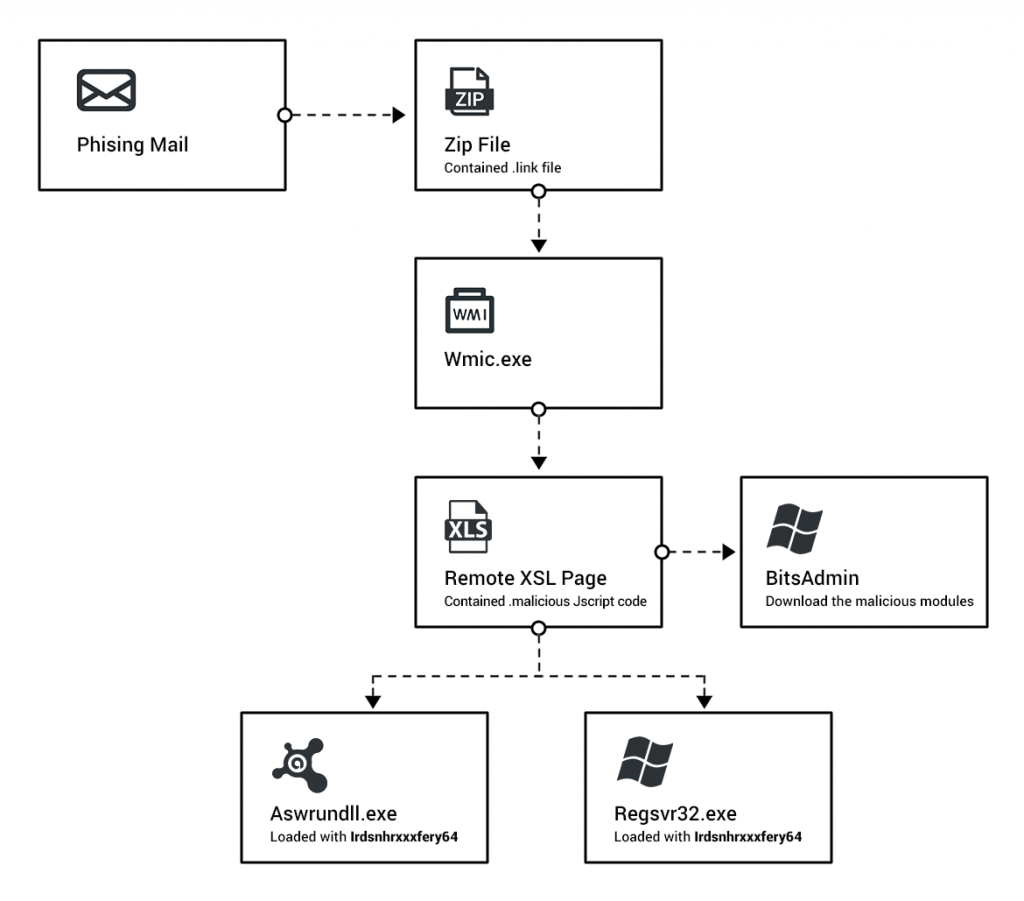
According to a report published by Cybereason's Nocturnus Research team, a new instance of the Astaroth trojan has been seen in the wild that is capable of stealing user credentials by exploiting antivirus software. The trojan is currently being used in spam campaigns throughout Europe and Brazil, and thousands of infections have been recorded towards the end of last year.
The Astaroth trojan disguises itself in JPEG, GIF or even extension-free files to avoid being detected by antivirus software. Once a user downloads the infected file from a phishing campaign, Microsoft’s BITSAdmin tool is used to download the payload which is then injected, and a connection to the C2 server is made.
Image Courtesy of Cybereason
According to Cybereason "As we enter 2019, we anticipate that the using of WMIC and other LOLbins will increase. Because of the great potential for malicious exploitation inherent in the use of LOLbins, it is very likely that many other information stealers will adopt this method to deliver their payload into targeted machines."
Once the Astaroth trojan is injected into a user system, an XSL script built using obfuscated code is launched. The script manages to hide from antivirus software. This is not the first time the trojan has been seen in the wild, but the older variations were not as effective. Previous iterations of the malware would simply quit if they detected any antivirus programs installed on target PCs.
In the modern iteration of Astaroth, the trojan tries to detect antivirus programs, and their executables are tricked into ignoring the malicious activity. The trojan was originally discovered in 2017, and it has kept evolving ever since. Outside of establishing a C2 server to attackers, the malicious program is also capable of intercepting calls, logging keyboard activity, and terminating applications.
What do you think about the Astaroth trojan? Let us know in the comments below. Don’t forget to join discussions on this or other topics on our socials, on Facebook and Twitter.